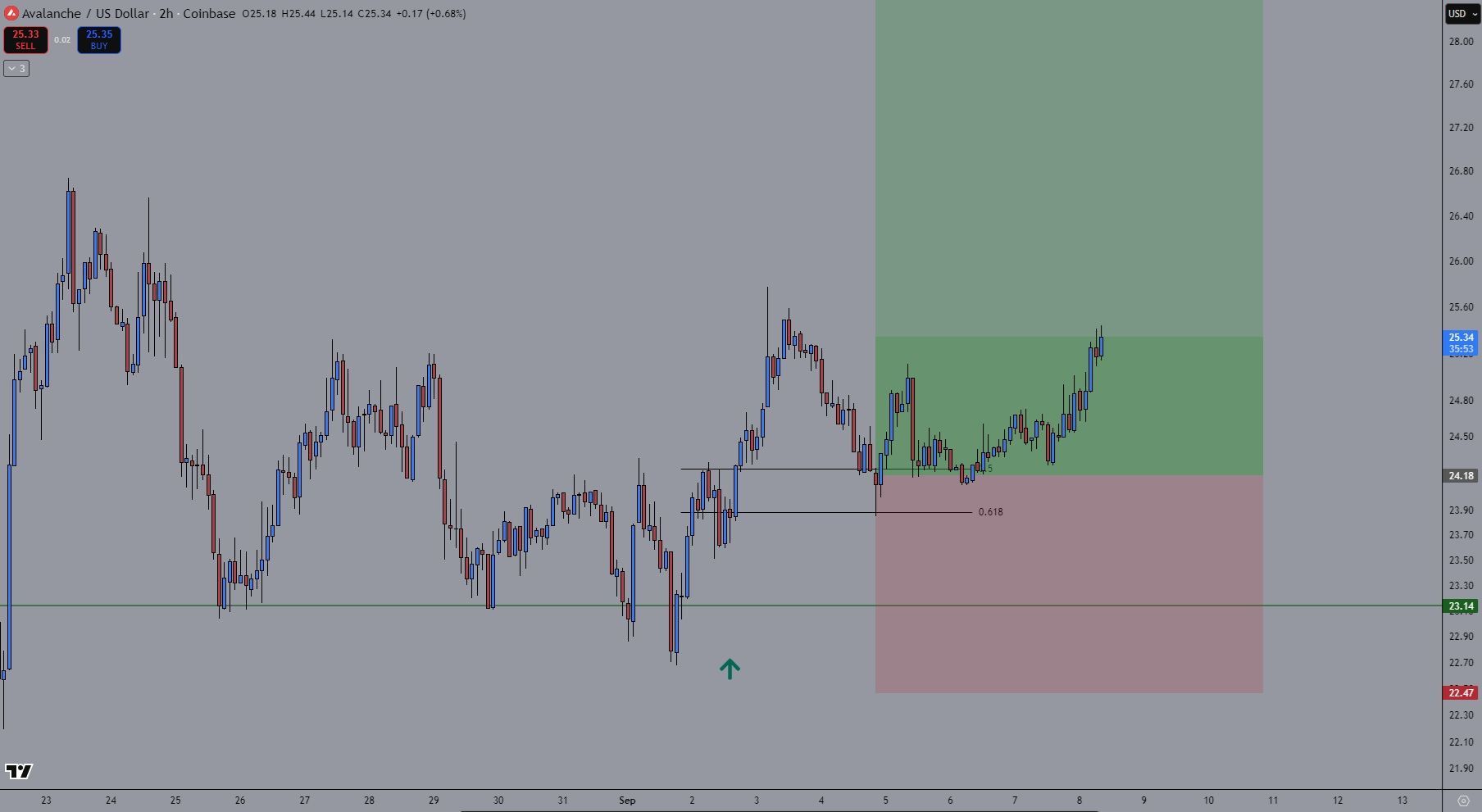
👀 La force se manifeste comme anticipé, renforçant la confiance dans les positions.
📊 Avec le momentum qui s’installe, les regards se tournent désormais vers des objectifs bien au-dessus de $30.
$AVAX/USDT ?
#Avalanche #AVAX #blockchain #cryptocurrency


Carmelita
2025-09-08 16:07
💥 $AVAX tient parfaitement sa zone clé de $23–24 !
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
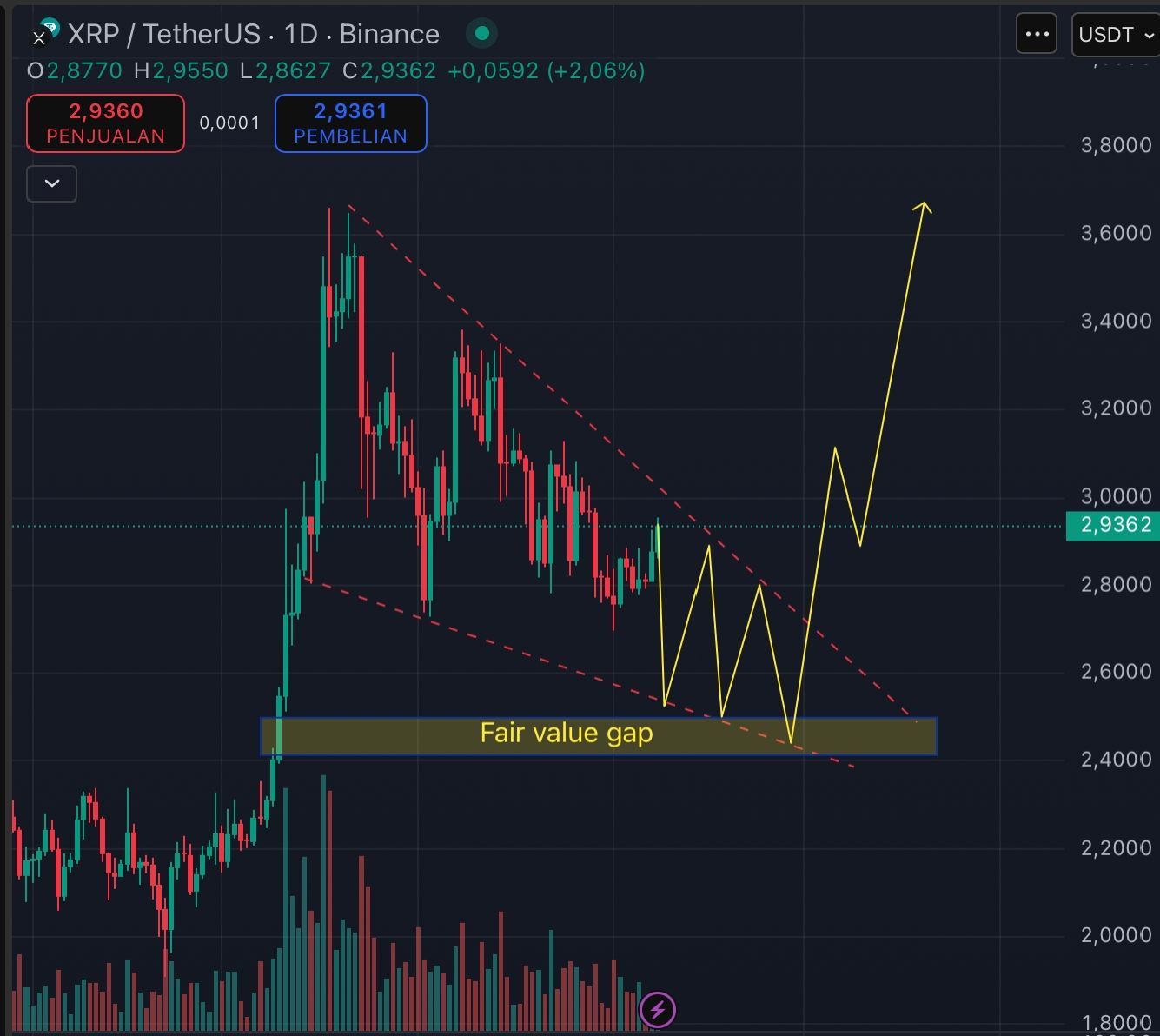
$XRP/USDT Corrective pullback → réaccumulation probable avant le prochain move haussier. 💡 Spot : buy the dips near channel support ou breakout H4 > 3,13. ❌ Invalidation : breakdown sous FVG.
