Understanding Blob-Carrying Transactions in Blockchain Sharding
Blockchain technology has revolutionized the way digital assets and data are transferred, stored, and verified. As the popularity of blockchain networks grows, so does the need for scalable solutions that can handle increasing transaction volumes without compromising security or decentralization. One promising approach to achieving this scalability is through sharding, a technique that divides a blockchain network into smaller, manageable segments called shards. Within this framework, blob-carrying transactions have emerged as an innovative method to optimize data processing and improve overall network efficiency.
What Are Blob-Carrying Transactions?
Blob-carrying transactions are specialized data structures designed to facilitate efficient transaction processing within sharded blockchain networks. Unlike traditional transactions that are verified individually by each node across the entire network, blob-carrying transactions package multiple small transactions into a single large "blob." This blob acts as a container holding numerous individual operations or data points.
The primary purpose of these blobs is to reduce verification overhead on individual nodes. Instead of verifying each small transaction separately—which can be time-consuming and resource-intensive—nodes verify larger blobs containing many transactions at once. This process significantly decreases latency and increases throughput, enabling the network to handle more users and higher transaction volumes without sacrificing security.
How Do Blob-Carrying Transactions Enhance Blockchain Scalability?
In traditional blockchain systems like Bitcoin or early versions of Ethereum, every node must validate every transaction directly. While this ensures high security levels through full validation, it also limits scalability because nodes become bottlenecks under heavy loads.
Sharding addresses this issue by dividing the network into smaller segments—each shard processes its own subset of transactions independently. However, managing communication between shards introduces complexity; verifying cross-shard interactions efficiently becomes challenging.
Blob-carrying transactions help mitigate these challenges by:
- Reducing Verification Load: By bundling multiple small transactions into one blob per shard, nodes only need to verify fewer large data structures instead of numerous tiny ones.
- Streamlining Data Transfer: Blobs simplify cross-shard communication since they encapsulate multiple operations in a single package.
- Improving Network Throughput: With less verification overhead per node and optimized data handling within shards, overall transaction processing speeds increase dramatically.
This approach aligns with modern demands for high-performance blockchains capable of supporting decentralized applications (dApps), DeFi platforms, NFTs marketplaces—and other use cases requiring rapid confirmation times at scale.
Recent Advances in Sharding Using Blob-Carrying Transactions
Blockchain projects worldwide have been actively exploring sharding techniques incorporating blob-based methods:
Ethereum 2.0's Sharding Implementation: Ethereum's transition from proof-of-work (PoW) to proof-of-stake (PoS) includes extensive sharding plans aimed at scaling its ecosystem sustainably. The Beacon Chain launched in December 2020 laid groundwork for future shard chains.
In September 2022, Ethereum activated its first phase of full sharding with the Shanghai hard fork—introducing parallel processing capabilities via shard chains that utilize blob-like structures for efficient validation.
Polkadot’s Interoperability Focus: Polkadot employs parachains—independent blockchains connected via relay chains—to facilitate seamless asset transfer across different networks.
Its architecture leverages sharded design principles where blobs enable quick cross-chain messaging while maintaining security guarantees.
Solana’s High Throughput Model: Solana adopts unique consensus mechanisms combining Proof-of-History (PoH) with Proof-of-Stake (PoS). It processes thousands of transactions per second using parallel execution similar to sharding concepts but optimized through innovative data structuring akin to blobs for batch validation purposes.
These developments demonstrate how integrating blob-like transactional models within sharded architectures can significantly enhance performance metrics such as throughput and latency while maintaining robust security standards essential for mainstream adoption.
Challenges Associated With Blob-Based Sharded Networks
Despite their advantages, implementing blob-carrying transactions within sharded systems presents several hurdles:
Security Concerns:
- Ensuring each shard remains secure against malicious actors is critical; if one shard becomes compromised due to inadequate validation protocols on blobs or faulty aggregation methods — it could threaten overall network integrity.
Interoperability Complexities:
- Facilitating smooth communication between different shards—or even disparate blockchains—is complex when relying on bundled transactional data like blobs because synchronization issues may arise if not managed properly.
User Experience Variability:
- As different shards may process batches differently or experience varying load levels during peak times—a user might notice inconsistent confirmation times depending on which part of the network their transaction interacts with.
Regulatory Considerations:
- As blockchain adoption expands into regulated sectors such as finance or healthcare—with strict compliance requirements—the design choices around batching mechanisms like blobs must align with legal standards concerning transparency and auditability.
Addressing these challenges requires ongoing research focused on enhancing cryptographic proofs associated with batch validations while developing standardized protocols ensuring interoperability without sacrificing decentralization principles.
The Future Role Of Blob-Carrying Transactions in Blockchain Ecosystems
As blockchain technology continues evolving towards greater scalability solutions—including Layer 2 rollups and other off-chain methods—blob-based approaches will likely remain integral components within broader architectural frameworks aimed at optimizing performance without compromising trustlessness or censorship resistance.
Furthermore:
- They will play vital roles in enabling real-time applications such as decentralized exchanges (DEXs), gaming platforms requiring rapid state updates,
- Supporting enterprise-grade solutions where high throughput combined with privacy-preserving features is necessary,
- And facilitating interoperability initiatives among diverse ecosystems aiming toward unified multi-chain environments.
By improving how large datasets are packaged and validated efficiently across distributed ledgers—a core function served by blob-carrying transactions—they contribute substantially toward realizing scalable decentralized infrastructures suitable for mainstream adoption.
Key Takeaways About Blob-Carrying Transactions
To summarize:
- They bundle multiple small operations into larger "blobs" reducing verification overhead,
- Play an essential role in scaling efforts like Ethereum's upcoming upgrades,
- Enable faster cross-shard communication crucial for complex dApps,
- Present ongoing challenges related to security assurance & interoperability,
- Will continue shaping future multi-chain ecosystems aiming for high performance alongside robust decentralization standards.
Understanding how these advanced transactional techniques fit within broader scaling strategies provides valuable insights into building resilient yet efficient blockchain networks capable of supporting tomorrow’s digital economy needs.
Keywords & Semantic Terms Used:
Blockchain scalability | Sharded blockchain | Transaction batching | Cross-shard communication | Ethereum 2.0 | Polkadot parachains | Solana throughput | Distributed ledger technology | Decentralized applications (dApps) | Blockchain interoperability


kai
2025-05-14 12:35
What role do blob-carrying transactions play in sharding?
Understanding Blob-Carrying Transactions in Blockchain Sharding
Blockchain technology has revolutionized the way digital assets and data are transferred, stored, and verified. As the popularity of blockchain networks grows, so does the need for scalable solutions that can handle increasing transaction volumes without compromising security or decentralization. One promising approach to achieving this scalability is through sharding, a technique that divides a blockchain network into smaller, manageable segments called shards. Within this framework, blob-carrying transactions have emerged as an innovative method to optimize data processing and improve overall network efficiency.
What Are Blob-Carrying Transactions?
Blob-carrying transactions are specialized data structures designed to facilitate efficient transaction processing within sharded blockchain networks. Unlike traditional transactions that are verified individually by each node across the entire network, blob-carrying transactions package multiple small transactions into a single large "blob." This blob acts as a container holding numerous individual operations or data points.
The primary purpose of these blobs is to reduce verification overhead on individual nodes. Instead of verifying each small transaction separately—which can be time-consuming and resource-intensive—nodes verify larger blobs containing many transactions at once. This process significantly decreases latency and increases throughput, enabling the network to handle more users and higher transaction volumes without sacrificing security.
How Do Blob-Carrying Transactions Enhance Blockchain Scalability?
In traditional blockchain systems like Bitcoin or early versions of Ethereum, every node must validate every transaction directly. While this ensures high security levels through full validation, it also limits scalability because nodes become bottlenecks under heavy loads.
Sharding addresses this issue by dividing the network into smaller segments—each shard processes its own subset of transactions independently. However, managing communication between shards introduces complexity; verifying cross-shard interactions efficiently becomes challenging.
Blob-carrying transactions help mitigate these challenges by:
- Reducing Verification Load: By bundling multiple small transactions into one blob per shard, nodes only need to verify fewer large data structures instead of numerous tiny ones.
- Streamlining Data Transfer: Blobs simplify cross-shard communication since they encapsulate multiple operations in a single package.
- Improving Network Throughput: With less verification overhead per node and optimized data handling within shards, overall transaction processing speeds increase dramatically.
This approach aligns with modern demands for high-performance blockchains capable of supporting decentralized applications (dApps), DeFi platforms, NFTs marketplaces—and other use cases requiring rapid confirmation times at scale.
Recent Advances in Sharding Using Blob-Carrying Transactions
Blockchain projects worldwide have been actively exploring sharding techniques incorporating blob-based methods:
Ethereum 2.0's Sharding Implementation: Ethereum's transition from proof-of-work (PoW) to proof-of-stake (PoS) includes extensive sharding plans aimed at scaling its ecosystem sustainably. The Beacon Chain launched in December 2020 laid groundwork for future shard chains.
In September 2022, Ethereum activated its first phase of full sharding with the Shanghai hard fork—introducing parallel processing capabilities via shard chains that utilize blob-like structures for efficient validation.
Polkadot’s Interoperability Focus: Polkadot employs parachains—independent blockchains connected via relay chains—to facilitate seamless asset transfer across different networks.
Its architecture leverages sharded design principles where blobs enable quick cross-chain messaging while maintaining security guarantees.
Solana’s High Throughput Model: Solana adopts unique consensus mechanisms combining Proof-of-History (PoH) with Proof-of-Stake (PoS). It processes thousands of transactions per second using parallel execution similar to sharding concepts but optimized through innovative data structuring akin to blobs for batch validation purposes.
These developments demonstrate how integrating blob-like transactional models within sharded architectures can significantly enhance performance metrics such as throughput and latency while maintaining robust security standards essential for mainstream adoption.
Challenges Associated With Blob-Based Sharded Networks
Despite their advantages, implementing blob-carrying transactions within sharded systems presents several hurdles:
Security Concerns:
- Ensuring each shard remains secure against malicious actors is critical; if one shard becomes compromised due to inadequate validation protocols on blobs or faulty aggregation methods — it could threaten overall network integrity.
Interoperability Complexities:
- Facilitating smooth communication between different shards—or even disparate blockchains—is complex when relying on bundled transactional data like blobs because synchronization issues may arise if not managed properly.
User Experience Variability:
- As different shards may process batches differently or experience varying load levels during peak times—a user might notice inconsistent confirmation times depending on which part of the network their transaction interacts with.
Regulatory Considerations:
- As blockchain adoption expands into regulated sectors such as finance or healthcare—with strict compliance requirements—the design choices around batching mechanisms like blobs must align with legal standards concerning transparency and auditability.
Addressing these challenges requires ongoing research focused on enhancing cryptographic proofs associated with batch validations while developing standardized protocols ensuring interoperability without sacrificing decentralization principles.
The Future Role Of Blob-Carrying Transactions in Blockchain Ecosystems
As blockchain technology continues evolving towards greater scalability solutions—including Layer 2 rollups and other off-chain methods—blob-based approaches will likely remain integral components within broader architectural frameworks aimed at optimizing performance without compromising trustlessness or censorship resistance.
Furthermore:
- They will play vital roles in enabling real-time applications such as decentralized exchanges (DEXs), gaming platforms requiring rapid state updates,
- Supporting enterprise-grade solutions where high throughput combined with privacy-preserving features is necessary,
- And facilitating interoperability initiatives among diverse ecosystems aiming toward unified multi-chain environments.
By improving how large datasets are packaged and validated efficiently across distributed ledgers—a core function served by blob-carrying transactions—they contribute substantially toward realizing scalable decentralized infrastructures suitable for mainstream adoption.
Key Takeaways About Blob-Carrying Transactions
To summarize:
- They bundle multiple small operations into larger "blobs" reducing verification overhead,
- Play an essential role in scaling efforts like Ethereum's upcoming upgrades,
- Enable faster cross-shard communication crucial for complex dApps,
- Present ongoing challenges related to security assurance & interoperability,
- Will continue shaping future multi-chain ecosystems aiming for high performance alongside robust decentralization standards.
Understanding how these advanced transactional techniques fit within broader scaling strategies provides valuable insights into building resilient yet efficient blockchain networks capable of supporting tomorrow’s digital economy needs.
Keywords & Semantic Terms Used:
Blockchain scalability | Sharded blockchain | Transaction batching | Cross-shard communication | Ethereum 2.0 | Polkadot parachains | Solana throughput | Distributed ledger technology | Decentralized applications (dApps) | Blockchain interoperability
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
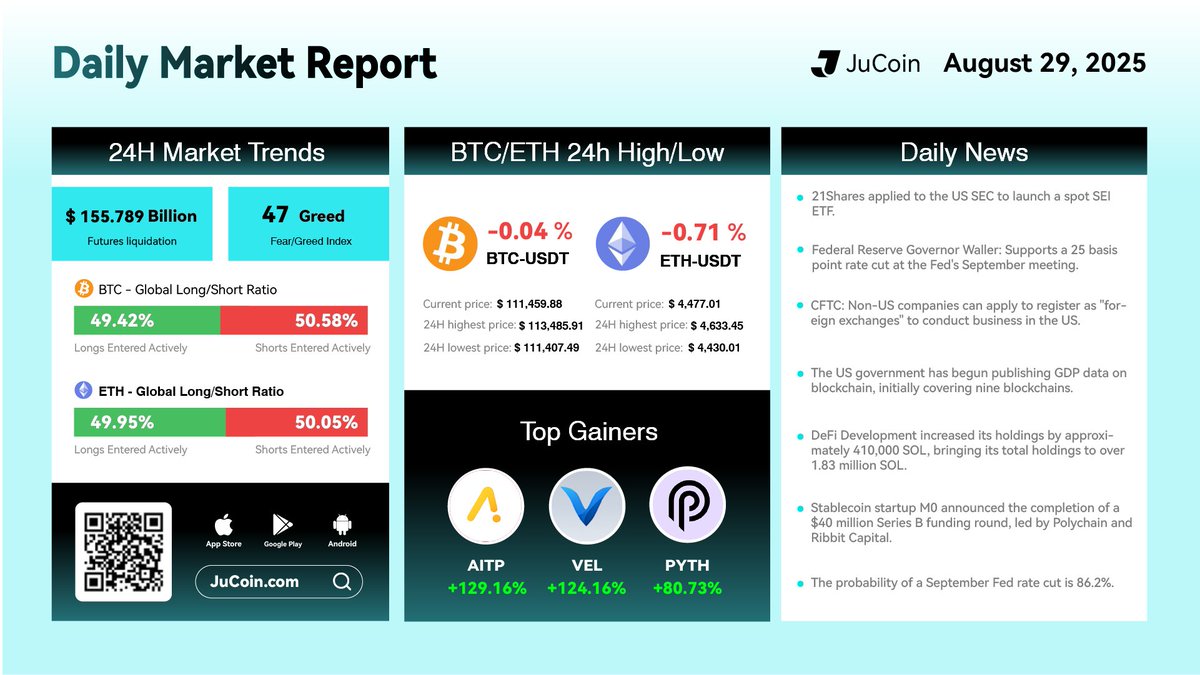
Today’s Top Gainers:
$AITP/USDT: 129%
$VEL/USDT: 124%$PYTH/USDT : 80%
$JU Token is close to reach $22 a new ATH
#cryptocurrency #blockchain #finance

Mrconfamm
2025-08-29 07:37
Market Daily Report
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
💰 Jusqu’à 200 USDT / mois pour les créateurs crypto + un partenariat long terme garanti.
Si tu es crypto creator, influenceur ou content maker Web3, c’est TON moment d’entrer dans la cour des grands.
🎯 Pourquoi rejoindre ?
✔️ Cash rewards mensuels → pas d’attente, tu encaisses tous les mois ✔️ Partenariat premium → top 10 créateurs = Gold Creator Channel ✔️ Visibilité boostée → ton contenu poussé via les canaux officiels ✔️ Stabilité & croissance → revenus fixes, events exclusifs, collabs écosystème
🏆 Récompenses mensuelles : 1️⃣ 1st place → 200 USDT 2️⃣ 2nd–5th → 100 USDT chacun 3️⃣ 6th–10th → 50 USDT chacun ✨ Bonus newcomer → 10 USDT dès les tâches test réussies
🛠️ Comment ça marche ?
1️⃣ Inscris-toi (2–7 septembre) 2️⃣ 21 jours → crée 15 contenus originaux autour de JuCoin 3️⃣ Ton contenu est évalué (originalité, impact, engagement) 4️⃣ Gagne tes USDT + ton badge Gold Creator ✨
👉 Peu importe ton style (vidéo, thread, visuel, analyse), tant que c’est crypto + JuCoin, tu peux briller.
🔥 Low barrier, high rewards. Même un débutant bien guidé peut devenir un Gold Creator.
📌 Formulaire en ligne dispo dès le 2 septembre via le site JuCoin, Twitter & Telegram.
✨ Rejoins Ju Square maintenant et transforme ton talent en revenus réguliers.
La création crypto n’attend plus : tu crées, tu gagnes.
#JuSquare #CryptoCreators #Web3Community #cryptocurrency #blockchain