👉 Prêt à anticiper le breakout avant les masses ?
#XRP #CryptoTrading #cryptocurrency #blockchain


Carmelita
2025-09-08 13:46
$XRP pause après l’ATH… opportunité d’accumulation ou simple correction ?
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
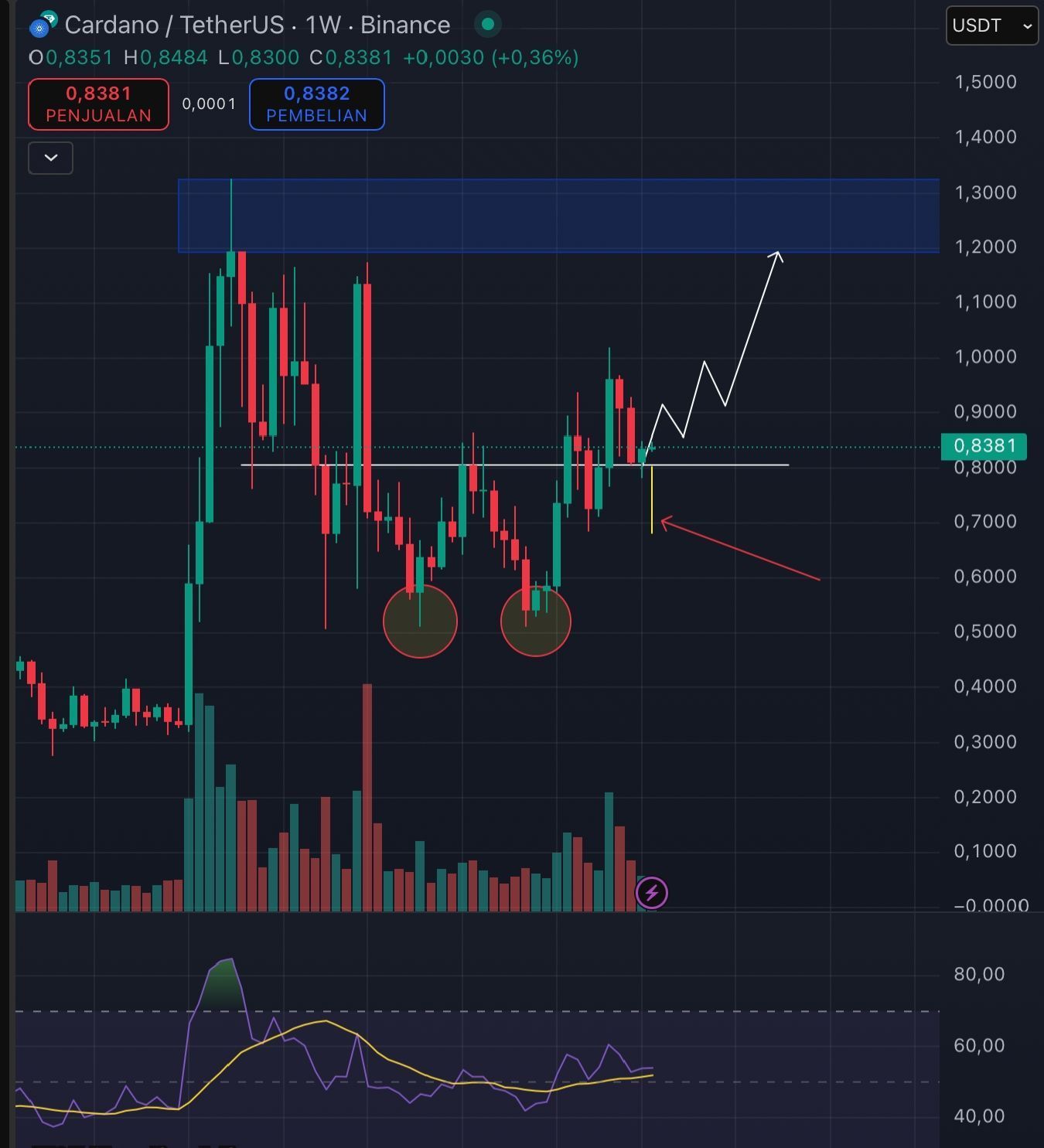
$ADA/USDT tient au-dessus de la neckline du double-bottom (0.8051) — une zone S/R cruciale. Un petit wick en dessous = simple chasse à la liquidité. Tant que les clôtures hebdo restent au-dessus, le biais reste bullish.
💡 Stratégie : DCA entre 0.80–0.83 → mais attention : invalidation si clôture journalière sous la zone, avec momentum.
👉 Signal de recharge discrète ou simple piège à acheteurs impatients ?
#Cardano #ADA #cryptocurrency #blockchain


Carmelita
2025-09-08 11:50
👀 Cardano joue avec le feu… mais reste solide.
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
$XRP/USDT Un actif longtemps sous pression, mais qui reste un classique du cycle crypto. Après plus d’un demi-siècle de consolidation et d’incertitude réglementaire, la conviction grandit : le prochain mouvement pourrait surprendre. 👀
📊 Setup technique : 🔹 Zone d’achat possible sous les récents creux 🔹 Objectifs ambitieux : $7–$10 sur la prochaine vague
👉 $XRP reste un “if you know, you know” asset : un pari où patience et timing peuvent tout changer.