Carmelita
2025-09-02 18:43
Ju Square Creator Partnership Program est OFFICIELLEMENT lancé !
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
What Is Sharding in Blockchain?
Sharding is a transformative scalability solution designed to enhance the performance and efficiency of blockchain networks. As blockchain technology gains widespread adoption, the need to process increasing numbers of transactions quickly and securely becomes critical. Sharding addresses this challenge by dividing the entire network into smaller, manageable segments called shards, each capable of processing transactions independently. This division allows multiple transactions to be processed simultaneously, significantly reducing congestion and improving overall throughput.
In essence, sharding enables a blockchain network to operate more like a distributed database rather than a single monolithic ledger. Each shard functions as its own mini-blockchain with its unique state and transaction history but remains interconnected within the larger network framework. This structure not only boosts transaction speeds but also helps in scaling blockchain solutions for real-world applications such as decentralized finance (DeFi), supply chain management, and enterprise solutions.
How Does Sharding Work in Blockchain Networks?
The core idea behind sharding involves splitting the workload across various smaller components—shards—that work concurrently. Each shard processes a subset of all transactions based on specific criteria such as user accounts or data types. For example, one shard might handle payment transactions while another manages smart contract interactions.
To maintain consistency across these independent shards, mechanisms like cross-shard communication are implemented. These protocols ensure that when users perform transactions involving multiple shards—say transferring assets from one account managed by one shard to another managed by different shards—the system can verify and record these operations accurately without compromising security or integrity.
Shards typically operate as separate blockchains known as "shard chains." They maintain their own states—such as account balances or smart contract data—and process their designated set of transactions independently before periodically syncing with other shards through consensus protocols designed for cross-shard validation.
Types of Sharding
There are primarily two types of sharding used in blockchain systems:
Horizontal Sharding: This approach divides the network based on transaction types or user groups—for instance, separating payment processing from smart contract execution.
Vertical Sharding: Here, data is partitioned based on storage needs or data categories—for example, storing different kinds of information (user profiles vs transactional logs) separately across various shards.
Both methods aim to optimize resource utilization while maintaining security and decentralization principles inherent in blockchain technology.
Benefits of Implementing Sharding
Implementing sharding offers several significant advantages:
Enhanced Scalability: By distributing transaction loads across multiple shards, networks can handle many more operations per second compared to traditional single-chain architectures.
Reduced Transaction Fees: Faster processing times mean less congestion; consequently, users often experience lower fees during peak usage periods.
Improved Network Efficiency: Smaller nodes manage fewer tasks within each shard—they require less computational power and storage capacity—making participation easier for more validators.
Parallel Processing: Multiple parts of the network work simultaneously rather than sequentially; this parallelism accelerates overall throughput significantly.
These benefits make sharded blockchains suitable for large-scale applications where high speed and low latency are essential requirements.
Challenges Associated With Blockchain Sharding
Despite its promising potential, implementing sharding introduces complex technical challenges that must be addressed:
Inter-Shard Communication
Ensuring seamless communication between different shards is vital yet difficult. Transactions involving multiple shards require secure protocols that prevent double-spending or inconsistencies—a problem known as cross-shard communication complexity.
Consensus Mechanisms Across Multiple Shards
Traditional consensus algorithms like Proof-of-Work (PoW) are not inherently designed for multi-shard environments. Developing efficient consensus models that work reliably across numerous independent chains remains an ongoing research area within blockchain development communities.
Security Concerns
Dividing a network into smaller segments increases vulnerability risks; if one shard becomes compromised due to an attack or bug exploitation—a scenario called "shard takeover"—it could threaten the entire ecosystem's security integrity unless robust safeguards are implemented effectively throughout all parts of the system.
Standardization & Adoption Barriers
For widespread adoption beyond experimental phases requires industry-wide standards governing how sharded networks communicate and interoperate seamlessly. Without standardization efforts among developers and stakeholders worldwide—including major platforms like Ethereum—the risk exists that fragmentation could hinder progress rather than accelerate it.
Recent Developments in Blockchain Sharding Technology
Major projects have made notable strides toward integrating sharding into their ecosystems:
Ethereum 2.0 has been at the forefront with plans for scalable upgrades through its phased rollout strategy involving beacon chains (launched December 2020). The next steps include deploying dedicated shard chains alongside cross-shard communication protocols aimed at enabling Ethereum’s massive ecosystem to scale efficiently without sacrificing decentralization or security standards.
Polkadot employs relay chains connecting parachains—independent blockchains optimized for specific use cases—that communicate via shared security models facilitating interoperability among diverse networks.
Cosmos, utilizing Tendermint Core consensus algorithm architecture allows developers to create zones (independent blockchains) capable of interoperation within an overarching hub-and-spoke model similar to Polkadot’s relay chain approach.
Research continues globally exploring innovative techniques such as state sharding, which aims at optimizing how state information is stored across nodes—a crucial factor influencing scalability limits further improvements.
Potential Risks Impacting Future Adoption
While promising solutions exist today—and ongoing research promises even better approaches—the path forward faces hurdles related mainly to:
Security Risks: Smaller individual shards may become targets due to reduced validation power compared with full nodes operating on entire networks.
Interoperability Challenges: Achieving flawless interaction between diverse systems requires standardized protocols; otherwise fragmentation may occur leading toward isolated ecosystems instead of unified platforms.
Adoption Hurdles & Industry Standardization
Without broad agreement on technical standards governing cross-shard communications—as well as regulatory considerations—widespread deployment might slow down considerably despite technological readiness.
Understanding How Blockchain Scaling Evolves Through Sharding
As demand grows exponentially—from DeFi applications demanding rapid trades versus enterprise-level integrations requiring high throughput—the importance lies not just in creating faster blockchains but ensuring they remain secure against evolving threats while interoperable enough for global adoption.
By addressing current limitations through continuous innovation—in protocol design improvements like state sharing techniques—and fostering collaboration among industry leaders worldwide who develop open standards —the future landscape looks promising: scalable yet secure decentralized systems capable enough for mainstream use.
This comprehensive overview provides clarity about what sharding entails within blockchain technology: how it works technically; why it matters; what benefits it offers; what challenges lie ahead; along with recent advancements shaping its future trajectory—all aligned towards helping users understand both foundational concepts and cutting-edge developments effectively.


Lo
2025-05-15 02:38
What is sharding in blockchain?
What Is Sharding in Blockchain?
Sharding is a transformative scalability solution designed to enhance the performance and efficiency of blockchain networks. As blockchain technology gains widespread adoption, the need to process increasing numbers of transactions quickly and securely becomes critical. Sharding addresses this challenge by dividing the entire network into smaller, manageable segments called shards, each capable of processing transactions independently. This division allows multiple transactions to be processed simultaneously, significantly reducing congestion and improving overall throughput.
In essence, sharding enables a blockchain network to operate more like a distributed database rather than a single monolithic ledger. Each shard functions as its own mini-blockchain with its unique state and transaction history but remains interconnected within the larger network framework. This structure not only boosts transaction speeds but also helps in scaling blockchain solutions for real-world applications such as decentralized finance (DeFi), supply chain management, and enterprise solutions.
How Does Sharding Work in Blockchain Networks?
The core idea behind sharding involves splitting the workload across various smaller components—shards—that work concurrently. Each shard processes a subset of all transactions based on specific criteria such as user accounts or data types. For example, one shard might handle payment transactions while another manages smart contract interactions.
To maintain consistency across these independent shards, mechanisms like cross-shard communication are implemented. These protocols ensure that when users perform transactions involving multiple shards—say transferring assets from one account managed by one shard to another managed by different shards—the system can verify and record these operations accurately without compromising security or integrity.
Shards typically operate as separate blockchains known as "shard chains." They maintain their own states—such as account balances or smart contract data—and process their designated set of transactions independently before periodically syncing with other shards through consensus protocols designed for cross-shard validation.
Types of Sharding
There are primarily two types of sharding used in blockchain systems:
Horizontal Sharding: This approach divides the network based on transaction types or user groups—for instance, separating payment processing from smart contract execution.
Vertical Sharding: Here, data is partitioned based on storage needs or data categories—for example, storing different kinds of information (user profiles vs transactional logs) separately across various shards.
Both methods aim to optimize resource utilization while maintaining security and decentralization principles inherent in blockchain technology.
Benefits of Implementing Sharding
Implementing sharding offers several significant advantages:
Enhanced Scalability: By distributing transaction loads across multiple shards, networks can handle many more operations per second compared to traditional single-chain architectures.
Reduced Transaction Fees: Faster processing times mean less congestion; consequently, users often experience lower fees during peak usage periods.
Improved Network Efficiency: Smaller nodes manage fewer tasks within each shard—they require less computational power and storage capacity—making participation easier for more validators.
Parallel Processing: Multiple parts of the network work simultaneously rather than sequentially; this parallelism accelerates overall throughput significantly.
These benefits make sharded blockchains suitable for large-scale applications where high speed and low latency are essential requirements.
Challenges Associated With Blockchain Sharding
Despite its promising potential, implementing sharding introduces complex technical challenges that must be addressed:
Inter-Shard Communication
Ensuring seamless communication between different shards is vital yet difficult. Transactions involving multiple shards require secure protocols that prevent double-spending or inconsistencies—a problem known as cross-shard communication complexity.
Consensus Mechanisms Across Multiple Shards
Traditional consensus algorithms like Proof-of-Work (PoW) are not inherently designed for multi-shard environments. Developing efficient consensus models that work reliably across numerous independent chains remains an ongoing research area within blockchain development communities.
Security Concerns
Dividing a network into smaller segments increases vulnerability risks; if one shard becomes compromised due to an attack or bug exploitation—a scenario called "shard takeover"—it could threaten the entire ecosystem's security integrity unless robust safeguards are implemented effectively throughout all parts of the system.
Standardization & Adoption Barriers
For widespread adoption beyond experimental phases requires industry-wide standards governing how sharded networks communicate and interoperate seamlessly. Without standardization efforts among developers and stakeholders worldwide—including major platforms like Ethereum—the risk exists that fragmentation could hinder progress rather than accelerate it.
Recent Developments in Blockchain Sharding Technology
Major projects have made notable strides toward integrating sharding into their ecosystems:
Ethereum 2.0 has been at the forefront with plans for scalable upgrades through its phased rollout strategy involving beacon chains (launched December 2020). The next steps include deploying dedicated shard chains alongside cross-shard communication protocols aimed at enabling Ethereum’s massive ecosystem to scale efficiently without sacrificing decentralization or security standards.
Polkadot employs relay chains connecting parachains—independent blockchains optimized for specific use cases—that communicate via shared security models facilitating interoperability among diverse networks.
Cosmos, utilizing Tendermint Core consensus algorithm architecture allows developers to create zones (independent blockchains) capable of interoperation within an overarching hub-and-spoke model similar to Polkadot’s relay chain approach.
Research continues globally exploring innovative techniques such as state sharding, which aims at optimizing how state information is stored across nodes—a crucial factor influencing scalability limits further improvements.
Potential Risks Impacting Future Adoption
While promising solutions exist today—and ongoing research promises even better approaches—the path forward faces hurdles related mainly to:
Security Risks: Smaller individual shards may become targets due to reduced validation power compared with full nodes operating on entire networks.
Interoperability Challenges: Achieving flawless interaction between diverse systems requires standardized protocols; otherwise fragmentation may occur leading toward isolated ecosystems instead of unified platforms.
Adoption Hurdles & Industry Standardization
Without broad agreement on technical standards governing cross-shard communications—as well as regulatory considerations—widespread deployment might slow down considerably despite technological readiness.
Understanding How Blockchain Scaling Evolves Through Sharding
As demand grows exponentially—from DeFi applications demanding rapid trades versus enterprise-level integrations requiring high throughput—the importance lies not just in creating faster blockchains but ensuring they remain secure against evolving threats while interoperable enough for global adoption.
By addressing current limitations through continuous innovation—in protocol design improvements like state sharing techniques—and fostering collaboration among industry leaders worldwide who develop open standards —the future landscape looks promising: scalable yet secure decentralized systems capable enough for mainstream use.
This comprehensive overview provides clarity about what sharding entails within blockchain technology: how it works technically; why it matters; what benefits it offers; what challenges lie ahead; along with recent advancements shaping its future trajectory—all aligned towards helping users understand both foundational concepts and cutting-edge developments effectively.
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
What Is a Vesting Schedule for Tokens?
Understanding the concept of a vesting schedule is essential for anyone involved in cryptocurrency projects, whether as an investor, developer, or stakeholder. At its core, a vesting schedule is a structured plan that determines how and when tokens are released to recipients over time. This mechanism plays a vital role in ensuring fair distribution, maintaining market stability, and aligning stakeholders’ interests with the long-term success of the project.
Why Token Vesting Matters in Blockchain Projects
Token vesting is more than just a technical detail; it’s a strategic tool used by blockchain projects to manage token supply and foster trust among investors and team members. When tokens are distributed without restrictions or schedules, it can lead to sudden sell-offs that destabilize the market or create perceptions of unfairness. Implementing vesting schedules helps mitigate these risks by controlling how quickly tokens enter circulation.
For investors and project teams alike, understanding how vesting works provides clarity on token availability and potential influence on market dynamics. It also demonstrates transparency from project developers—an important factor for regulatory compliance and building confidence within the community.
Types of Vesting Schedules
There are several common types of vesting schedules used across blockchain projects:
Linear Vesting: Tokens are gradually released at consistent intervals over the entire vesting period. For example, if 1 million tokens are vested over four years with monthly releases, approximately 20,833 tokens would be unlocked each month.
Cliff Vesting: A specific initial period (the "cliff") must pass before any tokens become available. After this cliff period—say six months—the remaining tokens start to unlock gradually or all at once.
Accelerated Vesting: Under certain conditions such as achieving milestones or during specific events like acquisitions or mergers, token release speeds up significantly compared to standard schedules.
These structures serve different strategic purposes: linear vestings promote steady engagement; cliffs protect early-stage projects from immediate sell-offs; accelerated options reward key achievements.
Key Components of Token Vesting Schedules
A typical vesting schedule incorporates several critical elements:
Vesting Period: The total duration over which tokens will be gradually released (e.g., 1 year, 4 years).
Cliff Period: An initial lock-up phase where no tokens are released until it ends (common durations range from three months to one year).
Release Intervals: The frequency at which vested tokens become accessible—monthly, quarterly, annually.
Vested Amounts: The portion of total allocated tokens that becomes available at each interval.
Some schedules include clawback provisions allowing projects to reclaim unvested tokens under certain circumstances—adding an extra layer of control but also complexity.
Regulatory Considerations for Token Vestings
As regulatory frameworks around cryptocurrencies evolve globally—and particularly within jurisdictions like the United States—the design of token vestings must adhere to legal standards. Agencies such as the SEC have issued guidance emphasizing transparency in token sales and distributions[1]. Properly structured vestings can help demonstrate compliance by showing that token allocations do not constitute unregistered securities offerings.
Projects should ensure theirvesting plans clearly specify timelines and conditions while avoiding practices that could be interpreted as manipulative or deceptive[5]. Transparent communication about these schedules builds trust among investors while reducing legal risks associated with non-compliance.
Recent Trends Enhancing Token Distribution Strategies
The industry has seen significant advancements in how vestings are implemented:
Use of smart contracts automates release processes based on predefined rules[3], increasing transparency and reducing manual errors.
Incorporation of performance metrics aligns token releases with project milestones rather than fixed timelines alone[2].
More sophisticated models now consider multiple factors such as team performance incentives alongside traditional time-based releases[2].
These innovations aim not only to improve fairness but also enhance stakeholder engagement by tying rewards directly to project achievements—a practice increasingly favored by regulators seeking accountability.
Risks Associated With Poorly Managed Vests
While well-designed schemes support healthy markets and stakeholder relations,poor management can have serious repercussions:
- Market Volatility:* If large amounts of vested tokens suddenly become available due to poorly planned schedules,it may flood exchanges causing price swings[4].
Legal Challenges: Non-compliance with jurisdictional regulations could lead to sanctions,legal action,or loss of credibility[5].
Stakeholder Distrust: Lackluster communication about unlocking timelines或 perceived unfairness might erode confidence,damaging long-term relationships within communities[6].
Therefore,careful planning combined with transparent disclosure is essential for safeguarding both project integrity和 investor interests。
How To Design an Effective Token Vestment Schedule
Creating an optimal schedule involves balancing multiple factors:
- Define clear goals:Determine whether your priority is long-term stability、team retention、or incentivizing milestones。
- Choose appropriate structure:Select between linear、cliff、or hybrid models based on your project's needs。
- Set realistic timelines:Align lock-up periods和 release intervals with development phases。
- Ensure regulatory compliance:Consult legal experts确保您的计划符合相关法律法规。
- Automate where possible:Utilize smart contracts来确保自动执行和透明度。
By carefully considering these aspects,你可以建立一个公平、安全且符合法规的vesting体系,为项目的持续成功奠定基础。
The Role Of Smart Contracts In Automating Vests
Smart contracts在现代区块链项目中扮演着关键角色。它们可以自动化token的释放过程,根据预设条件(如时间或达成特定目标)自动解锁tokens。这不仅提高了效率,还增强了透明度,因为所有操作都在区块链上公开记录,无需第三方干预。此外,这种自动化减少了人为错误和潜在的操控风险,使得整个vesting流程更加可信赖。
未来发展趋势显示,将智能合约与性能指标结合使用,将进一步优化token分发策略,实现更动态、更灵活的激励机制。这一技术进步也符合行业对安全性和合规性的不断追求,为投资者提供更有保障的环境。
References
1. SEC Guidance on Token Sales (2020)
2. Industry Trends in Vesting Schedules (2023)
3. Smart Contract-Based Vesting Schedules (2022)
4. Market Volatility Risks (2021)
5. Regulatory Risks in Token Distribution (2020)
6. Stakeholder Trust and Vesting Schedules (2022)
By understanding what a vestingat schedule entails—including its types、components、regulatory considerations以及最新行业趋势—you gain valuable insights into managing digital assets responsibly。 Whether you're developing new blockchain protocols或investors evaluating opportunities,这些知识都是确保安全、公平分配的重要基础。