#cryptocurrency #blockchain #Cryptocurrency


Carmelita
2025-09-07 22:26
💥 $XRP: The Sleeper Giant?
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
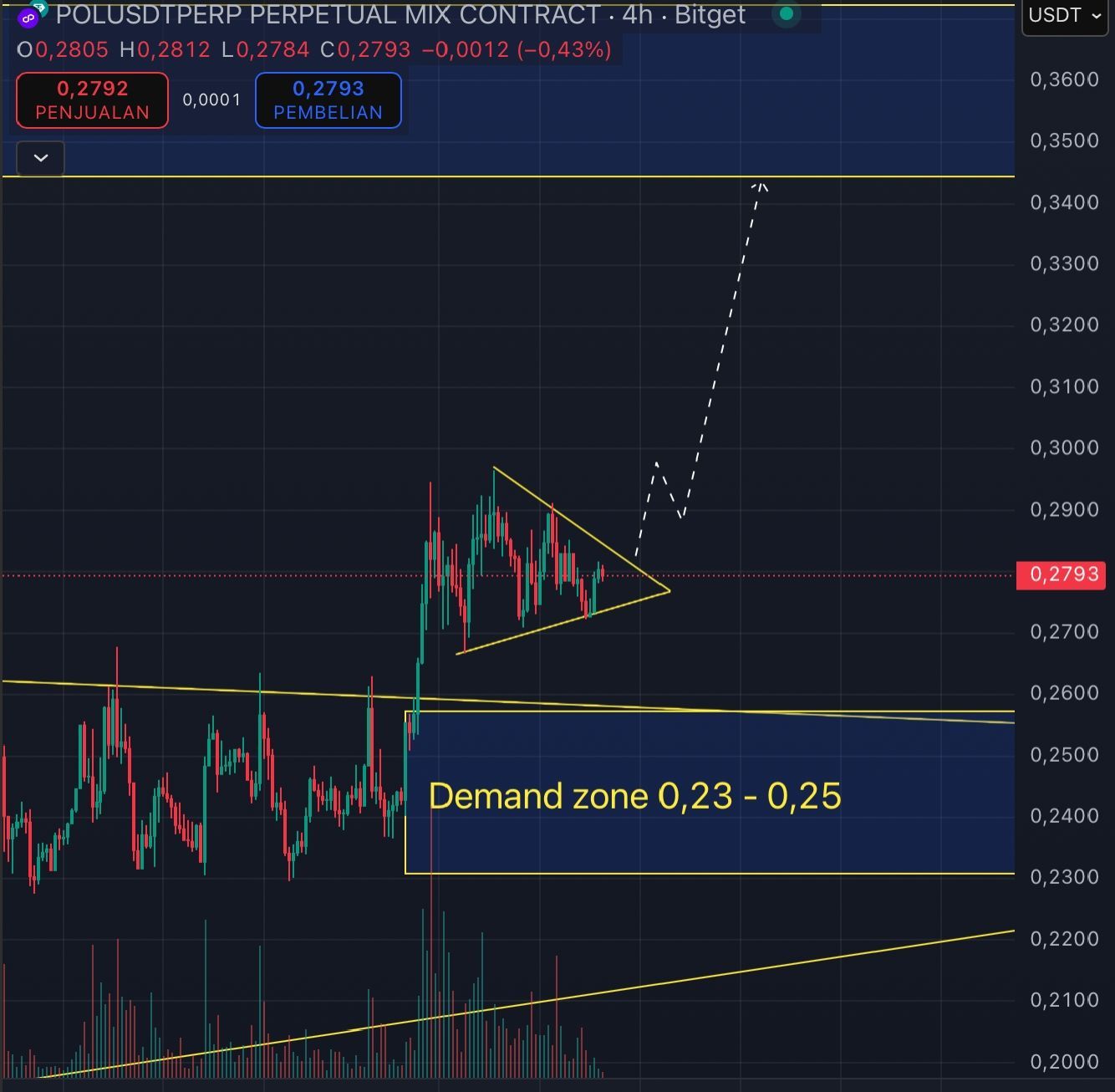
$POL/USDT vient de sortir d’une consolidation de plusieurs mois avec un volume solide → signal de momentum haussier. 🚀
⏳ 4H Chart : Symmetrical triangle (continuation) en formation. 🔑 Key level : $0.30
✅ Entry : Breakout au-dessus de $0.30 ou retest réussi ❌ Invalidation : Clôture H4 sous $0.266
🎯 Targets : • TP1 → $0.31 • TP2 → $0.33 • TP3 → $0.37
#cryptocurrency #blockchain #trading strategies #technical analysis #JuCoin


Carmelita
2025-09-07 13:15
📈 $POL Outlook
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
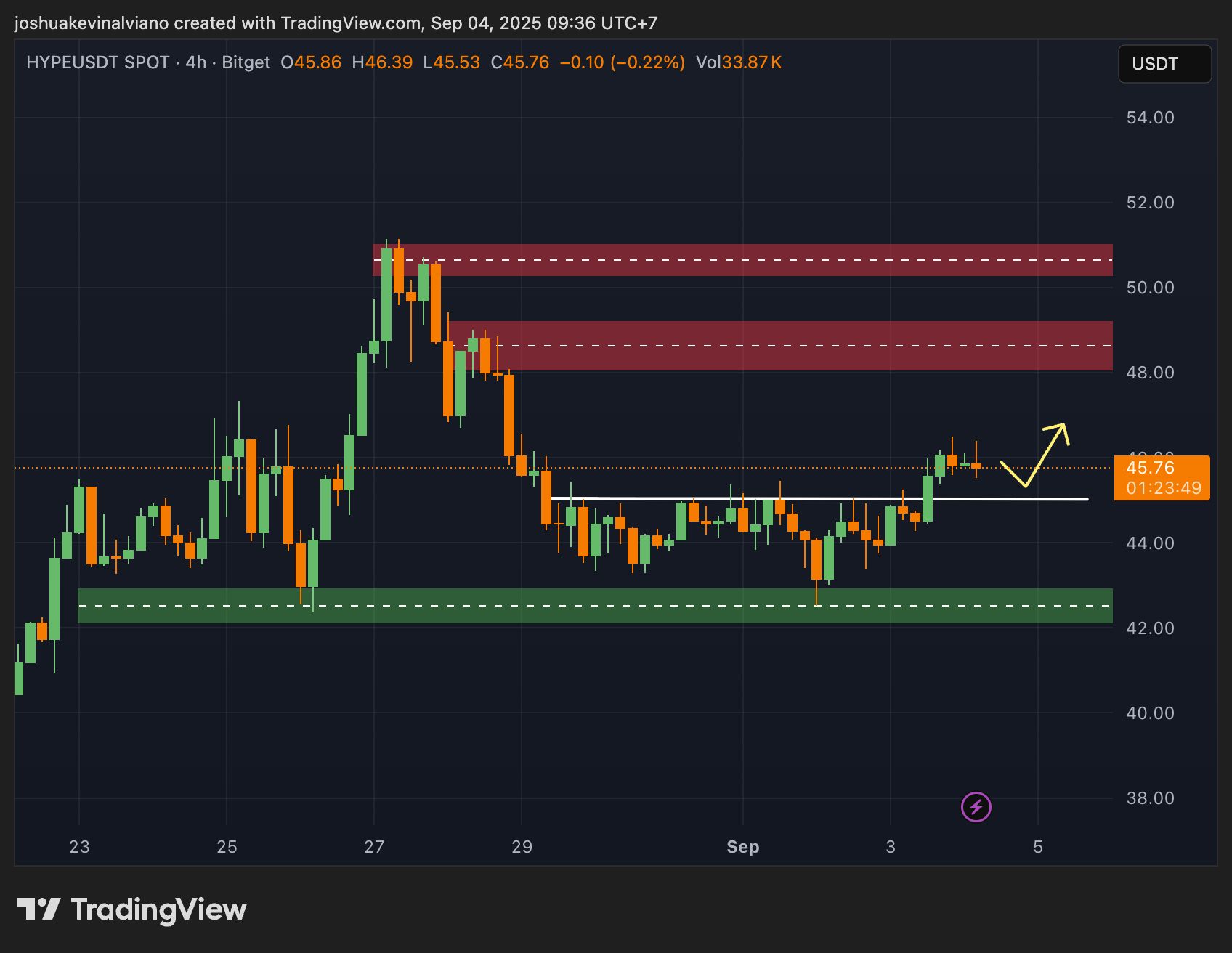
Sur le 4H, $HYPE tente un breakout avec prise de liquidité en vue 👀
✅ Au-dessus de $45 → possible run vers la zone $48–50 ❌ Sous $45 → retour probable vers la demande à $42
Momentum en train de chauffer… le breakout tiendra-t-il la distance ? 🚀
#hype #cryptotrading #cryptocurrency #blockchain #JuCoin


Carmelita
2025-09-07 11:34
⚡ $HYPE Breakout Watch
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
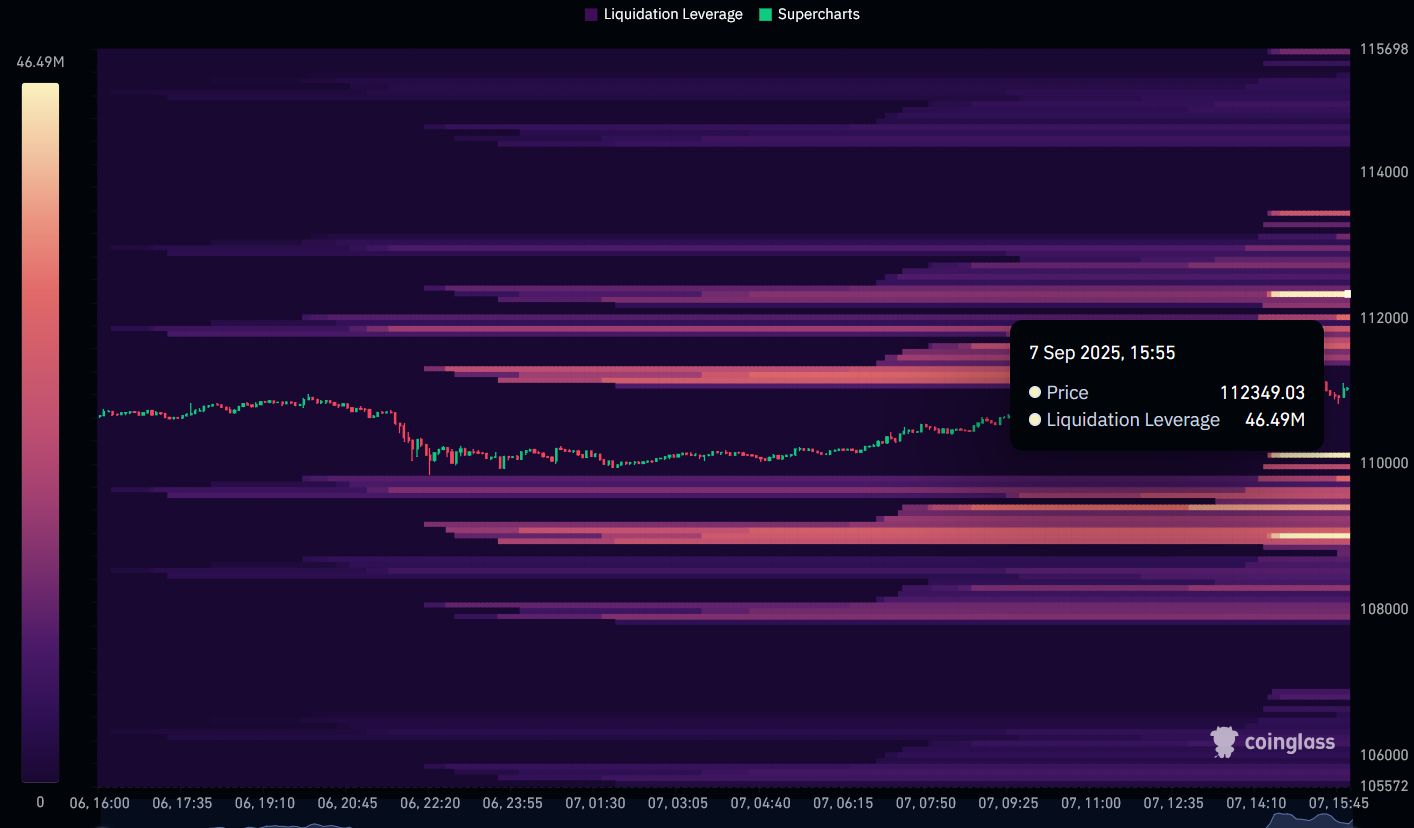
👉 Avec $46.49M de levier en liquidation positionné à ce niveau.