kai
2025-05-14 08:42
What is a vesting schedule for tokens?
What Is a Vesting Schedule for Tokens?
Understanding the concept of a vesting schedule is essential for anyone involved in cryptocurrency projects, whether as an investor, developer, or stakeholder. At its core, a vesting schedule is a structured plan that determines how and when tokens are released to recipients over time. This mechanism plays a vital role in ensuring fair distribution, maintaining market stability, and aligning stakeholders’ interests with the long-term success of the project.
Why Token Vesting Matters in Blockchain Projects
Token vesting is more than just a technical detail; it’s a strategic tool used by blockchain projects to manage token supply and foster trust among investors and team members. When tokens are distributed without restrictions or schedules, it can lead to sudden sell-offs that destabilize the market or create perceptions of unfairness. Implementing vesting schedules helps mitigate these risks by controlling how quickly tokens enter circulation.
For investors and project teams alike, understanding how vesting works provides clarity on token availability and potential influence on market dynamics. It also demonstrates transparency from project developers—an important factor for regulatory compliance and building confidence within the community.
Types of Vesting Schedules
There are several common types of vesting schedules used across blockchain projects:
Linear Vesting: Tokens are gradually released at consistent intervals over the entire vesting period. For example, if 1 million tokens are vested over four years with monthly releases, approximately 20,833 tokens would be unlocked each month.
Cliff Vesting: A specific initial period (the "cliff") must pass before any tokens become available. After this cliff period—say six months—the remaining tokens start to unlock gradually or all at once.
Accelerated Vesting: Under certain conditions such as achieving milestones or during specific events like acquisitions or mergers, token release speeds up significantly compared to standard schedules.
These structures serve different strategic purposes: linear vestings promote steady engagement; cliffs protect early-stage projects from immediate sell-offs; accelerated options reward key achievements.
Key Components of Token Vesting Schedules
A typical vesting schedule incorporates several critical elements:
Vesting Period: The total duration over which tokens will be gradually released (e.g., 1 year, 4 years).
Cliff Period: An initial lock-up phase where no tokens are released until it ends (common durations range from three months to one year).
Release Intervals: The frequency at which vested tokens become accessible—monthly, quarterly, annually.
Vested Amounts: The portion of total allocated tokens that becomes available at each interval.
Some schedules include clawback provisions allowing projects to reclaim unvested tokens under certain circumstances—adding an extra layer of control but also complexity.
Regulatory Considerations for Token Vestings
As regulatory frameworks around cryptocurrencies evolve globally—and particularly within jurisdictions like the United States—the design of token vestings must adhere to legal standards. Agencies such as the SEC have issued guidance emphasizing transparency in token sales and distributions[1]. Properly structured vestings can help demonstrate compliance by showing that token allocations do not constitute unregistered securities offerings.
Projects should ensure theirvesting plans clearly specify timelines and conditions while avoiding practices that could be interpreted as manipulative or deceptive[5]. Transparent communication about these schedules builds trust among investors while reducing legal risks associated with non-compliance.
Recent Trends Enhancing Token Distribution Strategies
The industry has seen significant advancements in how vestings are implemented:
Use of smart contracts automates release processes based on predefined rules[3], increasing transparency and reducing manual errors.
Incorporation of performance metrics aligns token releases with project milestones rather than fixed timelines alone[2].
More sophisticated models now consider multiple factors such as team performance incentives alongside traditional time-based releases[2].
These innovations aim not only to improve fairness but also enhance stakeholder engagement by tying rewards directly to project achievements—a practice increasingly favored by regulators seeking accountability.
Risks Associated With Poorly Managed Vests
While well-designed schemes support healthy markets and stakeholder relations,poor management can have serious repercussions:
- Market Volatility:* If large amounts of vested tokens suddenly become available due to poorly planned schedules,it may flood exchanges causing price swings[4].
Legal Challenges: Non-compliance with jurisdictional regulations could lead to sanctions,legal action,or loss of credibility[5].
Stakeholder Distrust: Lackluster communication about unlocking timelines或 perceived unfairness might erode confidence,damaging long-term relationships within communities[6].
Therefore,careful planning combined with transparent disclosure is essential for safeguarding both project integrity和 investor interests。
How To Design an Effective Token Vestment Schedule
Creating an optimal schedule involves balancing multiple factors:
- Define clear goals:Determine whether your priority is long-term stability、team retention、or incentivizing milestones。
- Choose appropriate structure:Select between linear、cliff、or hybrid models based on your project's needs。
- Set realistic timelines:Align lock-up periods和 release intervals with development phases。
- Ensure regulatory compliance:Consult legal experts确保您的计划符合相关法律法规。
- Automate where possible:Utilize smart contracts来确保自动执行和透明度。
By carefully considering these aspects,你可以建立一个公平、安全且符合法规的vesting体系,为项目的持续成功奠定基础。
The Role Of Smart Contracts In Automating Vests
Smart contracts在现代区块链项目中扮演着关键角色。它们可以自动化token的释放过程,根据预设条件(如时间或达成特定目标)自动解锁tokens。这不仅提高了效率,还增强了透明度,因为所有操作都在区块链上公开记录,无需第三方干预。此外,这种自动化减少了人为错误和潜在的操控风险,使得整个vesting流程更加可信赖。
未来发展趋势显示,将智能合约与性能指标结合使用,将进一步优化token分发策略,实现更动态、更灵活的激励机制。这一技术进步也符合行业对安全性和合规性的不断追求,为投资者提供更有保障的环境。
References
1. SEC Guidance on Token Sales (2020)
2. Industry Trends in Vesting Schedules (2023)
3. Smart Contract-Based Vesting Schedules (2022)
4. Market Volatility Risks (2021)
5. Regulatory Risks in Token Distribution (2020)
6. Stakeholder Trust and Vesting Schedules (2022)
By understanding what a vestingat schedule entails—including its types、components、regulatory considerations以及最新行业趋势—you gain valuable insights into managing digital assets responsibly。 Whether you're developing new blockchain protocols或investors evaluating opportunities,这些知识都是确保安全、公平分配的重要基础。
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
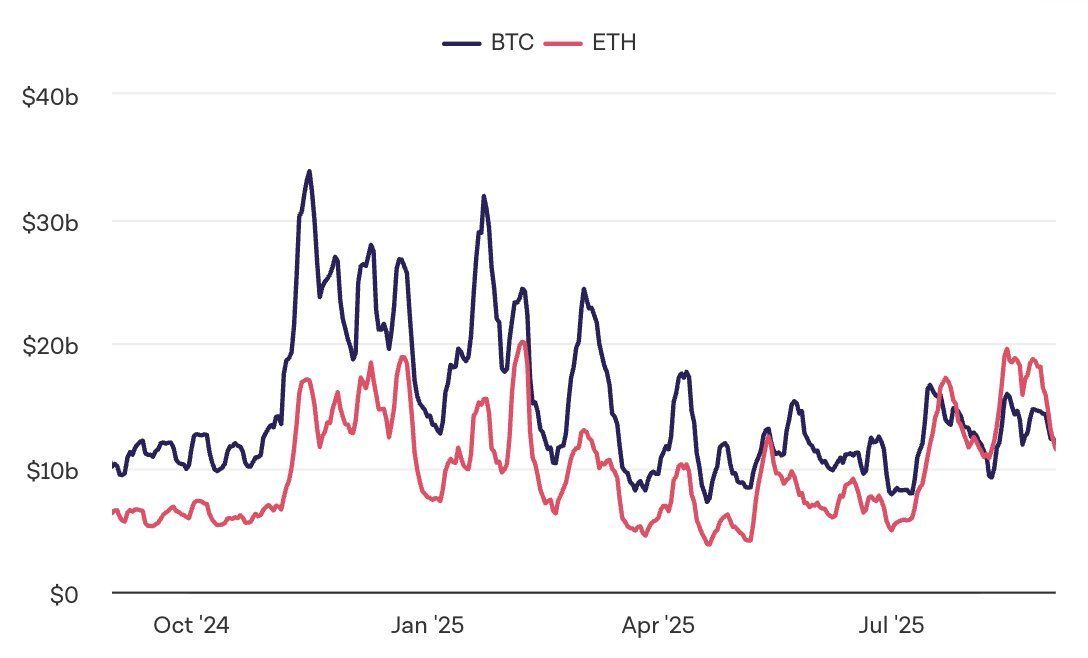
For the first time in 7 years, $ETH > $BTC in 7-day spot volume, per The Block. 🔁 👉 Bitcoin whales are rotating heavily into Ethereum.
With capital reallocating + rate cut anticipation, analysts now eye fresh ATHs in Q4 for majors.
#Ethereum #Bitcoin #cryptocurrency #blockchain


Carmelita
2025-09-04 16:37
🚨 Historic Shift on CEXs
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
Buying Cryptocurrency Safely: A Complete Guide for Investors
Understanding How to Buy Cryptocurrency Safely
Investing in cryptocurrency can be highly profitable, but it also involves significant risks. To navigate this landscape effectively, it's essential to understand the fundamentals of digital currencies, the current market environment, and best practices for secure transactions. This guide aims to provide a clear roadmap for anyone interested in purchasing cryptocurrencies responsibly and securely.
What Is Cryptocurrency and Why Is It Popular?
Cryptocurrency is a form of digital or virtual currency that relies on cryptography for security. Unlike traditional money issued by governments, cryptocurrencies operate on decentralized networks using blockchain technology—a distributed ledger that records all transactions transparently across multiple computers. Bitcoin remains the most recognized example, but thousands of other options like Ethereum, Litecoin, and Monero are available today.
The appeal of cryptocurrencies lies in their potential for high returns due to market volatility and their promise of financial privacy and decentralization. However, these same features contribute to unpredictable price swings and regulatory uncertainties that investors must consider carefully.
Market Context: Risks and Opportunities
Since their emergence over a decade ago, cryptocurrencies have experienced rapid growth alongside intense volatility. Prices can surge dramatically within short periods or plummet unexpectedly due to factors such as global economic shifts, regulatory announcements, technological updates, or market sentiment changes.
This environment makes cryptocurrency investing both attractive—offering opportunities for substantial gains—and risky—posing threats of significant losses if not approached with caution. Understanding these dynamics helps investors develop strategies aligned with their risk tolerance.
Key Factors Influencing Cryptocurrency Investments
- Decentralized Technology: Blockchain ensures transparency but requires understanding how it works.
- Security Measures: Cryptocurrencies are secured through cryptographic algorithms; however,vulnerabilities exist if security protocols are weak.
- Price Volatility: Market prices fluctuate rapidly; timing entries and exits is crucial.
- Regulatory Landscape: Laws governing crypto vary globally; staying informed prevents legal issues.
Steps to Buy Cryptocurrency Safely
- Conduct Thorough Research
Before making any purchase decisions:
- Learn about blockchain technology's basics—how transactions are verified via miners or validators.
- Explore different cryptocurrencies' use cases—some focus on privacy (like Monero), others on smart contracts (Ethereum).
- Follow reputable news sources covering market trends and regulatory updates to stay informed about potential risks or opportunities.
- Select a Reputable Exchange Platform
Choosing where you buy your crypto is critical:
- Opt for well-established exchanges with good track records regarding security measures.
- Verify compliance with local regulations such as AML (Anti-Money Laundering) and KYC (Know Your Customer) policies.
- Review user feedback concerning platform stability during high-volume trading periods.
- Use Secure Wallets for Storage
Storing your purchased crypto safely is just as important as buying it:
Hardware wallets like Ledger Nano S/X or Trezor offer cold storage solutions ideal for long-term holdings because they keep private keys offline from internet threats.
Pros:
- Enhanced security
- Reduced hacking risk
Cons:
- Slightly higher cost
- Less convenient than software wallets
Software wallets such as MetaMask provide quick access but should be protected with strong passwords plus two-factor authentication (2FA).
- Verify Your Identity Carefully
Most exchanges require identity verification before trading:
Prepare documents like government-issued IDs or proof of address.
Be cautious about phishing scams asking you to share personal information outside official channels—they pose serious security threats.
- Monitor Transactions Regularly
Keep an eye on your account activity:
Use built-in exchange tools or third-party services that track wallet movements across platforms.
Promptly report suspicious activities such as unauthorized withdrawals which could indicate hacking attempts.
- Diversify Your Investment Portfolio
Avoid putting all your funds into one cryptocurrency:
Uncertainty exists even within established coins; spreading investments reduces overall risk exposure by including stablecoins or less volatile assets alongside more speculative tokens.
- Stay Updated With Regulatory Changes
Regulations evolve constantly worldwide:
Follow official statements from financial authorities like SEC in the U.S., ESMA in Europe—or relevant local agencies—to anticipate policy shifts affecting your holdings.
Recent Developments Impacting Safe Crypto Buying
In recent years—and especially into 2023–2024—the landscape has seen notable changes impacting how investors approach safety measures:
Regulatory Frameworks:
The U.S., European Union, and other jurisdictions have introduced clearer guidelines—for example,
- The SEC’s new registration rules aim at increasing transparency among exchanges,
- The EU’s Markets in Crypto Assets (MiCA) regulation seeks standardized rules across member states,
which help reduce fraud risks while providing clarity around legal obligations when buying crypto legally.
Security Enhancements:
High-profile hacks continue reminding users about vulnerabilities—even major platforms faced breaches recently—which underscores the importance of robust security practices like multi-signature wallets combined with hardware devices designed specifically against cyberattacks.
Emerging Market Trends
Decentralized finance (DeFi) platforms have gained popularity by offering lending/borrowing services without intermediaries—this innovation increases adoption but also introduces new risks requiring diligent research before participation.
Potential Risks When Investing in Cryptocurrencies
Despite precautions,
market volatility remains unpredictable,
and sudden price swings can lead to substantial losses if not managed properly.
Regulatory uncertainty continues evolving;
regulators may impose restrictions unexpectedly,
potentially impacting asset values negatively.
Security concerns persist despite advances;
hacking incidents remind users always need vigilant asset protection strategies.
Practical Tips For Safe Crypto Investment
To minimize exposure while maximizing benefits,
consider implementing these best practices:
• Always use two-factor authentication wherever possible.• Keep private keys offline—in cold storage—for long-term holdings.• Avoid sharing sensitive information online.• Regularly update software wallets & exchange apps.• Set clear investment goals & exit strategies.
By adhering strictly to these principles—and maintaining awareness—you can significantly improve your chances of safe investing amid an ever-changing landscape.
Navigating Future Challenges And Opportunities
As cryptocurrency markets mature further—with increased institutional involvement—the ecosystem will likely see enhanced infrastructure supporting safer trading environments.
However,investors must remain vigilant regarding emerging scams,regulatory crackdowns,and technological vulnerabilities.
Continuous education remains vital; staying informed enables smarter decision-making amid rapid innovations.
This comprehensive overview aims at equipping you with knowledge necessary not only for buying cryptocurrency safely but also understanding broader implications involved in digital asset investments — empowering responsible participation within this dynamic space while safeguarding assets effectively through proven methods rooted in current industry standards.]


Lo
2025-05-15 00:33
How do you buy cryptocurrency safely?
Buying Cryptocurrency Safely: A Complete Guide for Investors
Understanding How to Buy Cryptocurrency Safely
Investing in cryptocurrency can be highly profitable, but it also involves significant risks. To navigate this landscape effectively, it's essential to understand the fundamentals of digital currencies, the current market environment, and best practices for secure transactions. This guide aims to provide a clear roadmap for anyone interested in purchasing cryptocurrencies responsibly and securely.
What Is Cryptocurrency and Why Is It Popular?
Cryptocurrency is a form of digital or virtual currency that relies on cryptography for security. Unlike traditional money issued by governments, cryptocurrencies operate on decentralized networks using blockchain technology—a distributed ledger that records all transactions transparently across multiple computers. Bitcoin remains the most recognized example, but thousands of other options like Ethereum, Litecoin, and Monero are available today.
The appeal of cryptocurrencies lies in their potential for high returns due to market volatility and their promise of financial privacy and decentralization. However, these same features contribute to unpredictable price swings and regulatory uncertainties that investors must consider carefully.
Market Context: Risks and Opportunities
Since their emergence over a decade ago, cryptocurrencies have experienced rapid growth alongside intense volatility. Prices can surge dramatically within short periods or plummet unexpectedly due to factors such as global economic shifts, regulatory announcements, technological updates, or market sentiment changes.
This environment makes cryptocurrency investing both attractive—offering opportunities for substantial gains—and risky—posing threats of significant losses if not approached with caution. Understanding these dynamics helps investors develop strategies aligned with their risk tolerance.
Key Factors Influencing Cryptocurrency Investments
- Decentralized Technology: Blockchain ensures transparency but requires understanding how it works.
- Security Measures: Cryptocurrencies are secured through cryptographic algorithms; however,vulnerabilities exist if security protocols are weak.
- Price Volatility: Market prices fluctuate rapidly; timing entries and exits is crucial.
- Regulatory Landscape: Laws governing crypto vary globally; staying informed prevents legal issues.
Steps to Buy Cryptocurrency Safely
- Conduct Thorough Research
Before making any purchase decisions:
- Learn about blockchain technology's basics—how transactions are verified via miners or validators.
- Explore different cryptocurrencies' use cases—some focus on privacy (like Monero), others on smart contracts (Ethereum).
- Follow reputable news sources covering market trends and regulatory updates to stay informed about potential risks or opportunities.
- Select a Reputable Exchange Platform
Choosing where you buy your crypto is critical:
- Opt for well-established exchanges with good track records regarding security measures.
- Verify compliance with local regulations such as AML (Anti-Money Laundering) and KYC (Know Your Customer) policies.
- Review user feedback concerning platform stability during high-volume trading periods.
- Use Secure Wallets for Storage
Storing your purchased crypto safely is just as important as buying it:
Hardware wallets like Ledger Nano S/X or Trezor offer cold storage solutions ideal for long-term holdings because they keep private keys offline from internet threats.
Pros:
- Enhanced security
- Reduced hacking risk
Cons:
- Slightly higher cost
- Less convenient than software wallets
Software wallets such as MetaMask provide quick access but should be protected with strong passwords plus two-factor authentication (2FA).
- Verify Your Identity Carefully
Most exchanges require identity verification before trading:
Prepare documents like government-issued IDs or proof of address.
Be cautious about phishing scams asking you to share personal information outside official channels—they pose serious security threats.
- Monitor Transactions Regularly
Keep an eye on your account activity:
Use built-in exchange tools or third-party services that track wallet movements across platforms.
Promptly report suspicious activities such as unauthorized withdrawals which could indicate hacking attempts.
- Diversify Your Investment Portfolio
Avoid putting all your funds into one cryptocurrency:
Uncertainty exists even within established coins; spreading investments reduces overall risk exposure by including stablecoins or less volatile assets alongside more speculative tokens.
- Stay Updated With Regulatory Changes
Regulations evolve constantly worldwide:
Follow official statements from financial authorities like SEC in the U.S., ESMA in Europe—or relevant local agencies—to anticipate policy shifts affecting your holdings.
Recent Developments Impacting Safe Crypto Buying
In recent years—and especially into 2023–2024—the landscape has seen notable changes impacting how investors approach safety measures:
Regulatory Frameworks:
The U.S., European Union, and other jurisdictions have introduced clearer guidelines—for example,
- The SEC’s new registration rules aim at increasing transparency among exchanges,
- The EU’s Markets in Crypto Assets (MiCA) regulation seeks standardized rules across member states,
which help reduce fraud risks while providing clarity around legal obligations when buying crypto legally.
Security Enhancements:
High-profile hacks continue reminding users about vulnerabilities—even major platforms faced breaches recently—which underscores the importance of robust security practices like multi-signature wallets combined with hardware devices designed specifically against cyberattacks.
Emerging Market Trends
Decentralized finance (DeFi) platforms have gained popularity by offering lending/borrowing services without intermediaries—this innovation increases adoption but also introduces new risks requiring diligent research before participation.
Potential Risks When Investing in Cryptocurrencies
Despite precautions,
market volatility remains unpredictable,
and sudden price swings can lead to substantial losses if not managed properly.
Regulatory uncertainty continues evolving;
regulators may impose restrictions unexpectedly,
potentially impacting asset values negatively.
Security concerns persist despite advances;
hacking incidents remind users always need vigilant asset protection strategies.
Practical Tips For Safe Crypto Investment
To minimize exposure while maximizing benefits,
consider implementing these best practices:
• Always use two-factor authentication wherever possible.• Keep private keys offline—in cold storage—for long-term holdings.• Avoid sharing sensitive information online.• Regularly update software wallets & exchange apps.• Set clear investment goals & exit strategies.
By adhering strictly to these principles—and maintaining awareness—you can significantly improve your chances of safe investing amid an ever-changing landscape.
Navigating Future Challenges And Opportunities
As cryptocurrency markets mature further—with increased institutional involvement—the ecosystem will likely see enhanced infrastructure supporting safer trading environments.
However,investors must remain vigilant regarding emerging scams,regulatory crackdowns,and technological vulnerabilities.
Continuous education remains vital; staying informed enables smarter decision-making amid rapid innovations.
This comprehensive overview aims at equipping you with knowledge necessary not only for buying cryptocurrency safely but also understanding broader implications involved in digital asset investments — empowering responsible participation within this dynamic space while safeguarding assets effectively through proven methods rooted in current industry standards.]
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
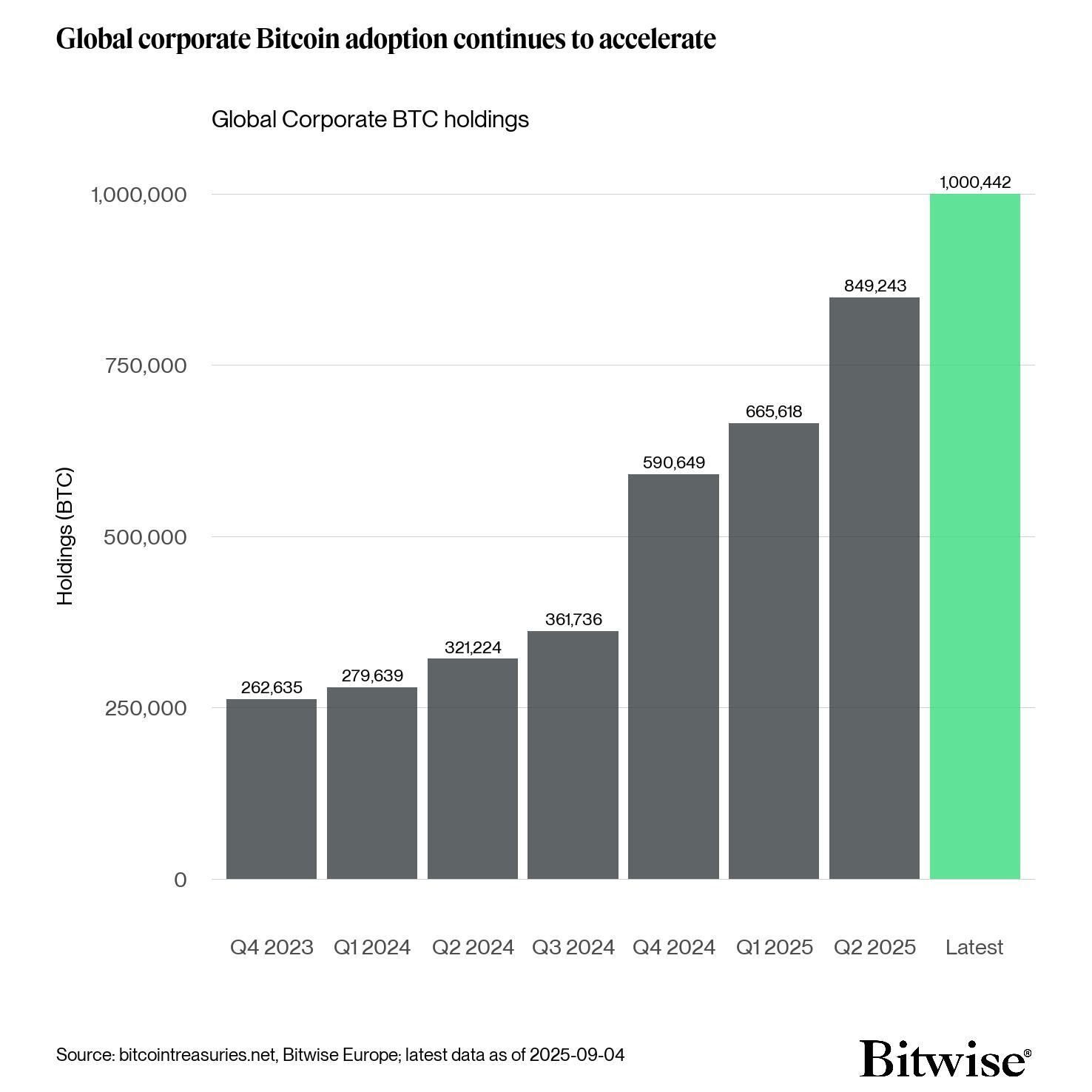
Soit 111 milliards $ retirés du marché, accentuant la pénurie d’offre. La pression d’achat s’intensifie alors que le #Bitcoin devient de plus en plus rare. 🔥
#BTC #CryptoMarkets #cryptocurrency #blockchain


Carmelita
2025-09-04 21:53
🚨 Dernière minute : Les trésoreries d’entreprises mondiales franchissent le cap du 1M $BTC
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
➡️ Achat de 2,588 $BTC/USDT pour 258,8 M$ 🟢 ➡️ Vente de 35,009 $ETH/USDT pour 152,7 M$ 🔴
Un rééquilibrage massif qui en dit long sur leur vision court-terme du marché. 👀
#Bitcoin #Ethereum #cryptocurrency #blockchain



Carmelita
2025-09-04 13:11
🔥 Mouvement stratégique de BlackRock aujourd’hui
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
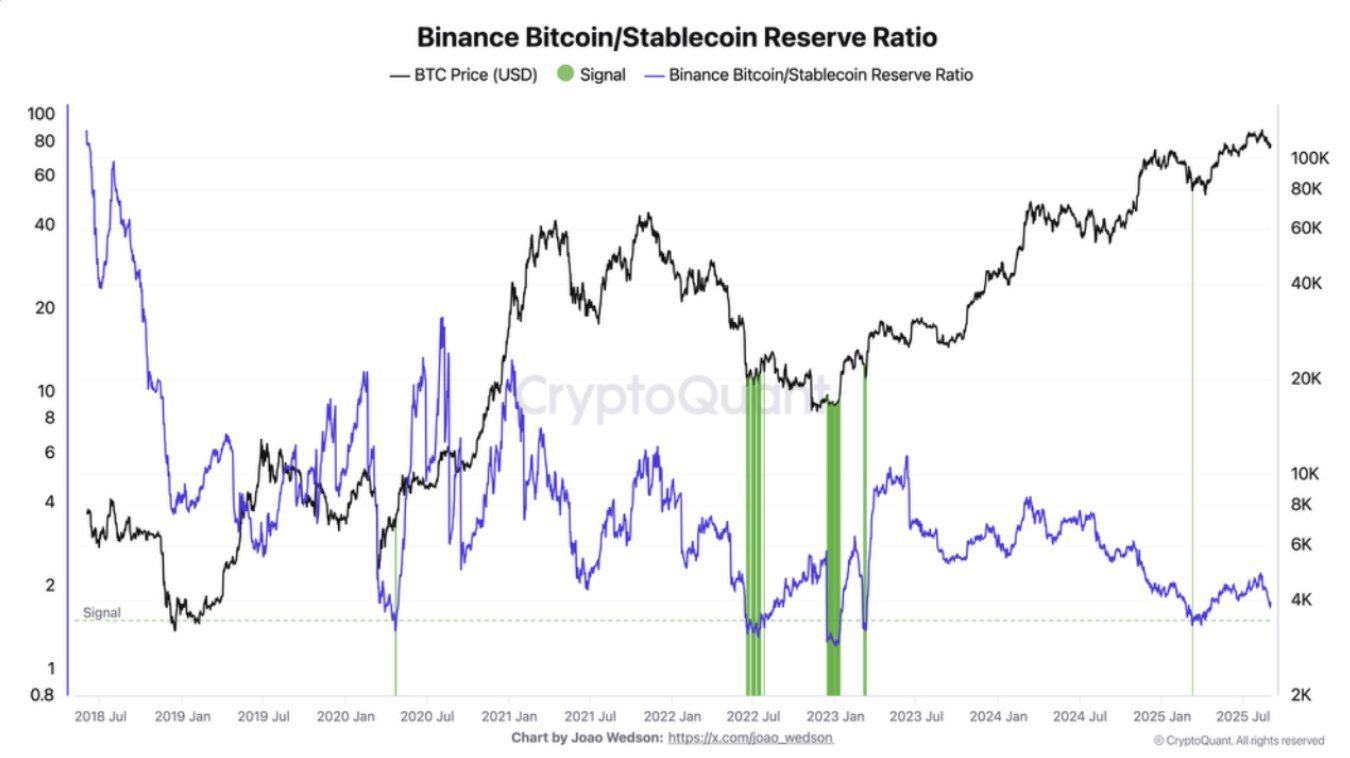
Le ratio atteint un niveau critique, un signal historique observé seulement 2 fois depuis le dernier bear market. 📊 👉 À surveiller de près pour anticiper un possible rebond.
#Bitcoin #CryptoSignals #cryptocurrency #blockchain


Carmelita
2025-09-04 17:05
🚨 Alerte Binance : Réserve $BTC vs stablecoins au bord du signal d’achat rare
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
What is Chainlink and Why Is It Important in Blockchain Ecosystems?
Understanding Chainlink: The Decentralized Oracle Network
Chainlink is a decentralized oracle network that plays a pivotal role in bridging the gap between blockchain smart contracts and real-world data. Unlike traditional blockchains, which are inherently isolated from external information, smart contracts require access to data such as market prices, weather conditions, or IoT sensor readings to execute complex functions. Chainlink provides this connectivity by securely sourcing and verifying external data for use within various blockchain platforms.
At its core, Chainlink acts as an intermediary—an open-source infrastructure that connects on-chain logic with off-chain information sources like APIs, IoT devices, and other external systems. This capability enables developers to build more sophisticated decentralized applications (dApps) across multiple sectors including finance, insurance, gaming, and supply chain management.
The Role of Oracles in Blockchain Technology
Smart contracts are self-executing agreements coded on blockchain networks like Ethereum or Binance Smart Chain. However, their functionality is limited without reliable external data inputs—a problem known as the "oracle problem." Oracles serve as trusted entities that feed real-world information into these contracts.
Chainlink’s decentralized approach involves multiple independent nodes (oracles) providing data to prevent single points of failure or manipulation. These nodes are incentivized through cryptographic security measures and economic rewards to ensure accuracy and integrity. This decentralization enhances trustworthiness compared to centralized or single-source solutions.
Why Is Chainlink Critical for DeFi?
Decentralized Finance (DeFi) has emerged as one of the most significant use cases for blockchain technology—enabling lending protocols, stablecoins, prediction markets—and relies heavily on accurate real-time data. For example:
- Lending platforms need current interest rates.
- Prediction markets depend on event outcomes.
- Insurance protocols require verification of claims based on external events.
Chainlink supplies these vital data feeds securely and reliably across various DeFi projects. Its ability to aggregate multiple sources reduces risks associated with faulty or manipulated information—an essential feature given the financial stakes involved.
Recent Developments Enhancing Chainlink’s Utility
Over recent years, Chainlink has expanded its capabilities through strategic partnerships and innovative features:
Partnerships: In 2023 alone, collaborations with tech giants like Google Cloud and Microsoft Azure have enhanced its capacity for sourcing diverse datasets.
New Tools:
- Chainlink VRF (Verifiable Random Function) provides provably fair randomness crucial for gaming applications such as NFT minting or lotteries.
- Chainlink Keepers automate contract execution based on predefined conditions without manual intervention.
These advancements improve both security standards and developer usability while broadening potential application areas.
Regulatory Environment & Community Growth
As blockchain adoption accelerates globally—including regions with evolving regulatory frameworks—Chainlink faces increased scrutiny regarding compliance especially related to DeFi activities. The company actively engages with regulators worldwide aiming for transparent operations while maintaining decentralization principles.
Meanwhile, community engagement remains strong; developer resources have expanded significantly since 2022 through educational initiatives aimed at fostering innovation within the ecosystem. This growth underscores confidence in Chainlink's long-term relevance amid competitive pressures from other oracle providers like Band Protocol or The Graph.
Challenges Facing Chainlink: Risks & Competition
Despite its leadership position in decentralized oracles:
Regulatory Risks: Evolving laws could impose restrictions impacting how chainlinks operate across jurisdictions.
Security Concerns: Although robust mechanisms exist against malicious node behavior—such as cryptographic proofs—the risk of unforeseen vulnerabilities persists inherent in complex distributed systems.
Market Competition: Other projects aim to provide similar services; continuous innovation is necessary for maintaining market dominance.
The Significance of Chainlink in Web3 Development
By enabling secure access to off-chain data sources without compromising decentralization principles—which underpin Web3's ethos—Chainlink facilitates trustless interactions essential for building scalable dApps across industries. Its infrastructure supports not only financial applications but also emerging fields like supply chain transparency and environmental monitoring where verified real-world info is critical.
How Does It Impact Users & Developers?
For end-users relying on DeFi products or NFT platforms powered by smart contracts integrated via Chainlink:
- They benefit from increased reliability due to tamper-proof data feeds,
- Experience fewer failures caused by inaccurate inputs,
- Gain confidence knowing their assets are protected by advanced security measures.
Developers find value in simplified integration processes thanks to comprehensive tools such as VRF and Keepers which streamline deploying complex functionalities efficiently.
Future Outlook: Growth Opportunities & Challenges Ahead
Looking forward beyond 2023,
- Continued expansion into enterprise sectors through new partnerships will likely diversify use cases further,
- Ongoing regulatory dialogues may shape operational frameworks but also pose hurdles if not navigated carefully,
- Competitive landscape evolution demands persistent innovation around scalability solutions like Layer 2 integrations,
All these factors suggest that while challenges exist—including regulatory uncertainties—the foundational importance of reliable off-chain data provision ensures chains like Link remain central players shaping Web3’s future development.
In Summary
Chainlin k stands out as a cornerstone technology enabling trustless interactions between blockchains and the outside world—a necessity for realizing fully functional decentralized applications across finance, gaming , insurance ,and beyond . Its commitment toward security innovations coupled with strategic collaborations positions it well amidst growing competition within the oracle space . As Web3 continues evolving rapidly , understanding how services like those provided by ChainLink underpin this transformation offers valuable insights into shaping future digital ecosystems.


JCUSER-F1IIaxXA
2025-05-09 14:21
What is Chainlink, and why is it important?
What is Chainlink and Why Is It Important in Blockchain Ecosystems?
Understanding Chainlink: The Decentralized Oracle Network
Chainlink is a decentralized oracle network that plays a pivotal role in bridging the gap between blockchain smart contracts and real-world data. Unlike traditional blockchains, which are inherently isolated from external information, smart contracts require access to data such as market prices, weather conditions, or IoT sensor readings to execute complex functions. Chainlink provides this connectivity by securely sourcing and verifying external data for use within various blockchain platforms.
At its core, Chainlink acts as an intermediary—an open-source infrastructure that connects on-chain logic with off-chain information sources like APIs, IoT devices, and other external systems. This capability enables developers to build more sophisticated decentralized applications (dApps) across multiple sectors including finance, insurance, gaming, and supply chain management.
The Role of Oracles in Blockchain Technology
Smart contracts are self-executing agreements coded on blockchain networks like Ethereum or Binance Smart Chain. However, their functionality is limited without reliable external data inputs—a problem known as the "oracle problem." Oracles serve as trusted entities that feed real-world information into these contracts.
Chainlink’s decentralized approach involves multiple independent nodes (oracles) providing data to prevent single points of failure or manipulation. These nodes are incentivized through cryptographic security measures and economic rewards to ensure accuracy and integrity. This decentralization enhances trustworthiness compared to centralized or single-source solutions.
Why Is Chainlink Critical for DeFi?
Decentralized Finance (DeFi) has emerged as one of the most significant use cases for blockchain technology—enabling lending protocols, stablecoins, prediction markets—and relies heavily on accurate real-time data. For example:
- Lending platforms need current interest rates.
- Prediction markets depend on event outcomes.
- Insurance protocols require verification of claims based on external events.
Chainlink supplies these vital data feeds securely and reliably across various DeFi projects. Its ability to aggregate multiple sources reduces risks associated with faulty or manipulated information—an essential feature given the financial stakes involved.
Recent Developments Enhancing Chainlink’s Utility
Over recent years, Chainlink has expanded its capabilities through strategic partnerships and innovative features:
Partnerships: In 2023 alone, collaborations with tech giants like Google Cloud and Microsoft Azure have enhanced its capacity for sourcing diverse datasets.
New Tools:
- Chainlink VRF (Verifiable Random Function) provides provably fair randomness crucial for gaming applications such as NFT minting or lotteries.
- Chainlink Keepers automate contract execution based on predefined conditions without manual intervention.
These advancements improve both security standards and developer usability while broadening potential application areas.
Regulatory Environment & Community Growth
As blockchain adoption accelerates globally—including regions with evolving regulatory frameworks—Chainlink faces increased scrutiny regarding compliance especially related to DeFi activities. The company actively engages with regulators worldwide aiming for transparent operations while maintaining decentralization principles.
Meanwhile, community engagement remains strong; developer resources have expanded significantly since 2022 through educational initiatives aimed at fostering innovation within the ecosystem. This growth underscores confidence in Chainlink's long-term relevance amid competitive pressures from other oracle providers like Band Protocol or The Graph.
Challenges Facing Chainlink: Risks & Competition
Despite its leadership position in decentralized oracles:
Regulatory Risks: Evolving laws could impose restrictions impacting how chainlinks operate across jurisdictions.
Security Concerns: Although robust mechanisms exist against malicious node behavior—such as cryptographic proofs—the risk of unforeseen vulnerabilities persists inherent in complex distributed systems.
Market Competition: Other projects aim to provide similar services; continuous innovation is necessary for maintaining market dominance.
The Significance of Chainlink in Web3 Development
By enabling secure access to off-chain data sources without compromising decentralization principles—which underpin Web3's ethos—Chainlink facilitates trustless interactions essential for building scalable dApps across industries. Its infrastructure supports not only financial applications but also emerging fields like supply chain transparency and environmental monitoring where verified real-world info is critical.
How Does It Impact Users & Developers?
For end-users relying on DeFi products or NFT platforms powered by smart contracts integrated via Chainlink:
- They benefit from increased reliability due to tamper-proof data feeds,
- Experience fewer failures caused by inaccurate inputs,
- Gain confidence knowing their assets are protected by advanced security measures.
Developers find value in simplified integration processes thanks to comprehensive tools such as VRF and Keepers which streamline deploying complex functionalities efficiently.
Future Outlook: Growth Opportunities & Challenges Ahead
Looking forward beyond 2023,
- Continued expansion into enterprise sectors through new partnerships will likely diversify use cases further,
- Ongoing regulatory dialogues may shape operational frameworks but also pose hurdles if not navigated carefully,
- Competitive landscape evolution demands persistent innovation around scalability solutions like Layer 2 integrations,
All these factors suggest that while challenges exist—including regulatory uncertainties—the foundational importance of reliable off-chain data provision ensures chains like Link remain central players shaping Web3’s future development.
In Summary
Chainlin k stands out as a cornerstone technology enabling trustless interactions between blockchains and the outside world—a necessity for realizing fully functional decentralized applications across finance, gaming , insurance ,and beyond . Its commitment toward security innovations coupled with strategic collaborations positions it well amidst growing competition within the oracle space . As Web3 continues evolving rapidly , understanding how services like those provided by ChainLink underpin this transformation offers valuable insights into shaping future digital ecosystems.
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
1280 utilisateurs couverts cette semaine ! 🚀
📌 Rappel des règles : • Perte nette ≥ 500 USDT ➡️ Allocation 1:1 en puissance de calcul • Puissance permanente générant des $JU/USDT quotidiens • Gains vérifiables on-chain, transparents et fiables
📅 Période de référence Week 8 : 4 juillet – 10 août 2025
#JuCoin #blockchain #crypto