Des clusters s’accumulent au-dessus & en dessous… ⚡ La volatilité s’annonce explosive. 👀
#Bitcoin #CryptoMarkets #BTC #cryptocurrency #blockchain


Carmelita
2025-09-07 11:42
🚨 JUST IN: $BTC vient de taper $112,349
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
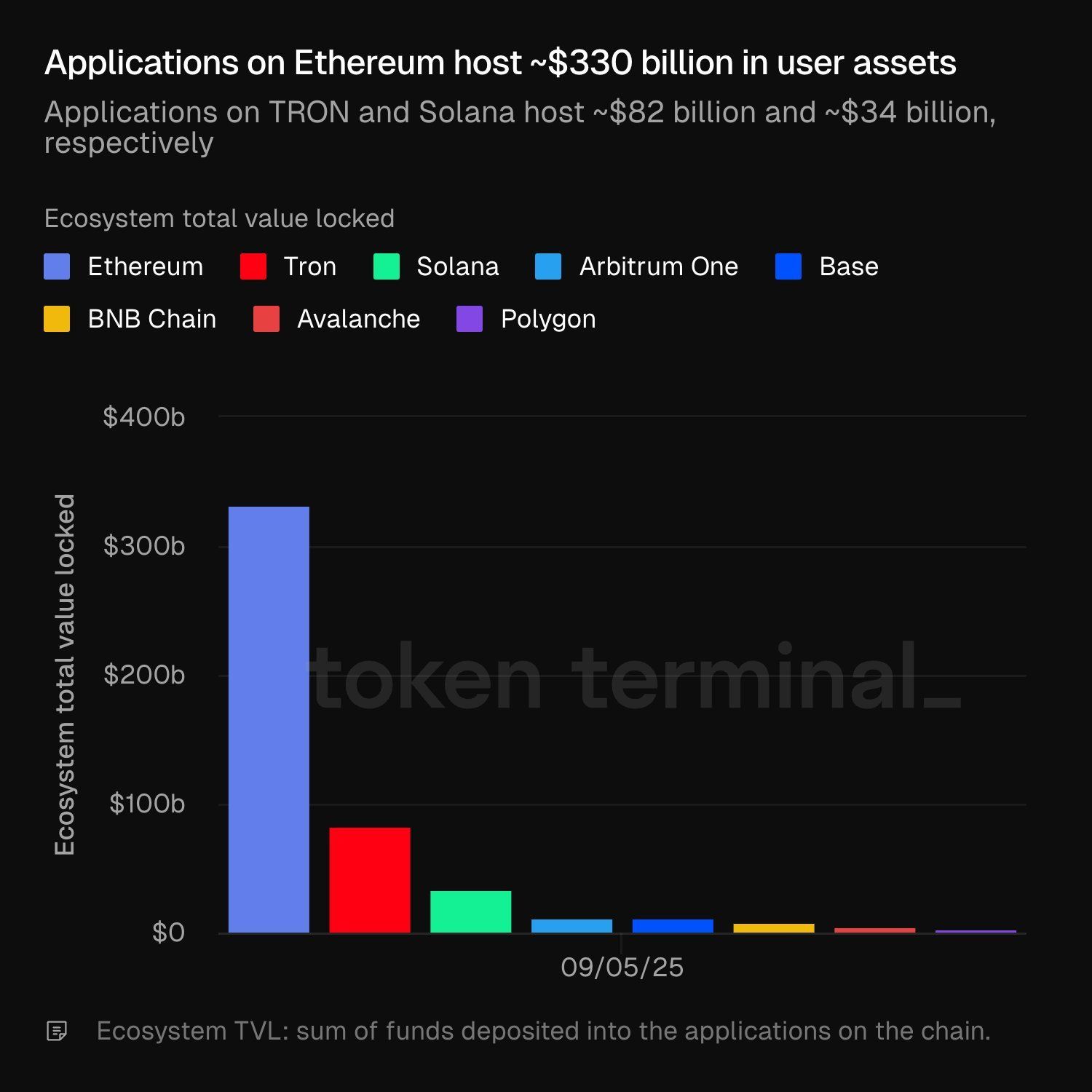
$TRX/USDT : ~$82B |$SOL/USDT : ~$34B
Le TVL des écosystèmes révèle où le vrai capital circule. Suivez les flux et soyez prêts pour la prochaine opportunité. 👀
#Ethereum #CryptoInsights #cryptocurrency #blockchain


Carmelita
2025-09-06 16:53
🔥 Ethereum domine le game !
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
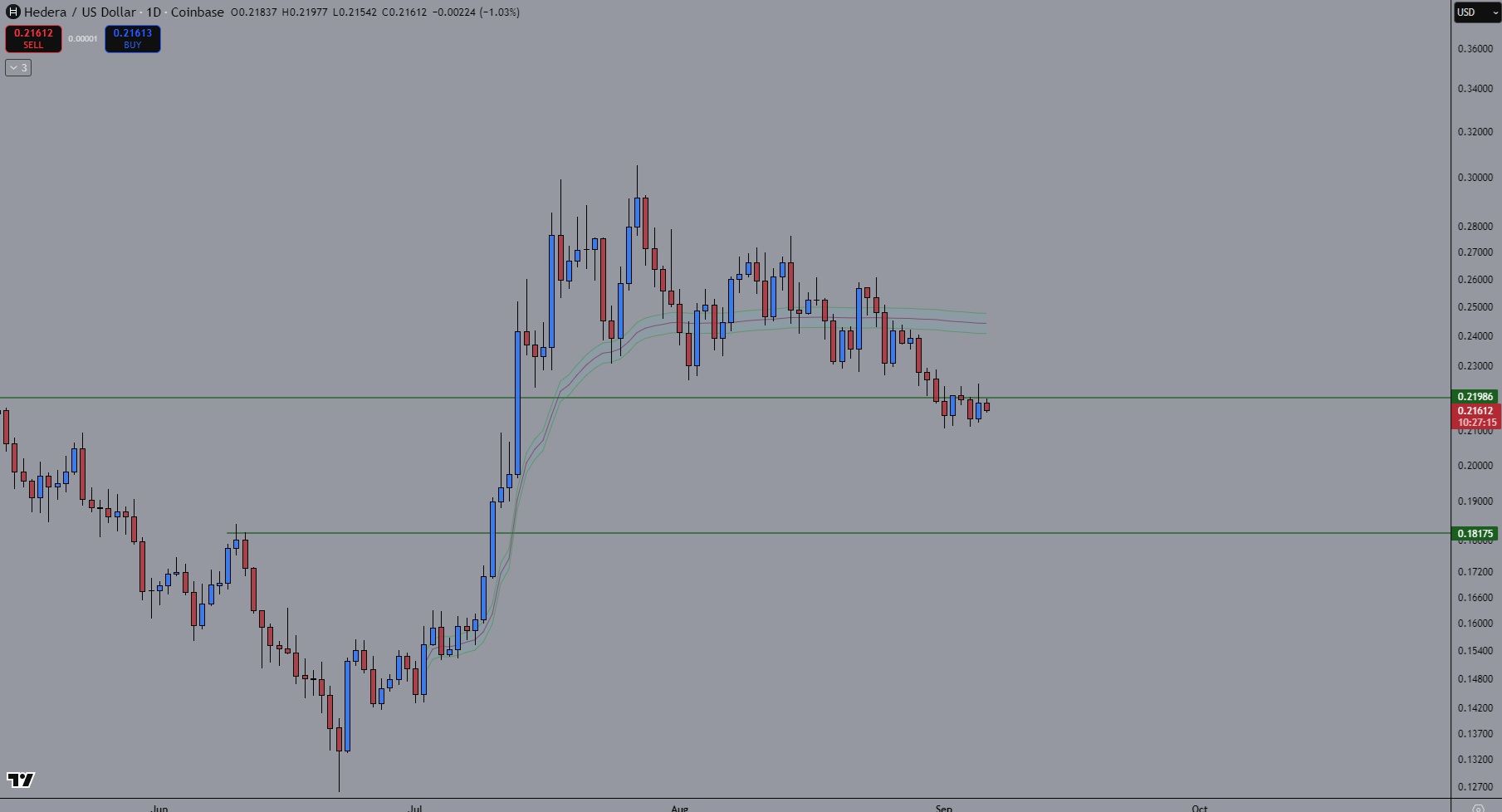
🔥 HBAR prêt à bondir ! $HBAR/USDT Le prix touche un support clé tout en étant largement sous sa moyenne de volume → accumulation en cours. Quand la dynamique reviendra, le prochain mouvement pourrait être explosif. 👀
#HBAR #CryptoInsights #cryptocurrency #blockchain #JuCoin


Carmelita
2025-09-06 17:00
🔥 HBAR prêt à bondir !