Carmelita
2025-08-08 10:27
💙 JuCoin Computing Power – Week 7 ✅
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
How Does Substrate Simplify Building Custom Blockchains?
Understanding Substrate and Its Role in Blockchain Development
Substrate is an open-source blockchain development framework created by Parity Technologies, now part of the Polkadot ecosystem. It aims to make the process of building custom blockchains more accessible, efficient, and flexible. Unlike traditional blockchain development, which often requires extensive expertise in cryptography, consensus algorithms, and low-level programming, Substrate provides a set of pre-built modules and tools that streamline these complex tasks. This allows developers—whether experienced or new—to focus on designing unique features tailored to their specific use cases.
By leveraging Substrate’s modular architecture and integration with Polkadot’s interoperability features, developers can create blockchains that are not only customized but also capable of communicating seamlessly with other networks. This capability is particularly valuable as the demand for specialized blockchain solutions continues to grow across industries such as finance, supply chain management, gaming, and decentralized applications (dApps).
Key Features That Make Building Custom Blockchains Easier
One of the primary reasons why Substrate simplifies blockchain creation is its modular design. Developers can select from a library of ready-made components—called pallets—that handle core functionalities like consensus mechanisms (e.g., Aura or Babe), transaction processing (including fee models), storage solutions, governance protocols, and more. If needed, they can also develop custom pallets to introduce unique logic without altering the entire system.
Another significant advantage is its tight integration with Polkadot’s ecosystem. This enables newly built blockchains—often called parachains—to interoperate smoothly within a broader network environment. Such interoperability reduces complexity when connecting multiple chains for cross-chain data transfer or asset movement.
The runtime environment provided by Substrate forms a robust foundation for deploying these modules efficiently. It manages critical operations such as transaction validation and state updates while ensuring security through well-tested consensus algorithms.
For developers’ convenience, Substrate offers comprehensive tooling support—including command-line interfaces (CLI), developer libraries in Rust (the primary language used), detailed documentation—and active community resources like forums and example projects. These tools significantly reduce setup time and lower barriers for onboarding new developers into blockchain development.
How Substrate Addresses Common Challenges in Blockchain Development
Traditional methods often involve writing low-level code from scratch or heavily customizing existing frameworks—a process that can be both time-consuming and error-prone. By providing reusable building blocks along with clear APIs and standards adherence (such as WebAssembly support), Substrate minimizes these challenges.
Furthermore:
- Rapid Prototyping: Developers can quickly assemble prototypes using pre-existing pallets before refining their project.
- Security: The framework incorporates best practices from established protocols; ongoing updates improve resilience against vulnerabilities.
- Scalability: Designed to handle high throughput scenarios; recent enhancements aim at supporting large-scale enterprise applications.
- Interoperability: Built-in support for cross-chain communication aligns with industry trends toward interconnected decentralized networks.
Recent Developments Enhancing Simplicity
Since its mainnet launch in May 2020 alongside Polkadot’s debut—a milestone demonstrating scalability—the ecosystem has seen continuous improvements aimed at simplifying development further:
- Enhanced cross-chain capabilities facilitate easier data sharing between different blockchains.
- Security upgrades address emerging vulnerabilities proactively.
- Ecosystem growth brings more third-party tools & integrations that expand what developers can achieve without reinventing wheels.
These developments mean that even complex projects involving multi-layered logic or high security requirements become more manageable within the substrate framework.
Potential Challenges When Using Substrate
While it offers many advantages over traditional approaches—and has gained popularity among startups as well as established organizations—it isn’t entirely free from challenges:
- Competition: Other frameworks like Ethereum's Web3.js SDK or Solana's SDKs provide alternative options; choosing between them depends on project needs.
- Regulatory Environment: As custom chains proliferate globally—especially those handling sensitive data—they may attract regulatory scrutiny which could impact deployment strategies.
- Scalability Limits: Although designed for scalability today—with ongoing optimization—the capacity to handle extremely large-scale applications remains an area under active research.
Despite these hurdles—which are common across all innovative technologies—Substrate continues to evolve rapidly thanks to strong community engagement & dedicated developer efforts worldwide.
Why Developers Prefer Using Substrate
Developers value how quickly they can go from idea conceptually into a working prototype using predefined modules rather than starting from zero each time. The ability to customize components ensures flexibility while maintaining security standards rooted in proven cryptographic practices makes it suitable even for mission-critical applications.
Additionally:
- Its compatibility with WebAssembly allows running smart contracts written in multiple languages beyond Rust
- The active community provides ongoing support through forums like Stack Exchange or GitHub repositories
- Continuous updates keep pace with industry demands around privacy enhancements & interoperability features
This combination fosters trustworthiness essential for enterprise adoption where compliance & reliability are paramount—a key aspect aligning with Google Scholar-recognized principles of transparency & technical competence known collectively as E-A-T (Expertise–Authoritativeness–Trustworthiness).
Future Outlook: How Simplification Will Shape Blockchain Innovation
As blockchain technology matures amid increasing adoption pressures—from DeFi platforms to enterprise supply chains—the need for accessible yet powerful development frameworks will grow correspondingly. With its focus on modularity combined with seamless interoperability via Polkadot integration—and ongoing improvements addressing scalability/security concerns—Substrate positions itself as an ideal platform enabling rapid innovation without sacrificing robustness or security standards.
In summary,
Substrate significantly lowers barriers associated with traditional blockchain creation by offering reusable components backed by strong community support—all within an architecture designed explicitly for customization at scale. Whether building simple tokens or complex dApps requiring high throughput/security guarantees—or integrating multiple chains—it empowers developers across skill levels while maintaining alignment with industry best practices.
Keywords: subtrate framework benefits | custom blockchain development | polkadot ecosystem | modular architecture | interoperable blockchains | scalable dApps | secure smart contracts


JCUSER-F1IIaxXA
2025-05-14 11:00
How does Substrate simplify building custom blockchains?
How Does Substrate Simplify Building Custom Blockchains?
Understanding Substrate and Its Role in Blockchain Development
Substrate is an open-source blockchain development framework created by Parity Technologies, now part of the Polkadot ecosystem. It aims to make the process of building custom blockchains more accessible, efficient, and flexible. Unlike traditional blockchain development, which often requires extensive expertise in cryptography, consensus algorithms, and low-level programming, Substrate provides a set of pre-built modules and tools that streamline these complex tasks. This allows developers—whether experienced or new—to focus on designing unique features tailored to their specific use cases.
By leveraging Substrate’s modular architecture and integration with Polkadot’s interoperability features, developers can create blockchains that are not only customized but also capable of communicating seamlessly with other networks. This capability is particularly valuable as the demand for specialized blockchain solutions continues to grow across industries such as finance, supply chain management, gaming, and decentralized applications (dApps).
Key Features That Make Building Custom Blockchains Easier
One of the primary reasons why Substrate simplifies blockchain creation is its modular design. Developers can select from a library of ready-made components—called pallets—that handle core functionalities like consensus mechanisms (e.g., Aura or Babe), transaction processing (including fee models), storage solutions, governance protocols, and more. If needed, they can also develop custom pallets to introduce unique logic without altering the entire system.
Another significant advantage is its tight integration with Polkadot’s ecosystem. This enables newly built blockchains—often called parachains—to interoperate smoothly within a broader network environment. Such interoperability reduces complexity when connecting multiple chains for cross-chain data transfer or asset movement.
The runtime environment provided by Substrate forms a robust foundation for deploying these modules efficiently. It manages critical operations such as transaction validation and state updates while ensuring security through well-tested consensus algorithms.
For developers’ convenience, Substrate offers comprehensive tooling support—including command-line interfaces (CLI), developer libraries in Rust (the primary language used), detailed documentation—and active community resources like forums and example projects. These tools significantly reduce setup time and lower barriers for onboarding new developers into blockchain development.
How Substrate Addresses Common Challenges in Blockchain Development
Traditional methods often involve writing low-level code from scratch or heavily customizing existing frameworks—a process that can be both time-consuming and error-prone. By providing reusable building blocks along with clear APIs and standards adherence (such as WebAssembly support), Substrate minimizes these challenges.
Furthermore:
- Rapid Prototyping: Developers can quickly assemble prototypes using pre-existing pallets before refining their project.
- Security: The framework incorporates best practices from established protocols; ongoing updates improve resilience against vulnerabilities.
- Scalability: Designed to handle high throughput scenarios; recent enhancements aim at supporting large-scale enterprise applications.
- Interoperability: Built-in support for cross-chain communication aligns with industry trends toward interconnected decentralized networks.
Recent Developments Enhancing Simplicity
Since its mainnet launch in May 2020 alongside Polkadot’s debut—a milestone demonstrating scalability—the ecosystem has seen continuous improvements aimed at simplifying development further:
- Enhanced cross-chain capabilities facilitate easier data sharing between different blockchains.
- Security upgrades address emerging vulnerabilities proactively.
- Ecosystem growth brings more third-party tools & integrations that expand what developers can achieve without reinventing wheels.
These developments mean that even complex projects involving multi-layered logic or high security requirements become more manageable within the substrate framework.
Potential Challenges When Using Substrate
While it offers many advantages over traditional approaches—and has gained popularity among startups as well as established organizations—it isn’t entirely free from challenges:
- Competition: Other frameworks like Ethereum's Web3.js SDK or Solana's SDKs provide alternative options; choosing between them depends on project needs.
- Regulatory Environment: As custom chains proliferate globally—especially those handling sensitive data—they may attract regulatory scrutiny which could impact deployment strategies.
- Scalability Limits: Although designed for scalability today—with ongoing optimization—the capacity to handle extremely large-scale applications remains an area under active research.
Despite these hurdles—which are common across all innovative technologies—Substrate continues to evolve rapidly thanks to strong community engagement & dedicated developer efforts worldwide.
Why Developers Prefer Using Substrate
Developers value how quickly they can go from idea conceptually into a working prototype using predefined modules rather than starting from zero each time. The ability to customize components ensures flexibility while maintaining security standards rooted in proven cryptographic practices makes it suitable even for mission-critical applications.
Additionally:
- Its compatibility with WebAssembly allows running smart contracts written in multiple languages beyond Rust
- The active community provides ongoing support through forums like Stack Exchange or GitHub repositories
- Continuous updates keep pace with industry demands around privacy enhancements & interoperability features
This combination fosters trustworthiness essential for enterprise adoption where compliance & reliability are paramount—a key aspect aligning with Google Scholar-recognized principles of transparency & technical competence known collectively as E-A-T (Expertise–Authoritativeness–Trustworthiness).
Future Outlook: How Simplification Will Shape Blockchain Innovation
As blockchain technology matures amid increasing adoption pressures—from DeFi platforms to enterprise supply chains—the need for accessible yet powerful development frameworks will grow correspondingly. With its focus on modularity combined with seamless interoperability via Polkadot integration—and ongoing improvements addressing scalability/security concerns—Substrate positions itself as an ideal platform enabling rapid innovation without sacrificing robustness or security standards.
In summary,
Substrate significantly lowers barriers associated with traditional blockchain creation by offering reusable components backed by strong community support—all within an architecture designed explicitly for customization at scale. Whether building simple tokens or complex dApps requiring high throughput/security guarantees—or integrating multiple chains—it empowers developers across skill levels while maintaining alignment with industry best practices.
Keywords: subtrate framework benefits | custom blockchain development | polkadot ecosystem | modular architecture | interoperable blockchains | scalable dApps | secure smart contracts
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
What Is Liquidity Mining? A Complete Guide
Liquidity mining has become a fundamental aspect of the decentralized finance (DeFi) ecosystem, transforming how digital assets are used to facilitate trading and lending. As DeFi continues to grow rapidly, understanding liquidity mining is essential for investors, developers, and enthusiasts aiming to navigate this innovative space effectively.
Understanding Liquidity Mining in DeFi
At its core, liquidity mining involves providing assets to decentralized exchanges (DEXs) or other DeFi protocols by locking them into liquidity pools. These pools enable users to trade cryptocurrencies directly without relying on traditional centralized intermediaries. When users contribute their tokens—such as stablecoins or other cryptocurrencies—they earn rewards based on the trading activity within these pools.
This process is akin to yield farming but specifically focuses on incentivizing asset provision rather than lending alone. By participating in liquidity mining, users help improve market efficiency and price stability across various platforms while earning passive income through fees and additional token incentives.
How Does Liquidity Mining Work?
Participants lock their tokens into a smart contract-based pool that facilitates trades between different crypto assets. In return for providing liquidity, they typically receive two types of rewards:
- Trading Fees: A portion of the transaction fees generated from swaps within the pool.
- Governance Tokens: Many platforms distribute native tokens that grant voting rights or future benefits within the protocol.
The value of these rewards depends on several factors including platform activity, token pair volatility, and overall market conditions. However, it's important for participants to be aware of risks such as impermanent loss—a situation where changes in asset prices can lead to potential losses compared to simply holding the tokens outside the pool.
Key Platforms Leading Liquidity Mining Initiatives
Several prominent DeFi platforms have pioneered liquidity mining programs that attract millions of dollars worth of assets:
- Uniswap: Launched its V3 version in May 2021 with concentrated liquidity features allowing providers to specify price ranges for their contributions.
- SushiSwap: Known for offering higher-than-average rewards since its inception in September 2020; it also faced some security challenges along the way.
- Curve Finance: Focused primarily on stablecoin pairs since July 2019; appreciated for low fees and high efficiency due to stable asset swaps.
These platforms leverage innovative mechanisms like token incentives and community governance models that foster user engagement while expanding their ecosystems.
Recent Trends Shaping Liquidity Mining
The landscape of liquidity mining has evolved significantly over recent years:
Introduction of Concentrated Liquidity
Uniswap V3's release marked a major shift by enabling providers to concentrate their capital within specific price ranges rather than spreading it thinly across an entire spectrum. This innovation allows more efficient use of funds but also introduces complexity regarding risk management.
Yield Farming Expansion
Initially centered around lending protocols like Compound or Aave—where users earned interest by depositing assets—the concept expanded into DEX-focused strategies involving direct participation in liquidity pools across multiple platforms such as SushiSwap and Curve Finance.
Regulatory Attention
As DeFi gains mainstream attention, regulators worldwide are scrutinizing aspects like tax implications and anti-money laundering measures associated with yield farming activities—including liquidity mining programs—raising questions about compliance standards moving forward.
Market Volatility Impact
Cryptocurrency markets are inherently volatile; sudden swings can affect both platform revenues (via fee fluctuations) and provider holdings due to impermanent loss risks. This volatility underscores the importance for participants not only seeking yields but also managing exposure carefully.
Risks Associated With Liquidity Mining
While offering attractive returns, engaging in liquidity mining involves notable risks:
Impermanent Loss: Price divergence between pooled assets can lead providers back below initial deposit values if not managed properly.
Security Vulnerabilities: Smart contract bugs or exploits have led several high-profile hacks affecting user funds across various protocols.
Regulatory Uncertainty: Governments are increasingly examining DeFi activities which could result in new restrictions or legal challenges impacting ongoing operations.
Economic Sustainability Concerns: As reward incentives diminish over time or if market conditions change unfavorably, many participants may withdraw their assets — potentially destabilizing certain pools.
The Future Outlook For Liquidity Mining
Looking ahead, several factors will influence how sustainable and impactful liquidity mining remains within DeFi:
- Enhanced Security Measures: Protocols adopting rigorous audits will reduce vulnerabilities.
- Innovative Incentive Models: New reward structures might better balance risk-reward ratios for providers.
- Regulatory Clarity: Clearer guidelines could legitimize participation while protecting consumers.
- Market Maturity: As more institutional players enter DeFi markets—bringing larger capital flows—the dynamics around yield generation may shift toward more sophisticated strategies beyond simple staking models.
In summary, understanding what constitutes effective participation in liquidity mining requires awareness not only of potential earnings but also associated risks like impermanent loss and regulatory developments. For those interested in leveraging decentralized finance’s capabilities responsibly—and contributing meaningfully—it remains an evolving yet promising avenue aligned with broader trends toward decentralization and financial democratization.
Keywords:liquidity mining explained | decentralized finance | yield farming | crypto staking | impermanent loss | DeFi protocols | cryptocurrency trading | blockchain security


kai
2025-05-09 13:22
What is liquidity mining?
What Is Liquidity Mining? A Complete Guide
Liquidity mining has become a fundamental aspect of the decentralized finance (DeFi) ecosystem, transforming how digital assets are used to facilitate trading and lending. As DeFi continues to grow rapidly, understanding liquidity mining is essential for investors, developers, and enthusiasts aiming to navigate this innovative space effectively.
Understanding Liquidity Mining in DeFi
At its core, liquidity mining involves providing assets to decentralized exchanges (DEXs) or other DeFi protocols by locking them into liquidity pools. These pools enable users to trade cryptocurrencies directly without relying on traditional centralized intermediaries. When users contribute their tokens—such as stablecoins or other cryptocurrencies—they earn rewards based on the trading activity within these pools.
This process is akin to yield farming but specifically focuses on incentivizing asset provision rather than lending alone. By participating in liquidity mining, users help improve market efficiency and price stability across various platforms while earning passive income through fees and additional token incentives.
How Does Liquidity Mining Work?
Participants lock their tokens into a smart contract-based pool that facilitates trades between different crypto assets. In return for providing liquidity, they typically receive two types of rewards:
- Trading Fees: A portion of the transaction fees generated from swaps within the pool.
- Governance Tokens: Many platforms distribute native tokens that grant voting rights or future benefits within the protocol.
The value of these rewards depends on several factors including platform activity, token pair volatility, and overall market conditions. However, it's important for participants to be aware of risks such as impermanent loss—a situation where changes in asset prices can lead to potential losses compared to simply holding the tokens outside the pool.
Key Platforms Leading Liquidity Mining Initiatives
Several prominent DeFi platforms have pioneered liquidity mining programs that attract millions of dollars worth of assets:
- Uniswap: Launched its V3 version in May 2021 with concentrated liquidity features allowing providers to specify price ranges for their contributions.
- SushiSwap: Known for offering higher-than-average rewards since its inception in September 2020; it also faced some security challenges along the way.
- Curve Finance: Focused primarily on stablecoin pairs since July 2019; appreciated for low fees and high efficiency due to stable asset swaps.
These platforms leverage innovative mechanisms like token incentives and community governance models that foster user engagement while expanding their ecosystems.
Recent Trends Shaping Liquidity Mining
The landscape of liquidity mining has evolved significantly over recent years:
Introduction of Concentrated Liquidity
Uniswap V3's release marked a major shift by enabling providers to concentrate their capital within specific price ranges rather than spreading it thinly across an entire spectrum. This innovation allows more efficient use of funds but also introduces complexity regarding risk management.
Yield Farming Expansion
Initially centered around lending protocols like Compound or Aave—where users earned interest by depositing assets—the concept expanded into DEX-focused strategies involving direct participation in liquidity pools across multiple platforms such as SushiSwap and Curve Finance.
Regulatory Attention
As DeFi gains mainstream attention, regulators worldwide are scrutinizing aspects like tax implications and anti-money laundering measures associated with yield farming activities—including liquidity mining programs—raising questions about compliance standards moving forward.
Market Volatility Impact
Cryptocurrency markets are inherently volatile; sudden swings can affect both platform revenues (via fee fluctuations) and provider holdings due to impermanent loss risks. This volatility underscores the importance for participants not only seeking yields but also managing exposure carefully.
Risks Associated With Liquidity Mining
While offering attractive returns, engaging in liquidity mining involves notable risks:
Impermanent Loss: Price divergence between pooled assets can lead providers back below initial deposit values if not managed properly.
Security Vulnerabilities: Smart contract bugs or exploits have led several high-profile hacks affecting user funds across various protocols.
Regulatory Uncertainty: Governments are increasingly examining DeFi activities which could result in new restrictions or legal challenges impacting ongoing operations.
Economic Sustainability Concerns: As reward incentives diminish over time or if market conditions change unfavorably, many participants may withdraw their assets — potentially destabilizing certain pools.
The Future Outlook For Liquidity Mining
Looking ahead, several factors will influence how sustainable and impactful liquidity mining remains within DeFi:
- Enhanced Security Measures: Protocols adopting rigorous audits will reduce vulnerabilities.
- Innovative Incentive Models: New reward structures might better balance risk-reward ratios for providers.
- Regulatory Clarity: Clearer guidelines could legitimize participation while protecting consumers.
- Market Maturity: As more institutional players enter DeFi markets—bringing larger capital flows—the dynamics around yield generation may shift toward more sophisticated strategies beyond simple staking models.
In summary, understanding what constitutes effective participation in liquidity mining requires awareness not only of potential earnings but also associated risks like impermanent loss and regulatory developments. For those interested in leveraging decentralized finance’s capabilities responsibly—and contributing meaningfully—it remains an evolving yet promising avenue aligned with broader trends toward decentralization and financial democratization.
Keywords:liquidity mining explained | decentralized finance | yield farming | crypto staking | impermanent loss | DeFi protocols | cryptocurrency trading | blockchain security
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
👉 Quand une baleine de ce calibre bouge, tout l’écosystème s’interroge. Le fait que Justin affirme “ne pas vouloir vendre” ne suffit pas à calmer les spéculations :
Risque de pression réglementaire accrue sur les fondateurs influents. Impact potentiel sur la liquidité et la confiance autour de $WLFI. Opportunité pour ceux qui savent lire au-delà du bruit médiatique.
📊 Le marché crypto ne dort jamais, et chaque mouvement de baleine peut redessiner les équilibres. La vraie question : serez-vous observateur ou acteur quand le prochain signal tombera ?
#crypto #blockchain #WLFI #cryptocurrency #blockchain


Carmelita
2025-09-04 23:06
🔥 “9M$ en $WLFI, wallet de Justin Sun blacklisté : simple transfert ou signal caché pour le march
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
What Blockchain Technology Uses: An In-Depth Overview
Understanding the core technology behind blockchain is essential for grasping its potential and limitations. At its heart, blockchain employs a combination of cryptography, decentralized networks, and consensus mechanisms to create a secure and transparent digital ledger system. This foundation allows blockchain to serve as a trustworthy platform for various applications across industries.
Cryptography: Securing Transactions
Cryptography is fundamental to blockchain's security features. It involves encrypting transaction data so that only authorized parties can access or modify it. Public-key cryptography, in particular, plays a vital role by generating unique key pairs—public keys used as addresses and private keys for signing transactions. This ensures that each transaction is authentic and tamper-proof. Additionally, cryptographic hashing functions produce fixed-length strings (hashes) from data inputs; these hashes are used to link blocks securely in the chain, making alterations detectable.
Decentralized Network Architecture
Unlike traditional centralized databases managed by single entities, blockchain operates on a decentralized network of computers called nodes. Each node maintains an identical copy of the entire ledger, which promotes transparency and resilience against failures or attacks. When new transactions occur, they are broadcasted across the network where nodes validate them through consensus mechanisms before adding them to the ledger.
Consensus Mechanisms: Validating Data Integrity
Consensus algorithms ensure all participants agree on the state of the ledger without relying on central authority. The two most common methods are Proof of Work (PoW) and Proof of Stake (PoS).
- Proof of Work requires miners to solve complex mathematical puzzles—a process that consumes significant computational power—to validate transactions and add new blocks.
- Proof of Stake, on the other hand, selects validators based on their holdings or stake in the network’s cryptocurrency value rather than computational effort.
These mechanisms prevent malicious activities like double-spending or fraudulent entries by making it costly or impractical for bad actors to manipulate data.
How Blockchain Uses These Technologies in Practice
The integration of cryptography, decentralization, and consensus protocols enables blockchain's wide-ranging applications:
- In finance—facilitating secure cross-border payments with reduced costs.
- In government—tracking expenditures transparently while safeguarding sensitive information.
- In entertainment—enabling NFT ownership verification within gaming ecosystems.
- In cybersecurity—protecting critical infrastructure from cyber threats through tamper-resistant ledgers.
Each application leverages these underlying technologies differently but relies fundamentally on their combined strengths for security and trustworthiness.
Recent Innovations Related to Blockchain Protocols
Advancements continue shaping how blockchain systems operate:
- Enhanced Security Measures: Newer protocols aim at reducing vulnerabilities exposed during incidents like ransomware attacks involving educational institutions such as PowerSchool’s 2025 breach.
- Legal Developments Around NFTs: Ongoing legal battles over intellectual property rights associated with popular collections like Bored Ape Yacht Club highlight evolving regulatory landscapes affecting how blockchains handle ownership verification.
- Energy-Efficient Consensus Models: To address environmental concerns linked with PoW systems’ high energy consumption—which has garnered criticism—the industry is exploring alternatives such as Proof of Stake or hybrid models that balance security with sustainability.
These innovations demonstrate both technological progressions aimed at improving robustness while navigating emerging legal frameworks.
Addressing Challenges Through Technological Choices
Despite its strengths, blockchain faces challenges rooted in its technological design:
Regulatory uncertainty complicates widespread adoption; different jurisdictions have varying rules regarding cryptocurrencies and digital assets.
Security risks persist if implementations lack proper safeguards; incidents like ransomware breaches underscore this vulnerability despite inherent cryptographic protections.
Environmental impact remains contentious due to energy-intensive processes required by some consensus algorithms; ongoing research seeks greener solutions without compromising security standards.
By understanding these technical underpinnings—including cryptographic techniques like hashing functions & public-private key pairs—and how they interact within decentralized networks governed by specific consensus protocols—stakeholders can better evaluate both opportunities and risks associated with deploying blockchain solutions effectively.
Why It Matters for Users & Businesses
For users seeking transparency or businesses aiming for secure recordkeeping—and especially those involved in finance or digital asset management—the choice of underlying technology influences trustworthiness significantly. Knowing whether a platform uses energy-efficient proof schemes versus traditional proof-of-work helps assess sustainability alongside performance metrics such as transaction speed or scalability potential.
In summary,
Blockchain technology relies heavily on advanced cryptographic methods combined with decentralized architectures supported by various consensus mechanisms like PoW or PoS. These components work together not only to secure data but also enable innovative applications across sectors—from financial services to entertainment—all while presenting ongoing challenges related to regulation, security vulnerabilities, and environmental impact.
By staying informed about these core technologies underpinning blockchains today—and future developments—you can better understand their capabilities' scope while contributing thoughtfully toward responsible adoption strategies aligned with societal needs.
Keywords: Blockchain technology components | Cryptography in blockchain | Decentralized networks | Consensus mechanisms | Proof of Work vs Proof of Stake | Blockchain security features | Environmental impact of blockchains


Lo
2025-05-14 23:08
What blockchain or technology does it use?
What Blockchain Technology Uses: An In-Depth Overview
Understanding the core technology behind blockchain is essential for grasping its potential and limitations. At its heart, blockchain employs a combination of cryptography, decentralized networks, and consensus mechanisms to create a secure and transparent digital ledger system. This foundation allows blockchain to serve as a trustworthy platform for various applications across industries.
Cryptography: Securing Transactions
Cryptography is fundamental to blockchain's security features. It involves encrypting transaction data so that only authorized parties can access or modify it. Public-key cryptography, in particular, plays a vital role by generating unique key pairs—public keys used as addresses and private keys for signing transactions. This ensures that each transaction is authentic and tamper-proof. Additionally, cryptographic hashing functions produce fixed-length strings (hashes) from data inputs; these hashes are used to link blocks securely in the chain, making alterations detectable.
Decentralized Network Architecture
Unlike traditional centralized databases managed by single entities, blockchain operates on a decentralized network of computers called nodes. Each node maintains an identical copy of the entire ledger, which promotes transparency and resilience against failures or attacks. When new transactions occur, they are broadcasted across the network where nodes validate them through consensus mechanisms before adding them to the ledger.
Consensus Mechanisms: Validating Data Integrity
Consensus algorithms ensure all participants agree on the state of the ledger without relying on central authority. The two most common methods are Proof of Work (PoW) and Proof of Stake (PoS).
- Proof of Work requires miners to solve complex mathematical puzzles—a process that consumes significant computational power—to validate transactions and add new blocks.
- Proof of Stake, on the other hand, selects validators based on their holdings or stake in the network’s cryptocurrency value rather than computational effort.
These mechanisms prevent malicious activities like double-spending or fraudulent entries by making it costly or impractical for bad actors to manipulate data.
How Blockchain Uses These Technologies in Practice
The integration of cryptography, decentralization, and consensus protocols enables blockchain's wide-ranging applications:
- In finance—facilitating secure cross-border payments with reduced costs.
- In government—tracking expenditures transparently while safeguarding sensitive information.
- In entertainment—enabling NFT ownership verification within gaming ecosystems.
- In cybersecurity—protecting critical infrastructure from cyber threats through tamper-resistant ledgers.
Each application leverages these underlying technologies differently but relies fundamentally on their combined strengths for security and trustworthiness.
Recent Innovations Related to Blockchain Protocols
Advancements continue shaping how blockchain systems operate:
- Enhanced Security Measures: Newer protocols aim at reducing vulnerabilities exposed during incidents like ransomware attacks involving educational institutions such as PowerSchool’s 2025 breach.
- Legal Developments Around NFTs: Ongoing legal battles over intellectual property rights associated with popular collections like Bored Ape Yacht Club highlight evolving regulatory landscapes affecting how blockchains handle ownership verification.
- Energy-Efficient Consensus Models: To address environmental concerns linked with PoW systems’ high energy consumption—which has garnered criticism—the industry is exploring alternatives such as Proof of Stake or hybrid models that balance security with sustainability.
These innovations demonstrate both technological progressions aimed at improving robustness while navigating emerging legal frameworks.
Addressing Challenges Through Technological Choices
Despite its strengths, blockchain faces challenges rooted in its technological design:
Regulatory uncertainty complicates widespread adoption; different jurisdictions have varying rules regarding cryptocurrencies and digital assets.
Security risks persist if implementations lack proper safeguards; incidents like ransomware breaches underscore this vulnerability despite inherent cryptographic protections.
Environmental impact remains contentious due to energy-intensive processes required by some consensus algorithms; ongoing research seeks greener solutions without compromising security standards.
By understanding these technical underpinnings—including cryptographic techniques like hashing functions & public-private key pairs—and how they interact within decentralized networks governed by specific consensus protocols—stakeholders can better evaluate both opportunities and risks associated with deploying blockchain solutions effectively.
Why It Matters for Users & Businesses
For users seeking transparency or businesses aiming for secure recordkeeping—and especially those involved in finance or digital asset management—the choice of underlying technology influences trustworthiness significantly. Knowing whether a platform uses energy-efficient proof schemes versus traditional proof-of-work helps assess sustainability alongside performance metrics such as transaction speed or scalability potential.
In summary,
Blockchain technology relies heavily on advanced cryptographic methods combined with decentralized architectures supported by various consensus mechanisms like PoW or PoS. These components work together not only to secure data but also enable innovative applications across sectors—from financial services to entertainment—all while presenting ongoing challenges related to regulation, security vulnerabilities, and environmental impact.
By staying informed about these core technologies underpinning blockchains today—and future developments—you can better understand their capabilities' scope while contributing thoughtfully toward responsible adoption strategies aligned with societal needs.
Keywords: Blockchain technology components | Cryptography in blockchain | Decentralized networks | Consensus mechanisms | Proof of Work vs Proof of Stake | Blockchain security features | Environmental impact of blockchains
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
How Does a Sidechain Differ from Layer 2?
Understanding the differences between sidechains and layer 2 solutions is essential for anyone interested in blockchain scalability, interoperability, and security. Both approaches aim to improve blockchain performance but do so through distinct mechanisms and architectures. This article explores these differences comprehensively, providing clarity on how each solution functions within the broader cryptocurrency ecosystem.
What Is a Sidechain?
A sidechain is an independent blockchain that operates alongside a main or parent chain, such as Bitcoin or Ethereum. It connects to the main chain via a two-way peg or bridge mechanism, allowing assets—like tokens—to be transferred back and forth securely. This setup enables developers to experiment with different consensus algorithms, block times, or even entirely different cryptocurrencies without impacting the main network's stability.
Sidechains are particularly valued for their interoperability capabilities. They allow diverse blockchains to communicate seamlessly, facilitating cross-chain asset transfers and data sharing. For example, Polkadot’s relay chain connects multiple parachains (which act as sidechains), enabling them to exchange information efficiently. Similarly, Cosmos employs its hub-and-spoke model where individual zones (sidechains) connect through a central hub using its Inter-Blockchain Communication (IBC) protocol.
One of the key advantages of sidechains is their flexibility; they can be customized independently of the main chain’s ruleset while still maintaining asset transferability via secure bridges. However, this independence also introduces additional security considerations since each sidechain may have its own vulnerabilities depending on its design.
What Are Layer 2 Solutions?
Layer 2 solutions are protocols built on top of an existing blockchain network—most notably Ethereum—to enhance scalability without creating separate chains or requiring significant changes to the base layer (Layer 1). These solutions process transactions off-chain or in specialized environments while leveraging the security guarantees provided by Layer 1.
Unlike sidechains that operate as separate entities with their own consensus mechanisms, layer 2 solutions rely heavily on cryptographic proofs and smart contracts deployed directly on the main chain. Common types include state channels—where two parties conduct multiple transactions off-chain before settling—and rollups—which bundle many transactions into one batch processed on-chain at once.
Rollups have gained popularity due to their efficiency; they reduce gas costs significantly by aggregating numerous transactions into single proofs sent back to Ethereum’s mainnet for final settlement. Projects like Optimism utilize optimistic rollups that assume transactions are valid unless challenged within a dispute window; zk-Rollups use zero-knowledge proofs for even faster validation with enhanced security assurances.
Layer 2 solutions excel at increasing transaction throughput and reducing latency while maintaining high levels of security rooted in the underlying blockchain’s consensus model—a critical factor for user trust and adoption in decentralized finance (DeFi), gaming applications, and other high-demand use cases.
Key Differences Between Sidechains and Layer 2
While both approaches aim at scaling blockchains effectively, several fundamental differences set them apart:
Architecture: Sidechains are independent blockchains connected via bridges; layer 2 operates atop an existing primary chain.
Security Model: Sidechain security depends largely on its own consensus mechanism which might differ from that of the main chain; layer 2 leverages the security infrastructure of Layer 1 through cryptographic proofs.
Interoperability: Sidechains facilitate cross-chain communication more broadly across different networks; layer 2 primarily focuses on scaling within one network.
Customization & Flexibility: Developers can tailor sidechain features independently—such as consensus algorithms—while layer 2 solutions adapt existing protocols like Ethereum's smart contracts.
Complexity & Risk: Managing multiple independent chains introduces additional complexity and potential attack vectors in sidechains; layer 2 relies heavily on cryptography but benefits from established base-layer security standards.
Understanding these distinctions helps users evaluate which solution best fits specific needs such as decentralization level, speed requirements, or cross-chain compatibility.
Recent Trends & Developments
The landscape continues evolving rapidly with notable advancements:
In Sidechain Technology
Polkadot has made significant strides through parachain auctions launched in late 2021 — allowing projects to secure dedicated slots by staking tokens — fostering ecosystem growth around interoperability standards. Cosmos’ IBC protocol has seen widespread adoption among various projects aiming for seamless inter-blockchain communication across diverse networks like Terra or Binance Chain.
In Layer Two Solutions
Ethereum's transition toward Ethereum 2.0 aims at integrating various scaling techniques including rollups like Optimism and zk-Rollups developed by firms such as Matter Labs (zkSync). These technologies promise higher throughput with lower fees while preserving decentralization principles vital for DeFi platforms’ integrity.
Furthermore, Polygon combines both approaches by offering multi-layered scalability options—including Plasma chains (a form of optimistic rollup) alongside traditional sidechaining—to provide flexible tools suited for different application demands across ecosystems seeking scalable yet secure infrastructure options.
Challenges Facing Both Approaches
Despite promising developments , both sides face hurdles:
Security Concerns
Sidechains' independence means they may not inherit all safety features from their parent chains—a potential vulnerability if not properly secured against attacks like double-spending or bridge exploits.Layer two systems depend heavily on cryptographic proofs' correctness; any flaw could compromise entire transaction batches leading to loss of funds or data breaches.
Regulatory Uncertainty
As governments scrutinize crypto activities more closely , regulatory ambiguity surrounding new scaling methods could hinder widespread adoption until clearer legal frameworks emerge globally.
Adoption Barriers
For either solution type to succeed long-term , broad acceptance among developers , exchanges , wallets ,and end-users is crucial . Seamless integration into existing infrastructure remains vital but challenging due to technical complexity.
Final Thoughts
Both sidechains and layer two solutions play pivotal roles in shaping future blockchain scalability strategies . While they serve similar goals — increasing transaction capacity without sacrificing decentralization—they do so through fundamentally different architectures suited for varied use cases ranging from cross-chain interoperability to high-speed microtransactions .
As ongoing innovations continue addressing current limitations related to security risks,Cross-platform compatibility,and regulatory clarity,their combined evolution will likely define how scalable,decentralizedblockchain networks become over time . Staying informed about these developments ensures stakeholders can make educated decisions aligned with technological progressions shaping tomorrow’s decentralized world