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
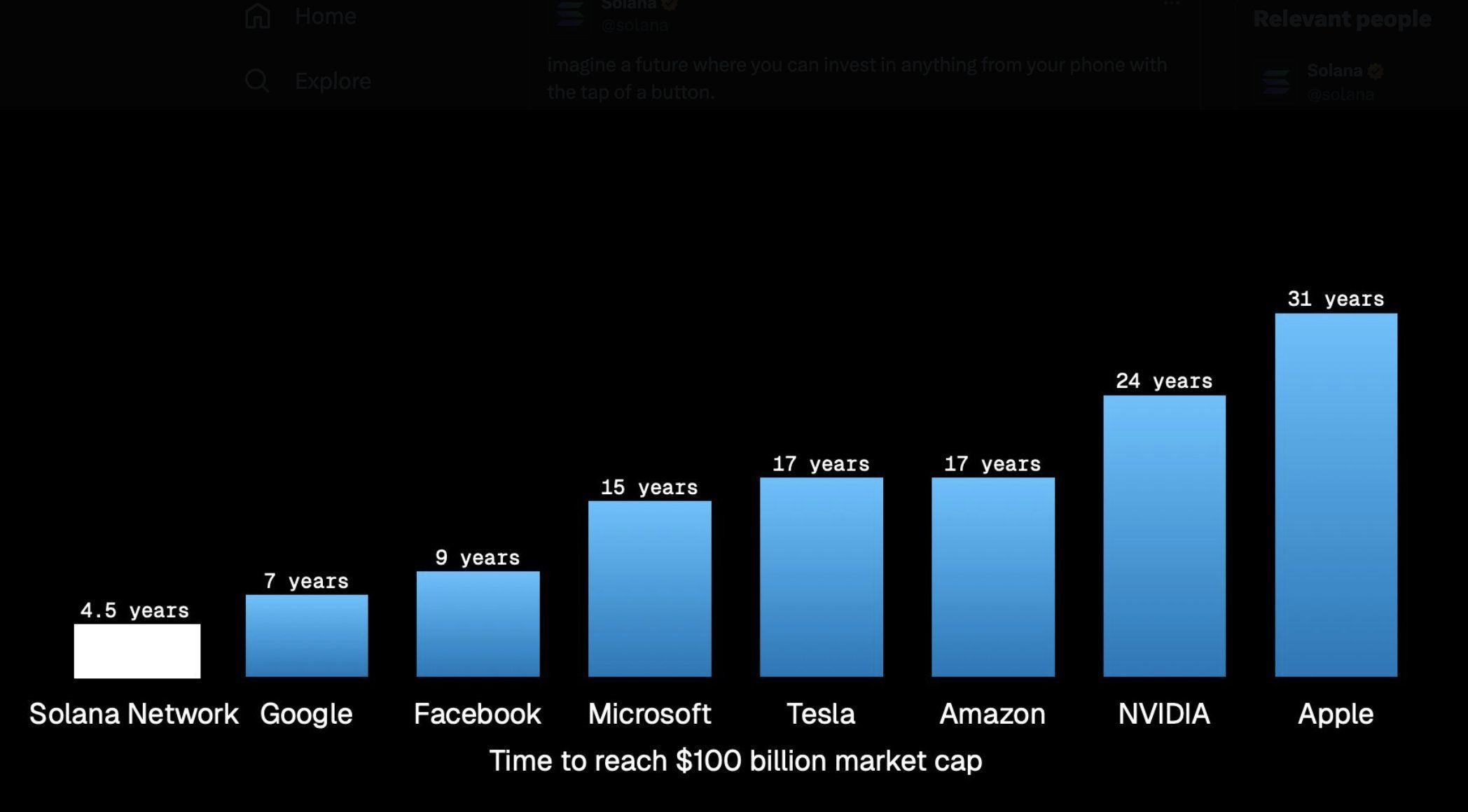
De 0 à +100 milliards $ en valeur d’écosystème en moins de 5 ans — l’une des plus fulgurantes histoires de croissance de la crypto. 👀
$SOL/USDT peut-il encore aller ?
#Solana #crypto #cryptocurrency #blockchain


Carmelita
2025-09-06 16:47
⚡ Solana en mode fusée 🚀
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
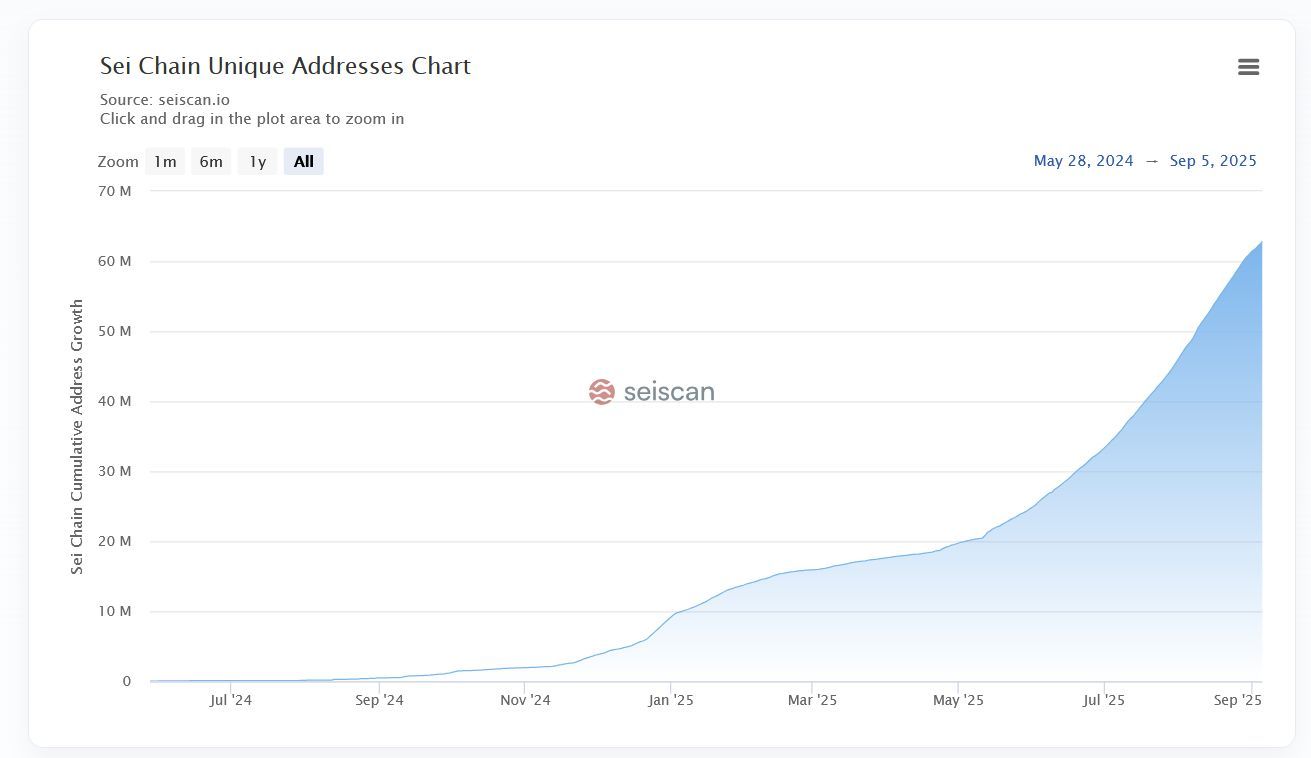
+14M nouvelles adresses en 1 mois Avec un record absolu de 715,814 wallets créés en une seule journée (9 août 2025).