JCUSER-WVMdslBw
2025-05-09 13:13
How does a sidechain differ from layer 2?
How Does a Sidechain Differ from Layer 2?
Understanding the differences between sidechains and layer 2 solutions is essential for anyone interested in blockchain scalability, interoperability, and security. Both approaches aim to improve blockchain performance but do so through distinct mechanisms and architectures. This article explores these differences comprehensively, providing clarity on how each solution functions within the broader cryptocurrency ecosystem.
What Is a Sidechain?
A sidechain is an independent blockchain that operates alongside a main or parent chain, such as Bitcoin or Ethereum. It connects to the main chain via a two-way peg or bridge mechanism, allowing assets—like tokens—to be transferred back and forth securely. This setup enables developers to experiment with different consensus algorithms, block times, or even entirely different cryptocurrencies without impacting the main network's stability.
Sidechains are particularly valued for their interoperability capabilities. They allow diverse blockchains to communicate seamlessly, facilitating cross-chain asset transfers and data sharing. For example, Polkadot’s relay chain connects multiple parachains (which act as sidechains), enabling them to exchange information efficiently. Similarly, Cosmos employs its hub-and-spoke model where individual zones (sidechains) connect through a central hub using its Inter-Blockchain Communication (IBC) protocol.
One of the key advantages of sidechains is their flexibility; they can be customized independently of the main chain’s ruleset while still maintaining asset transferability via secure bridges. However, this independence also introduces additional security considerations since each sidechain may have its own vulnerabilities depending on its design.
What Are Layer 2 Solutions?
Layer 2 solutions are protocols built on top of an existing blockchain network—most notably Ethereum—to enhance scalability without creating separate chains or requiring significant changes to the base layer (Layer 1). These solutions process transactions off-chain or in specialized environments while leveraging the security guarantees provided by Layer 1.
Unlike sidechains that operate as separate entities with their own consensus mechanisms, layer 2 solutions rely heavily on cryptographic proofs and smart contracts deployed directly on the main chain. Common types include state channels—where two parties conduct multiple transactions off-chain before settling—and rollups—which bundle many transactions into one batch processed on-chain at once.
Rollups have gained popularity due to their efficiency; they reduce gas costs significantly by aggregating numerous transactions into single proofs sent back to Ethereum’s mainnet for final settlement. Projects like Optimism utilize optimistic rollups that assume transactions are valid unless challenged within a dispute window; zk-Rollups use zero-knowledge proofs for even faster validation with enhanced security assurances.
Layer 2 solutions excel at increasing transaction throughput and reducing latency while maintaining high levels of security rooted in the underlying blockchain’s consensus model—a critical factor for user trust and adoption in decentralized finance (DeFi), gaming applications, and other high-demand use cases.
Key Differences Between Sidechains and Layer 2
While both approaches aim at scaling blockchains effectively, several fundamental differences set them apart:
Architecture: Sidechains are independent blockchains connected via bridges; layer 2 operates atop an existing primary chain.
Security Model: Sidechain security depends largely on its own consensus mechanism which might differ from that of the main chain; layer 2 leverages the security infrastructure of Layer 1 through cryptographic proofs.
Interoperability: Sidechains facilitate cross-chain communication more broadly across different networks; layer 2 primarily focuses on scaling within one network.
Customization & Flexibility: Developers can tailor sidechain features independently—such as consensus algorithms—while layer 2 solutions adapt existing protocols like Ethereum's smart contracts.
Complexity & Risk: Managing multiple independent chains introduces additional complexity and potential attack vectors in sidechains; layer 2 relies heavily on cryptography but benefits from established base-layer security standards.
Understanding these distinctions helps users evaluate which solution best fits specific needs such as decentralization level, speed requirements, or cross-chain compatibility.
Recent Trends & Developments
The landscape continues evolving rapidly with notable advancements:
In Sidechain Technology
Polkadot has made significant strides through parachain auctions launched in late 2021 — allowing projects to secure dedicated slots by staking tokens — fostering ecosystem growth around interoperability standards. Cosmos’ IBC protocol has seen widespread adoption among various projects aiming for seamless inter-blockchain communication across diverse networks like Terra or Binance Chain.
In Layer Two Solutions
Ethereum's transition toward Ethereum 2.0 aims at integrating various scaling techniques including rollups like Optimism and zk-Rollups developed by firms such as Matter Labs (zkSync). These technologies promise higher throughput with lower fees while preserving decentralization principles vital for DeFi platforms’ integrity.
Furthermore, Polygon combines both approaches by offering multi-layered scalability options—including Plasma chains (a form of optimistic rollup) alongside traditional sidechaining—to provide flexible tools suited for different application demands across ecosystems seeking scalable yet secure infrastructure options.
Challenges Facing Both Approaches
Despite promising developments , both sides face hurdles:
Security Concerns
Sidechains' independence means they may not inherit all safety features from their parent chains—a potential vulnerability if not properly secured against attacks like double-spending or bridge exploits.Layer two systems depend heavily on cryptographic proofs' correctness; any flaw could compromise entire transaction batches leading to loss of funds or data breaches.
Regulatory Uncertainty
As governments scrutinize crypto activities more closely , regulatory ambiguity surrounding new scaling methods could hinder widespread adoption until clearer legal frameworks emerge globally.
Adoption Barriers
For either solution type to succeed long-term , broad acceptance among developers , exchanges , wallets ,and end-users is crucial . Seamless integration into existing infrastructure remains vital but challenging due to technical complexity.
Final Thoughts
Both sidechains and layer two solutions play pivotal roles in shaping future blockchain scalability strategies . While they serve similar goals — increasing transaction capacity without sacrificing decentralization—they do so through fundamentally different architectures suited for varied use cases ranging from cross-chain interoperability to high-speed microtransactions .
As ongoing innovations continue addressing current limitations related to security risks,Cross-platform compatibility,and regulatory clarity,their combined evolution will likely define how scalable,decentralizedblockchain networks become over time . Staying informed about these developments ensures stakeholders can make educated decisions aligned with technological progressions shaping tomorrow’s decentralized world
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
The Role of Institutional Investors in Cryptocurrency Markets
Institutional investors have become increasingly influential players in the cryptocurrency landscape. Their entry into the market has not only driven significant capital inflows but also added a layer of legitimacy and stability to digital assets. Understanding their role is essential for anyone interested in the future trajectory of cryptocurrencies, whether as an investor, regulator, or industry participant.
Who Are Institutional Investors?
Institutional investors are large organizations that manage substantial sums of money on behalf of clients such as pension funds, hedge funds, university endowments, insurance companies, and family offices. Unlike individual retail investors who typically buy smaller amounts directly from exchanges or brokers, institutional investors operate at a much larger scale with sophisticated strategies and risk management protocols.
Historically focused on traditional assets like stocks and bonds, these entities have started exploring cryptocurrencies due to their potential for high returns and portfolio diversification. Their involvement signals a shift toward mainstream acceptance and recognition of digital assets as legitimate investment vehicles.
Why Are Institutional Investors Investing in Crypto?
Several factors have contributed to the increased interest from institutional players:
Market Growth & Volatility: Cryptocurrencies like Bitcoin have experienced exponential growth alongside notable volatility. This environment offers opportunities for high returns but also demands advanced risk management—something institutional investors are equipped to handle.
Regulatory Improvements: Clarification around regulations—such as approval processes for Bitcoin ETFs—has reduced uncertainties that previously hindered large-scale participation.
Technological Innovations: Development of secure custody solutions and sophisticated trading platforms has addressed major concerns about security risks associated with digital asset storage.
Diversification & Hedge Strategies: Cryptocurrencies are increasingly viewed as uncorrelated assets that can serve as hedges against inflation or economic downturns.
Recent Developments Signaling Institutional Engagement
The past few years have seen several landmark events indicating growing institutional involvement:
Introduction of Bitcoin ETFs: Exchange-Traded Funds linked to Bitcoin allow institutions to gain exposure without directly holding the cryptocurrency. This reduces operational risks related to security and custody while providing liquidity advantages.
Corporate Investments: Companies like MicroStrategy have made substantial investments in Bitcoin, positioning it as a treasury reserve asset akin to gold—a move that underscores its perceived store-of-value potential.
State-Level Initiatives: Some U.S. states are exploring innovative ways to integrate crypto into public finance systems; New Hampshire’s establishment of a Strategic Bitcoin Reserve exemplifies this trend by signaling governmental acknowledgment at state levels.
Broader Adoption Beyond Bitcoin: Investment products focusing on alternative cryptocurrencies such as Solana through specialized ETFs demonstrate diversification efforts among institutional portfolios beyond just Bitcoin.
Stablecoins & Digital Currency Use Cases: The emergence of stablecoins linked to prominent figures or institutions highlights evolving use cases—particularly settling large transactions efficiently while maintaining price stability within volatile markets.
How Do Institutional Investors Impact Cryptocurrency Markets?
The influx of institutional capital has had tangible effects:
It has contributed significantly toward pushing prices higher; for example, Bitcoin's value approached $95,000 amid increased buying activity.
Institutions employ diverse strategies—from direct purchases and futures contracts to ETF investments—to optimize risk-adjusted returns.
Their participation lends credibility which can attract further retail interest but also introduces complexities related to market influence by large trades (market impact).
However, this increased participation isn't without challenges:
Market Volatility
Large trades executed by institutions can cause sharp price swings due to liquidity constraints—a phenomenon known as "whale activity." While volatility is inherent in crypto markets anyway, significant institutional moves can amplify fluctuations temporarily.
Regulatory Risks
As more big players enter the space rapidly, regulators face pressure both from within their jurisdictions and globally—to craft frameworks that balance innovation with consumer protection—and this ongoing process may introduce uncertainties affecting market stability.
Security Concerns
With more significant sums involved comes heightened cybersecurity risks—including hacking attempts targeting exchanges or custody solutions—that could threaten investor holdings if not properly managed through robust security measures.
Potential Market Manipulation
The size advantage held by some institutions raises concerns about possible market manipulation practices such as pump-and-dump schemes or coordinated trading activities lacking sufficient oversight mechanisms currently under development worldwide.
Moving Forward: Challenges & Opportunities for Crypto’s Mainstream Adoption
Institutional involvement undeniably accelerates mainstream adoption by providing legitimacy through substantial capital flows; however it also necessitates careful regulation enforcement alongside technological advancements aimed at safeguarding investor interests across all levels—from retail traders up through giant funds managing billions worth of assets.
Efforts towards clearer regulatory frameworks will be crucial moving forward—not only protecting individual investors but ensuring sustainable growth within an evolving ecosystem where transparency becomes paramount.
Furthermore,
- Continued innovation around custody solutions will help mitigate security threats,
- Enhanced oversight mechanisms will reduce manipulation risks,
- And broader education initiatives will foster better understanding among all stakeholders about crypto’s benefits versus its inherent risks.
By addressing these areas proactively—with input from industry leaders alongside policymakers—the cryptocurrency sector can harness the full potential offered by institutional engagement while minimizing adverse fallout.
Final Thoughts on Institutional Influence in Crypto Markets
Institutional investors play an increasingly pivotal role shaping today’s cryptocurrency markets—they bring much-needed liquidity along with credibility but also pose challenges related to volatility control and regulatory compliance. As they continue expanding their footprint—with innovations like ETFs becoming more commonplace—the landscape is poised for further maturation.
For retail traders and smaller firms alike, understanding how these developments unfold remains critical—not just for navigating current conditions but preparing strategically for future shifts driven largely by big-money participants entering what was once considered a niche asset class.
This comprehensive overview aims at equipping readers with insights into how large organizations influence crypto markets today—and what lies ahead—as digital currencies inch closer toward mainstream financial ecosystems worldwide.


JCUSER-IC8sJL1q
2025-05-09 15:56
What role do institutional investors play in crypto?
The Role of Institutional Investors in Cryptocurrency Markets
Institutional investors have become increasingly influential players in the cryptocurrency landscape. Their entry into the market has not only driven significant capital inflows but also added a layer of legitimacy and stability to digital assets. Understanding their role is essential for anyone interested in the future trajectory of cryptocurrencies, whether as an investor, regulator, or industry participant.
Who Are Institutional Investors?
Institutional investors are large organizations that manage substantial sums of money on behalf of clients such as pension funds, hedge funds, university endowments, insurance companies, and family offices. Unlike individual retail investors who typically buy smaller amounts directly from exchanges or brokers, institutional investors operate at a much larger scale with sophisticated strategies and risk management protocols.
Historically focused on traditional assets like stocks and bonds, these entities have started exploring cryptocurrencies due to their potential for high returns and portfolio diversification. Their involvement signals a shift toward mainstream acceptance and recognition of digital assets as legitimate investment vehicles.
Why Are Institutional Investors Investing in Crypto?
Several factors have contributed to the increased interest from institutional players:
Market Growth & Volatility: Cryptocurrencies like Bitcoin have experienced exponential growth alongside notable volatility. This environment offers opportunities for high returns but also demands advanced risk management—something institutional investors are equipped to handle.
Regulatory Improvements: Clarification around regulations—such as approval processes for Bitcoin ETFs—has reduced uncertainties that previously hindered large-scale participation.
Technological Innovations: Development of secure custody solutions and sophisticated trading platforms has addressed major concerns about security risks associated with digital asset storage.
Diversification & Hedge Strategies: Cryptocurrencies are increasingly viewed as uncorrelated assets that can serve as hedges against inflation or economic downturns.
Recent Developments Signaling Institutional Engagement
The past few years have seen several landmark events indicating growing institutional involvement:
Introduction of Bitcoin ETFs: Exchange-Traded Funds linked to Bitcoin allow institutions to gain exposure without directly holding the cryptocurrency. This reduces operational risks related to security and custody while providing liquidity advantages.
Corporate Investments: Companies like MicroStrategy have made substantial investments in Bitcoin, positioning it as a treasury reserve asset akin to gold—a move that underscores its perceived store-of-value potential.
State-Level Initiatives: Some U.S. states are exploring innovative ways to integrate crypto into public finance systems; New Hampshire’s establishment of a Strategic Bitcoin Reserve exemplifies this trend by signaling governmental acknowledgment at state levels.
Broader Adoption Beyond Bitcoin: Investment products focusing on alternative cryptocurrencies such as Solana through specialized ETFs demonstrate diversification efforts among institutional portfolios beyond just Bitcoin.
Stablecoins & Digital Currency Use Cases: The emergence of stablecoins linked to prominent figures or institutions highlights evolving use cases—particularly settling large transactions efficiently while maintaining price stability within volatile markets.
How Do Institutional Investors Impact Cryptocurrency Markets?
The influx of institutional capital has had tangible effects:
It has contributed significantly toward pushing prices higher; for example, Bitcoin's value approached $95,000 amid increased buying activity.
Institutions employ diverse strategies—from direct purchases and futures contracts to ETF investments—to optimize risk-adjusted returns.
Their participation lends credibility which can attract further retail interest but also introduces complexities related to market influence by large trades (market impact).
However, this increased participation isn't without challenges:
Market Volatility
Large trades executed by institutions can cause sharp price swings due to liquidity constraints—a phenomenon known as "whale activity." While volatility is inherent in crypto markets anyway, significant institutional moves can amplify fluctuations temporarily.
Regulatory Risks
As more big players enter the space rapidly, regulators face pressure both from within their jurisdictions and globally—to craft frameworks that balance innovation with consumer protection—and this ongoing process may introduce uncertainties affecting market stability.
Security Concerns
With more significant sums involved comes heightened cybersecurity risks—including hacking attempts targeting exchanges or custody solutions—that could threaten investor holdings if not properly managed through robust security measures.
Potential Market Manipulation
The size advantage held by some institutions raises concerns about possible market manipulation practices such as pump-and-dump schemes or coordinated trading activities lacking sufficient oversight mechanisms currently under development worldwide.
Moving Forward: Challenges & Opportunities for Crypto’s Mainstream Adoption
Institutional involvement undeniably accelerates mainstream adoption by providing legitimacy through substantial capital flows; however it also necessitates careful regulation enforcement alongside technological advancements aimed at safeguarding investor interests across all levels—from retail traders up through giant funds managing billions worth of assets.
Efforts towards clearer regulatory frameworks will be crucial moving forward—not only protecting individual investors but ensuring sustainable growth within an evolving ecosystem where transparency becomes paramount.
Furthermore,
- Continued innovation around custody solutions will help mitigate security threats,
- Enhanced oversight mechanisms will reduce manipulation risks,
- And broader education initiatives will foster better understanding among all stakeholders about crypto’s benefits versus its inherent risks.
By addressing these areas proactively—with input from industry leaders alongside policymakers—the cryptocurrency sector can harness the full potential offered by institutional engagement while minimizing adverse fallout.
Final Thoughts on Institutional Influence in Crypto Markets
Institutional investors play an increasingly pivotal role shaping today’s cryptocurrency markets—they bring much-needed liquidity along with credibility but also pose challenges related to volatility control and regulatory compliance. As they continue expanding their footprint—with innovations like ETFs becoming more commonplace—the landscape is poised for further maturation.
For retail traders and smaller firms alike, understanding how these developments unfold remains critical—not just for navigating current conditions but preparing strategically for future shifts driven largely by big-money participants entering what was once considered a niche asset class.
This comprehensive overview aims at equipping readers with insights into how large organizations influence crypto markets today—and what lies ahead—as digital currencies inch closer toward mainstream financial ecosystems worldwide.
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
How Does Blockchain Technology Work?
Understanding the fundamentals of blockchain technology is essential for grasping its transformative potential across various industries. At its core, blockchain is a decentralized digital ledger that records transactions securely and transparently. Unlike traditional databases managed by central authorities, blockchain distributes data across a network of computers, ensuring no single point of control or failure.
Decentralization is one of the key features that make blockchain unique. Each participant in the network, often called a node, holds an identical copy of the entire ledger. This setup not only enhances security but also promotes transparency because every transaction recorded on the blockchain is visible to all participants. This transparency fosters trust among users and reduces reliance on intermediaries.
The process begins with transaction verification. When someone initiates a transaction—such as transferring cryptocurrency or recording data—the transaction must be validated by nodes within the network. These nodes use consensus mechanisms like proof-of-work (PoW) or proof-of-stake (PoS) to agree on whether the transaction is legitimate before it can be added to the chain.
Once verified, transactions are grouped into blocks. Each block contains multiple transactions along with metadata such as timestamps and cryptographic hashes linking it to previous blocks in the chain—a process known as chaining blocks together cryptographically. This linkage ensures that once a block has been added, altering any information within it would require changing all subsequent blocks—a computationally infeasible task under normal circumstances.
Adding new blocks involves miners or validators performing complex computations (in PoW systems) or staking tokens (in PoS systems). For example, Bitcoin’s proof-of-work requires miners to solve mathematical puzzles; this process consumes significant energy but secures the network against malicious attacks by making tampering costly and resource-intensive.
Cryptography plays an integral role throughout this process—securing data through algorithms such as hashing functions and public-private key encryption. Hash functions generate unique identifiers for each block; any change in data results in a different hash value, alerting participants to potential tampering attempts.
The immutability feature means that once data has been recorded onto a block and added to the chain, it cannot be altered retroactively without detection—this property builds trustworthiness into blockchain applications ranging from financial services to supply chain management.
Blockchain's origins trace back to 2008 when Satoshi Nakamoto published his whitepaper introducing Bitcoin—a peer-to-peer electronic cash system utilizing blockchain technology for secure digital currency transactions without centralized oversight. Since then, innovations have expanded beyond cryptocurrencies into areas like smart contracts—self-executing agreements coded directly onto blockchains—and decentralized finance (DeFi), which offers financial services without traditional intermediaries.
Despite its strengths, understanding how blockchain works also involves recognizing current challenges such as scalability issues where networks struggle with high transaction volumes; environmental concerns due to energy-intensive mining processes; regulatory uncertainties affecting adoption; and security vulnerabilities related mainly to smart contract bugs rather than inherent flaws in underlying protocols.
In summary, blockchain operates through a combination of decentralization, cryptographic security measures, consensus mechanisms for validating transactions—and immutable record-keeping—that collectively create transparent yet secure digital ledgers capable of transforming numerous sectors beyond just cryptocurrencies.


JCUSER-IC8sJL1q
2025-05-14 05:39
How does blockchain technology work?
How Does Blockchain Technology Work?
Understanding the fundamentals of blockchain technology is essential for grasping its transformative potential across various industries. At its core, blockchain is a decentralized digital ledger that records transactions securely and transparently. Unlike traditional databases managed by central authorities, blockchain distributes data across a network of computers, ensuring no single point of control or failure.
Decentralization is one of the key features that make blockchain unique. Each participant in the network, often called a node, holds an identical copy of the entire ledger. This setup not only enhances security but also promotes transparency because every transaction recorded on the blockchain is visible to all participants. This transparency fosters trust among users and reduces reliance on intermediaries.
The process begins with transaction verification. When someone initiates a transaction—such as transferring cryptocurrency or recording data—the transaction must be validated by nodes within the network. These nodes use consensus mechanisms like proof-of-work (PoW) or proof-of-stake (PoS) to agree on whether the transaction is legitimate before it can be added to the chain.
Once verified, transactions are grouped into blocks. Each block contains multiple transactions along with metadata such as timestamps and cryptographic hashes linking it to previous blocks in the chain—a process known as chaining blocks together cryptographically. This linkage ensures that once a block has been added, altering any information within it would require changing all subsequent blocks—a computationally infeasible task under normal circumstances.
Adding new blocks involves miners or validators performing complex computations (in PoW systems) or staking tokens (in PoS systems). For example, Bitcoin’s proof-of-work requires miners to solve mathematical puzzles; this process consumes significant energy but secures the network against malicious attacks by making tampering costly and resource-intensive.
Cryptography plays an integral role throughout this process—securing data through algorithms such as hashing functions and public-private key encryption. Hash functions generate unique identifiers for each block; any change in data results in a different hash value, alerting participants to potential tampering attempts.
The immutability feature means that once data has been recorded onto a block and added to the chain, it cannot be altered retroactively without detection—this property builds trustworthiness into blockchain applications ranging from financial services to supply chain management.
Blockchain's origins trace back to 2008 when Satoshi Nakamoto published his whitepaper introducing Bitcoin—a peer-to-peer electronic cash system utilizing blockchain technology for secure digital currency transactions without centralized oversight. Since then, innovations have expanded beyond cryptocurrencies into areas like smart contracts—self-executing agreements coded directly onto blockchains—and decentralized finance (DeFi), which offers financial services without traditional intermediaries.
Despite its strengths, understanding how blockchain works also involves recognizing current challenges such as scalability issues where networks struggle with high transaction volumes; environmental concerns due to energy-intensive mining processes; regulatory uncertainties affecting adoption; and security vulnerabilities related mainly to smart contract bugs rather than inherent flaws in underlying protocols.
In summary, blockchain operates through a combination of decentralization, cryptographic security measures, consensus mechanisms for validating transactions—and immutable record-keeping—that collectively create transparent yet secure digital ledgers capable of transforming numerous sectors beyond just cryptocurrencies.
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
What Are the Inherent Risks of Interacting with DeFi Protocols?
Decentralized Finance (DeFi) has emerged as a transformative force in the financial industry, offering innovative ways to lend, borrow, trade, and earn yields without traditional intermediaries. While DeFi provides increased accessibility and transparency, it also introduces a range of inherent risks that users must understand before engaging. This article explores these risks comprehensively to help users navigate the complex landscape of DeFi safely.
Understanding Smart Contract Vulnerabilities
At the core of DeFi protocols are smart contracts—self-executing code that automates financial transactions based on predefined rules. Although they enable trustless operations, smart contracts are susceptible to bugs and vulnerabilities. Historically significant incidents like the DAO hack in 2016 demonstrated how exploited vulnerabilities could lead to massive losses; approximately 3.6 million Ether were drained due to a reentrancy bug[1]. These vulnerabilities often stem from coding errors or overlooked edge cases during development. As smart contracts are immutable once deployed, fixing such issues post-launch can be challenging and costly.
To mitigate this risk, rigorous security audits by third-party firms are essential before deploying new protocols or updates. Additionally, ongoing monitoring and bug bounty programs incentivize community participation in identifying potential flaws early.
Liquidity Risks in Decentralized Pools
Liquidity is vital for smooth trading and borrowing activities within DeFi ecosystems. Many protocols rely on liquidity pools—collections of tokens supplied by users—to facilitate transactions without centralized order books[2]. However, these pools can face liquidity shortages during periods of high volatility or market downturns. Insufficient liquidity can lead to slippage—where trades execute at unfavorable prices—or even transaction failures.
For example, during sudden market crashes or large trades (known as "whale" movements), prices may swing sharply due to low liquidity levels[3]. Users participating in yield farming or providing liquidity should be aware that their assets might become illiquid if market conditions deteriorate unexpectedly.
Market Volatility Impact
Cryptocurrencies used within DeFi platforms are inherently volatile assets; their values can fluctuate dramatically over short periods[3]. Such volatility directly affects collateral valuations in lending protocols and impacts yield calculations for farmers earning interest or rewards. A sudden price drop could trigger liquidation events where collateral is sold off automatically at unfavorable rates—a process known as "liquidation risk."
This unpredictability underscores the importance for users engaging with leverage-based strategies or staking assets: they must closely monitor market trends and set appropriate risk parameters like collateralization ratios to avoid unexpected losses.
Regulatory Uncertainty Surrounding DeFi
The regulatory landscape for DeFi remains largely undefined globally[4]. Governments and regulators are increasingly scrutinizing decentralized platforms due to concerns about consumer protection, money laundering risks, tax evasion potential—and whether existing laws apply effectively within decentralized environments.
This ambiguity exposes users and platform operators to legal uncertainties; regulations could change abruptly leading to restrictions on certain activities or shutdowns of platforms altogether[4]. Staying informed about evolving legal frameworks is crucial for participants who wish to avoid unintended compliance violations while maintaining access.
Security Threats: Phishing & Hacks
Beyond technical vulnerabilities within smart contracts themselves lies an array of security threats targeting individual users’ funds[5]. Phishing attacks remain prevalent—attackers impersonate legitimate services via fake websites or emails designed specifically to steal private keys or seed phrases necessary for wallet access(5). Once compromised, hackers can drain user accounts instantly.
High-profile hacks such as Wormhole’s $320 million breach in 2022 highlight how security lapses at bridge infrastructure points pose significant risks [10], emphasizing that no component is immune from attack vectors targeting cross-chain interoperability solutions used widely across DeFi ecosystems.
Users should adopt best practices including multi-factor authentication (MFA), hardware wallets when possible—and always verify URLs—to reduce susceptibility toward phishing schemes [5].
Reentrancy Attacks: A Persistent Threat
Reentrancy attacks exploit specific vulnerabilities where malicious actors repeatedly call functions within a contract before previous executions complete[6]. This loophole allows attackers unauthorized access—potentially draining funds from affected protocols if not properly guarded against reentrant calls(6).
The infamous DAO hack was an early example illustrating this threat’s severity [1], prompting developers worldwide toward implementing safeguards like mutexes (mutual exclusions) into their codebases today [6].
Ensuring robust coding standards combined with formal verification methods significantly reduces reentrancy-related exploits' likelihood across new protocol deployments.
Front-Running & Sandwich Attacks Exploiting Transaction Ordering
In blockchain networks where transaction ordering isn’t strictly controlled by centralized authorities—the phenomenon known as front-running becomes problematic.[7] Traders with faster access may observe pending transactions via mempool data—and place their own orders ahead intentionally (“front-run”) —altering prices unfavorably for others(7).
Sandwich attacks take this further by placing one order just before a target trade while another immediately afterward—effectively “sandwiching” it—to manipulate asset prices temporarily.[7] These tactics undermine fair trading principles within DEXs like Uniswap but also pose financial risks for regular traders unfamiliar with such exploits.[7]
Mitigation strategies include implementing time-weighted average pricing mechanisms (TWAP)and utilizing privacy-preserving techniques such as zero-knowledge proofs where feasible .
Dependence on Oracles & Data Integrity Issues
Many advanced DeFi applications depend heavily on external data sources called “oracles” — which provide real-time information like asset prices,[8] interest rates,[8] etc., necessary for executing automated decisions accurately(8). However , inaccuracies stemming from faulty data feeds—or malicious manipulation—can cause severe miscalculations leading either into unwarranted liquidationsor incorrect payouts(8).
Protocols employing multiple independent oracle sources coupled with decentralization techniques aimto improve resilience against false data injection but cannot eliminate all associated risks entirely .
Navigating the Risks: Best Practices & Future Outlook
While inherent dangers exist across various facets—from technical bugs through regulatory shifts—the key lies in adopting comprehensive risk management strategies . Regularly auditing codebases , diversifying investments , employing secure wallets , staying updated about legal developments ,and understanding protocol mechanics form partof prudent engagement practices .
Recent developments indicate increased focus on enhancing security measures—including more rigorous audits post-hack incidents—as well as efforts towards clearer regulation frameworks aimed at protecting investors while fostering innovation . As the ecosystem matures—with improved standards around transparency,safety,and compliance—the overall safety profile will likely improve over time—but vigilance remains essentialfor all participants involvedin decentralized finance activities.


JCUSER-WVMdslBw
2025-05-22 08:07
What are the inherent risks involved in interacting with DeFi protocols?
What Are the Inherent Risks of Interacting with DeFi Protocols?
Decentralized Finance (DeFi) has emerged as a transformative force in the financial industry, offering innovative ways to lend, borrow, trade, and earn yields without traditional intermediaries. While DeFi provides increased accessibility and transparency, it also introduces a range of inherent risks that users must understand before engaging. This article explores these risks comprehensively to help users navigate the complex landscape of DeFi safely.
Understanding Smart Contract Vulnerabilities
At the core of DeFi protocols are smart contracts—self-executing code that automates financial transactions based on predefined rules. Although they enable trustless operations, smart contracts are susceptible to bugs and vulnerabilities. Historically significant incidents like the DAO hack in 2016 demonstrated how exploited vulnerabilities could lead to massive losses; approximately 3.6 million Ether were drained due to a reentrancy bug[1]. These vulnerabilities often stem from coding errors or overlooked edge cases during development. As smart contracts are immutable once deployed, fixing such issues post-launch can be challenging and costly.
To mitigate this risk, rigorous security audits by third-party firms are essential before deploying new protocols or updates. Additionally, ongoing monitoring and bug bounty programs incentivize community participation in identifying potential flaws early.
Liquidity Risks in Decentralized Pools
Liquidity is vital for smooth trading and borrowing activities within DeFi ecosystems. Many protocols rely on liquidity pools—collections of tokens supplied by users—to facilitate transactions without centralized order books[2]. However, these pools can face liquidity shortages during periods of high volatility or market downturns. Insufficient liquidity can lead to slippage—where trades execute at unfavorable prices—or even transaction failures.
For example, during sudden market crashes or large trades (known as "whale" movements), prices may swing sharply due to low liquidity levels[3]. Users participating in yield farming or providing liquidity should be aware that their assets might become illiquid if market conditions deteriorate unexpectedly.
Market Volatility Impact
Cryptocurrencies used within DeFi platforms are inherently volatile assets; their values can fluctuate dramatically over short periods[3]. Such volatility directly affects collateral valuations in lending protocols and impacts yield calculations for farmers earning interest or rewards. A sudden price drop could trigger liquidation events where collateral is sold off automatically at unfavorable rates—a process known as "liquidation risk."
This unpredictability underscores the importance for users engaging with leverage-based strategies or staking assets: they must closely monitor market trends and set appropriate risk parameters like collateralization ratios to avoid unexpected losses.
Regulatory Uncertainty Surrounding DeFi
The regulatory landscape for DeFi remains largely undefined globally[4]. Governments and regulators are increasingly scrutinizing decentralized platforms due to concerns about consumer protection, money laundering risks, tax evasion potential—and whether existing laws apply effectively within decentralized environments.
This ambiguity exposes users and platform operators to legal uncertainties; regulations could change abruptly leading to restrictions on certain activities or shutdowns of platforms altogether[4]. Staying informed about evolving legal frameworks is crucial for participants who wish to avoid unintended compliance violations while maintaining access.
Security Threats: Phishing & Hacks
Beyond technical vulnerabilities within smart contracts themselves lies an array of security threats targeting individual users’ funds[5]. Phishing attacks remain prevalent—attackers impersonate legitimate services via fake websites or emails designed specifically to steal private keys or seed phrases necessary for wallet access(5). Once compromised, hackers can drain user accounts instantly.
High-profile hacks such as Wormhole’s $320 million breach in 2022 highlight how security lapses at bridge infrastructure points pose significant risks [10], emphasizing that no component is immune from attack vectors targeting cross-chain interoperability solutions used widely across DeFi ecosystems.
Users should adopt best practices including multi-factor authentication (MFA), hardware wallets when possible—and always verify URLs—to reduce susceptibility toward phishing schemes [5].
Reentrancy Attacks: A Persistent Threat
Reentrancy attacks exploit specific vulnerabilities where malicious actors repeatedly call functions within a contract before previous executions complete[6]. This loophole allows attackers unauthorized access—potentially draining funds from affected protocols if not properly guarded against reentrant calls(6).
The infamous DAO hack was an early example illustrating this threat’s severity [1], prompting developers worldwide toward implementing safeguards like mutexes (mutual exclusions) into their codebases today [6].
Ensuring robust coding standards combined with formal verification methods significantly reduces reentrancy-related exploits' likelihood across new protocol deployments.
Front-Running & Sandwich Attacks Exploiting Transaction Ordering
In blockchain networks where transaction ordering isn’t strictly controlled by centralized authorities—the phenomenon known as front-running becomes problematic.[7] Traders with faster access may observe pending transactions via mempool data—and place their own orders ahead intentionally (“front-run”) —altering prices unfavorably for others(7).
Sandwich attacks take this further by placing one order just before a target trade while another immediately afterward—effectively “sandwiching” it—to manipulate asset prices temporarily.[7] These tactics undermine fair trading principles within DEXs like Uniswap but also pose financial risks for regular traders unfamiliar with such exploits.[7]
Mitigation strategies include implementing time-weighted average pricing mechanisms (TWAP)and utilizing privacy-preserving techniques such as zero-knowledge proofs where feasible .
Dependence on Oracles & Data Integrity Issues
Many advanced DeFi applications depend heavily on external data sources called “oracles” — which provide real-time information like asset prices,[8] interest rates,[8] etc., necessary for executing automated decisions accurately(8). However , inaccuracies stemming from faulty data feeds—or malicious manipulation—can cause severe miscalculations leading either into unwarranted liquidationsor incorrect payouts(8).
Protocols employing multiple independent oracle sources coupled with decentralization techniques aimto improve resilience against false data injection but cannot eliminate all associated risks entirely .
Navigating the Risks: Best Practices & Future Outlook
While inherent dangers exist across various facets—from technical bugs through regulatory shifts—the key lies in adopting comprehensive risk management strategies . Regularly auditing codebases , diversifying investments , employing secure wallets , staying updated about legal developments ,and understanding protocol mechanics form partof prudent engagement practices .
Recent developments indicate increased focus on enhancing security measures—including more rigorous audits post-hack incidents—as well as efforts towards clearer regulation frameworks aimed at protecting investors while fostering innovation . As the ecosystem matures—with improved standards around transparency,safety,and compliance—the overall safety profile will likely improve over time—but vigilance remains essentialfor all participants involvedin decentralized finance activities.
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