$SEI/USDT ? 👀
#SEI #crypto #cryptocurrency #blockchain


Carmelita
2025-09-06 16:37
📈 SEI explose son adoption !
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
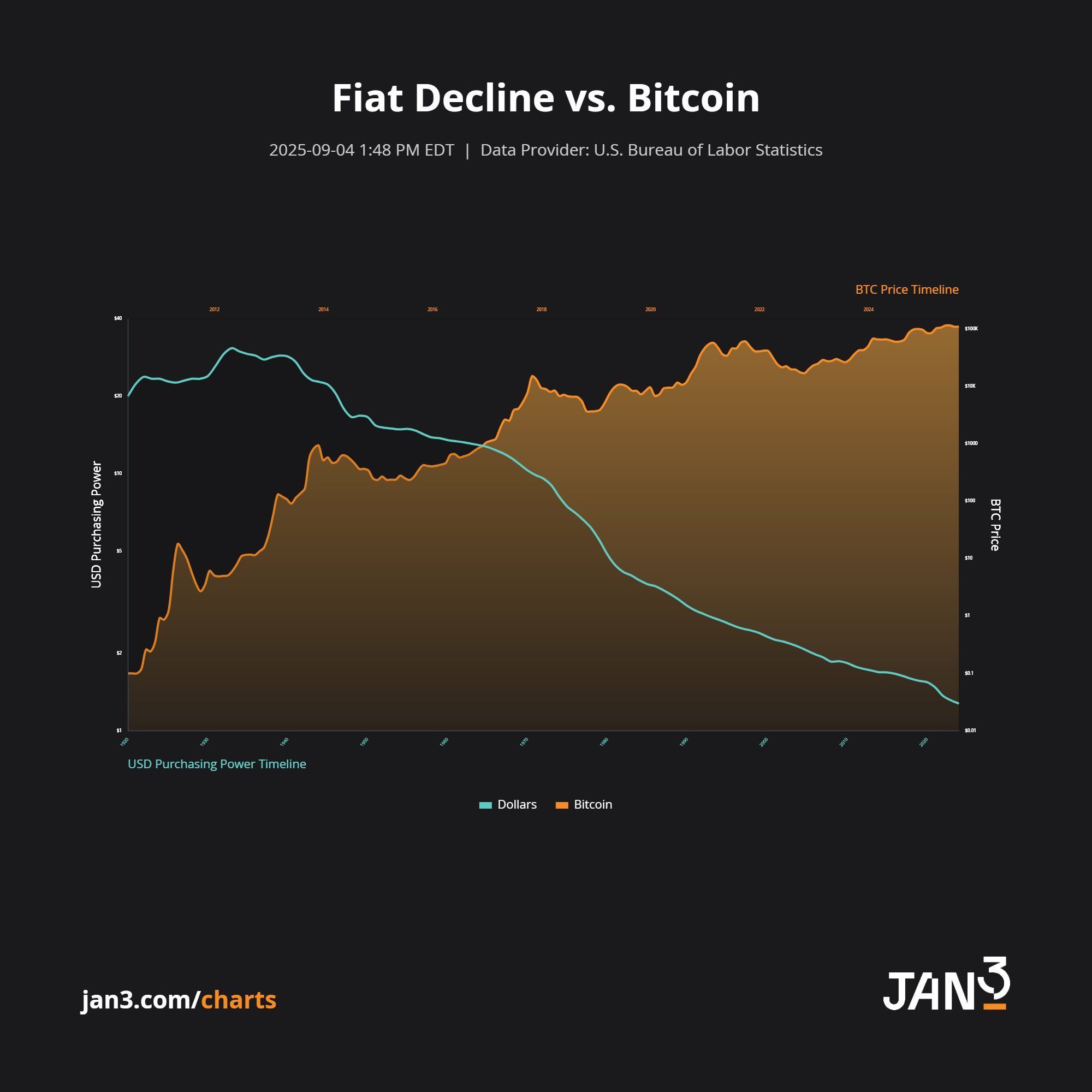
FACT: Les monnaies fiat perdent sans cesse de leur pouvoir d’achat… tandis que #Bitcoin ne cesse de grimper. 💪
📊 La tendance est limpide : ❌ Déclin du fiat ✅ Puissance du $BTC
La vraie question : combien de temps avant que Bitcoin devienne la référence monétaire mondiale ? 👀
#crypto #Bitcoin #cryptocurrency #blockchain


Carmelita
2025-09-06 16:40
🚨 FACT: Les monnaies fiat perdent sans cesse de leur pouvoir d’achat… tandis que #Bitcoin ne cesse
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
What Is the Total Number of Transactions on the Bitcoin Network?
Understanding the total number of transactions on the Bitcoin network is essential for grasping how active and widely used this pioneering cryptocurrency truly is. This metric offers insights into user engagement, network health, and overall adoption trends. In this article, we will explore what influences transaction volume, recent developments in 2023, and what these figures mean for investors and users alike.
How Does Transaction Volume Reflect Network Activity?
The total number of Bitcoin transactions indicates how frequently users are transferring funds or engaging with blockchain-based applications. On average, as of 2023, around 250,000 to 300,000 transactions occur daily. These fluctuations are driven by various factors such as market sentiment—bullish periods tend to see increased activity—as well as regulatory environments that can either encourage or restrict usage.
High transaction volumes suggest a vibrant ecosystem where users actively buy, sell, or transfer Bitcoin. Conversely, dips may signal reduced interest or external pressures like stricter regulations. Monitoring these numbers helps stakeholders gauge whether Bitcoin remains a popular medium for peer-to-peer payments or speculative trading.
Factors Influencing Transaction Counts
Several key elements impact how many transactions are recorded on the blockchain:
- Market Conditions: Bull markets often lead to increased trading activity as investors seek opportunities.
- Regulatory Changes: Stricter laws can temporarily suppress transaction volumes; conversely, favorable policies may boost activity.
- Network Congestion: When many users transact simultaneously—such as during major price swings—transaction fees rise due to limited block space.
- Technological Developments: Improvements like SegWit (Segregated Witness) have optimized transaction processing times and costs over time.
These factors collectively shape daily transaction counts and influence user behavior across different periods.
Recent Trends in 2023: Fluctuations in Transaction Numbers
In April 2023, the Bitcoin network experienced a notable surge in transaction volume driven by heightened market speculation amid potential regulatory shifts in major economies. This increase was partly fueled by traders reacting to news about possible government interventions that could impact cryptocurrency markets globally.
However, May saw an uptick in average transaction fees—about a 20% rise compared to previous months—which reflects higher network congestion. Elevated fees can discourage smaller transactions from occurring frequently because they become less cost-effective for everyday use cases like micro-payments or casual transfers.
These recent trends highlight how external events directly influence not only how much activity occurs but also its economic viability for typical users.
Blockchain Size and Its Impact on Transactions
The size of the Bitcoin blockchain itself provides context about overall network activity; it stood at approximately 400 GB in early 2023—a significant increase from previous years due to continuous addition of new blocks containing transactional data.
A larger blockchain signifies more historical data stored across nodes worldwide but also raises concerns regarding scalability:
- Larger blockchains require more storage capacity.
- Synchronization times increase for new nodes joining the network.
- Higher data loads can contribute to slower confirmation times during peak periods unless scaling solutions are implemented effectively.
Efforts such as Lightning Network aim to address these scalability challenges by enabling faster off-chain transactions while maintaining security through underlying blockchain settlement layers.
The Role of Miners and Validation Processes
Miners play a crucial role in maintaining accurate records by validating transactions through complex computational puzzles—a process known as proof-of-work (PoW). They compete within seconds to add new blocks containing pending transactions onto the chain; successful miners receive rewards plus associated fees paid by transacting parties.
This validation process ensures integrity but is energy-intensive: estimates suggest that mining consumes substantial electricity globally. As demand increases with higher transaction volumes during active periods like April-May 2023’s surge,
the environmental footprint becomes more prominent concern among regulators and advocates alike.
Key Points About Mining:
- Miners validate hundreds of thousands of daily transactions
- Validation ensures decentralization & security
- Rising demand impacts energy consumption
Regulatory Environment's Effect on Transaction Volumes
Government policies significantly influence user participation levels on the Bitcoin network. In early 2023,
several countries introduced stricter regulations targeting crypto exchanges,which temporarily dampened trading activities reflected through decreased transaction counts initially observed after policy announcements.
However,
some jurisdictions adopted clearer frameworks encouraging institutional involvement,potentially stabilizing or increasing future transactional activity once compliance mechanisms were established.
Summary:
Regulatory uncertainty remains one of the most unpredictable factors affecting total bitcoin transactions; ongoing legislative developments will continue shaping usage patterns moving forward.
Future Outlook: Scalability Solutions & Adoption Trends
As interest grows among retail investors and institutions alike,
scalability solutions such as Taproot upgrades,Lightning Network implementations,and sidechains aim to facilitate faster processing at lower costs.
These technological advancements could help sustain higher throughput levels necessary for mainstream adoption while reducing congestion-related fee hikes seen earlier this year.
Moreover,
wider acceptance from merchants accepting bitcoin payments directly enhances real-world utility beyond speculative trading,
potentially leading toward sustained growth in total number of daily transactions over coming years.
By continuously monitoring metrics like total bitcoin transaction count alongside technological improvements and regulatory changes,
stakeholders—from individual users to large-scale investors—can better understand market dynamics
and make informed decisions aligned with evolving industry conditions.
References
- CoinDesk — General information on Bitcoin networks
- Blockchain.com Charts — Historical data analysis
- Blockchain Size Data — Blockchain growth insights
- Transaction Fees & Congestion — Impact analysis
- Bitcoin Mining Process — Technical validation overview
- Regulatory Impact Reports — Policy effects assessment
Understanding how many people transact using Bitcoin provides valuable insight into its current state—and future potential—as both an investment asset and a decentralized payment system amidst an ever-changing global landscape


Lo
2025-05-06 07:37
What is the total number of transactions on the Bitcoin network?
What Is the Total Number of Transactions on the Bitcoin Network?
Understanding the total number of transactions on the Bitcoin network is essential for grasping how active and widely used this pioneering cryptocurrency truly is. This metric offers insights into user engagement, network health, and overall adoption trends. In this article, we will explore what influences transaction volume, recent developments in 2023, and what these figures mean for investors and users alike.
How Does Transaction Volume Reflect Network Activity?
The total number of Bitcoin transactions indicates how frequently users are transferring funds or engaging with blockchain-based applications. On average, as of 2023, around 250,000 to 300,000 transactions occur daily. These fluctuations are driven by various factors such as market sentiment—bullish periods tend to see increased activity—as well as regulatory environments that can either encourage or restrict usage.
High transaction volumes suggest a vibrant ecosystem where users actively buy, sell, or transfer Bitcoin. Conversely, dips may signal reduced interest or external pressures like stricter regulations. Monitoring these numbers helps stakeholders gauge whether Bitcoin remains a popular medium for peer-to-peer payments or speculative trading.
Factors Influencing Transaction Counts
Several key elements impact how many transactions are recorded on the blockchain:
- Market Conditions: Bull markets often lead to increased trading activity as investors seek opportunities.
- Regulatory Changes: Stricter laws can temporarily suppress transaction volumes; conversely, favorable policies may boost activity.
- Network Congestion: When many users transact simultaneously—such as during major price swings—transaction fees rise due to limited block space.
- Technological Developments: Improvements like SegWit (Segregated Witness) have optimized transaction processing times and costs over time.
These factors collectively shape daily transaction counts and influence user behavior across different periods.
Recent Trends in 2023: Fluctuations in Transaction Numbers
In April 2023, the Bitcoin network experienced a notable surge in transaction volume driven by heightened market speculation amid potential regulatory shifts in major economies. This increase was partly fueled by traders reacting to news about possible government interventions that could impact cryptocurrency markets globally.
However, May saw an uptick in average transaction fees—about a 20% rise compared to previous months—which reflects higher network congestion. Elevated fees can discourage smaller transactions from occurring frequently because they become less cost-effective for everyday use cases like micro-payments or casual transfers.
These recent trends highlight how external events directly influence not only how much activity occurs but also its economic viability for typical users.
Blockchain Size and Its Impact on Transactions
The size of the Bitcoin blockchain itself provides context about overall network activity; it stood at approximately 400 GB in early 2023—a significant increase from previous years due to continuous addition of new blocks containing transactional data.
A larger blockchain signifies more historical data stored across nodes worldwide but also raises concerns regarding scalability:
- Larger blockchains require more storage capacity.
- Synchronization times increase for new nodes joining the network.
- Higher data loads can contribute to slower confirmation times during peak periods unless scaling solutions are implemented effectively.
Efforts such as Lightning Network aim to address these scalability challenges by enabling faster off-chain transactions while maintaining security through underlying blockchain settlement layers.
The Role of Miners and Validation Processes
Miners play a crucial role in maintaining accurate records by validating transactions through complex computational puzzles—a process known as proof-of-work (PoW). They compete within seconds to add new blocks containing pending transactions onto the chain; successful miners receive rewards plus associated fees paid by transacting parties.
This validation process ensures integrity but is energy-intensive: estimates suggest that mining consumes substantial electricity globally. As demand increases with higher transaction volumes during active periods like April-May 2023’s surge,
the environmental footprint becomes more prominent concern among regulators and advocates alike.
Key Points About Mining:
- Miners validate hundreds of thousands of daily transactions
- Validation ensures decentralization & security
- Rising demand impacts energy consumption
Regulatory Environment's Effect on Transaction Volumes
Government policies significantly influence user participation levels on the Bitcoin network. In early 2023,
several countries introduced stricter regulations targeting crypto exchanges,which temporarily dampened trading activities reflected through decreased transaction counts initially observed after policy announcements.
However,
some jurisdictions adopted clearer frameworks encouraging institutional involvement,potentially stabilizing or increasing future transactional activity once compliance mechanisms were established.
Summary:
Regulatory uncertainty remains one of the most unpredictable factors affecting total bitcoin transactions; ongoing legislative developments will continue shaping usage patterns moving forward.
Future Outlook: Scalability Solutions & Adoption Trends
As interest grows among retail investors and institutions alike,
scalability solutions such as Taproot upgrades,Lightning Network implementations,and sidechains aim to facilitate faster processing at lower costs.
These technological advancements could help sustain higher throughput levels necessary for mainstream adoption while reducing congestion-related fee hikes seen earlier this year.
Moreover,
wider acceptance from merchants accepting bitcoin payments directly enhances real-world utility beyond speculative trading,
potentially leading toward sustained growth in total number of daily transactions over coming years.
By continuously monitoring metrics like total bitcoin transaction count alongside technological improvements and regulatory changes,
stakeholders—from individual users to large-scale investors—can better understand market dynamics
and make informed decisions aligned with evolving industry conditions.
References
- CoinDesk — General information on Bitcoin networks
- Blockchain.com Charts — Historical data analysis
- Blockchain Size Data — Blockchain growth insights
- Transaction Fees & Congestion — Impact analysis
- Bitcoin Mining Process — Technical validation overview
- Regulatory Impact Reports — Policy effects assessment
Understanding how many people transact using Bitcoin provides valuable insight into its current state—and future potential—as both an investment asset and a decentralized payment system amidst an ever-changing global landscape
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
What is Wallet Address Clustering?
Wallet address clustering is a crucial technique in the blockchain and cryptocurrency ecosystem that involves grouping multiple wallet addresses based on shared transaction behaviors or characteristics. This process helps analysts, security professionals, and regulators better understand how digital assets move across the network, identify potential illicit activities, and improve privacy measures for users.
Understanding Wallet Addresses in Cryptocurrency
In the world of cryptocurrencies like Bitcoin and Ethereum, each user interacts with the blockchain through wallet addresses—unique alphanumeric strings that serve as digital bank accounts. These addresses are generated cryptographically to ensure pseudonymity; they do not directly reveal personal identities. However, despite this pseudonymity, all transactions linked to these addresses are publicly recorded on the blockchain ledger.
As transaction volumes grow exponentially over time, it becomes increasingly difficult to maintain complete anonymity for individual users. Every transaction leaves a trail that can potentially be traced back to specific entities or behaviors if analyzed correctly. This is where wallet address clustering comes into play—it aims to analyze patterns across multiple addresses to infer relationships or groupings.
How Does Wallet Address Clustering Work?
Wallet address clustering employs various algorithms and analytical techniques designed to detect similarities among different addresses based on their activity patterns. These methods include:
- Transaction Pattern Analysis: Examining transfer amounts, timing between transactions, and frequency.
- Behavioral Signatures: Identifying common usage habits such as recurring transfers or specific asset types.
- Graph-Based Clustering: Creating visual maps of interconnected addresses based on shared inputs or outputs within transactions.
Popular algorithms used in this context include k-means clustering (which partitions data into predefined groups), hierarchical clustering (which builds nested clusters), and density-based methods like DBSCAN (which identifies clusters of varying shapes). Each has its strengths depending on dataset complexity and analysis goals.
Why Is Wallet Address Clustering Important?
The significance of wallet address clustering extends across several key areas:
Enhancing Privacy
While cryptocurrencies are often touted for their privacy features, true anonymity remains elusive due to transparent transaction records. By grouping related addresses together through clustering techniques, third parties find it more challenging to link individual transactions back to specific users—especially when combined with other privacy-preserving tools like mixers or privacy coins.
Security Monitoring
Clustering enables security teams and law enforcement agencies to detect suspicious activities such as money laundering schemes or fraud rings by spotting unusual patterns—like rapid transfers between clustered groups or large volume spikes—that deviate from typical user behavior.
Regulatory Compliance
Financial institutions operating within regulatory frameworks use wallet address analysis for anti-money laundering (AML) efforts and know-your-customer (KYC) procedures. While full anonymization isn't always possible with effective clustering tools, these techniques help create a more compliant environment by providing insights into transactional relationships without exposing sensitive details unnecessarily.
Recent Advances in Wallet Address Clustering
Over recent years, significant progress has been made in refining clustering methodologies:
- Improved Algorithms: Researchers have developed sophisticated models capable of handling vast datasets efficiently while uncovering complex behavioral patterns.
- Integration Into Blockchain Analytics Platforms: Major analytics providers now incorporate advanced clustering features into their tools—enabling users ranging from law enforcement agencies to financial firms—to gain deeper insights.
- Privacy-Centric Cryptocurrencies: Some projects have integrated cluster-aware features directly into their protocols—for example, enhancing user privacy while still allowing legitimate analysis under certain conditions—which reflects ongoing innovation balancing transparency with confidentiality.
Challenges & Ethical Considerations
Despite its benefits, wallet address clustering raises important concerns:
Regulatory Dilemmas: As authorities seek greater oversight over illicit activities like money laundering or terrorist financing via blockchain analysis tools—including those employing clustering—they face challenges balancing user privacy rights against compliance needs.
Potential for Misuse: If improperly implemented—or used without proper safeguards—clustering could inadvertently obscure legitimate transactions involving businesses or individuals who rely on enhanced privacy measures.
Ethical Debates: The debate continues around whether such analytical techniques should be solely used for security purposes—or if they risk infringing upon personal freedoms by enabling pervasive surveillance without adequate oversight.
Timeline of Key Developments
Understanding how wallet address clustering has evolved provides context about its current state:
- 2020: Academic research focused on evaluating different algorithms' effectiveness at preserving user privacy while enabling meaningful analysis.
- 2021: Major blockchain analytics platforms began integrating advanced cluster detection features amid rising demand from compliance-focused clients.
- 2022: The rise of privacy-centric cryptocurrencies prompted developers to embed cluster-aware mechanisms directly within protocols themselves.
- 2023: Regulatory discussions intensified regarding how best practices can balance effective AML/KYC processes with respecting individual rights—a debate ongoing today.
By grasping what wallet address clustering entails—and recognizing both its capabilities and limitations—you can better appreciate its role within broader efforts toward secure yet private cryptocurrency usage. Whether you're an investor seeking insight into transaction behaviors—or a regulator aiming at compliance—the evolving landscape underscores the importance of understanding this powerful analytical tool in today's digital economy.
Keywords: cryptocurrency wallets | blockchain analysis | transaction pattern recognition | crypto privacy | AML compliance | crypto security | decentralized finance


Lo
2025-05-15 03:19
What is wallet address clustering?
What is Wallet Address Clustering?
Wallet address clustering is a crucial technique in the blockchain and cryptocurrency ecosystem that involves grouping multiple wallet addresses based on shared transaction behaviors or characteristics. This process helps analysts, security professionals, and regulators better understand how digital assets move across the network, identify potential illicit activities, and improve privacy measures for users.
Understanding Wallet Addresses in Cryptocurrency
In the world of cryptocurrencies like Bitcoin and Ethereum, each user interacts with the blockchain through wallet addresses—unique alphanumeric strings that serve as digital bank accounts. These addresses are generated cryptographically to ensure pseudonymity; they do not directly reveal personal identities. However, despite this pseudonymity, all transactions linked to these addresses are publicly recorded on the blockchain ledger.
As transaction volumes grow exponentially over time, it becomes increasingly difficult to maintain complete anonymity for individual users. Every transaction leaves a trail that can potentially be traced back to specific entities or behaviors if analyzed correctly. This is where wallet address clustering comes into play—it aims to analyze patterns across multiple addresses to infer relationships or groupings.
How Does Wallet Address Clustering Work?
Wallet address clustering employs various algorithms and analytical techniques designed to detect similarities among different addresses based on their activity patterns. These methods include:
- Transaction Pattern Analysis: Examining transfer amounts, timing between transactions, and frequency.
- Behavioral Signatures: Identifying common usage habits such as recurring transfers or specific asset types.
- Graph-Based Clustering: Creating visual maps of interconnected addresses based on shared inputs or outputs within transactions.
Popular algorithms used in this context include k-means clustering (which partitions data into predefined groups), hierarchical clustering (which builds nested clusters), and density-based methods like DBSCAN (which identifies clusters of varying shapes). Each has its strengths depending on dataset complexity and analysis goals.
Why Is Wallet Address Clustering Important?
The significance of wallet address clustering extends across several key areas:
Enhancing Privacy
While cryptocurrencies are often touted for their privacy features, true anonymity remains elusive due to transparent transaction records. By grouping related addresses together through clustering techniques, third parties find it more challenging to link individual transactions back to specific users—especially when combined with other privacy-preserving tools like mixers or privacy coins.
Security Monitoring
Clustering enables security teams and law enforcement agencies to detect suspicious activities such as money laundering schemes or fraud rings by spotting unusual patterns—like rapid transfers between clustered groups or large volume spikes—that deviate from typical user behavior.
Regulatory Compliance
Financial institutions operating within regulatory frameworks use wallet address analysis for anti-money laundering (AML) efforts and know-your-customer (KYC) procedures. While full anonymization isn't always possible with effective clustering tools, these techniques help create a more compliant environment by providing insights into transactional relationships without exposing sensitive details unnecessarily.
Recent Advances in Wallet Address Clustering
Over recent years, significant progress has been made in refining clustering methodologies:
- Improved Algorithms: Researchers have developed sophisticated models capable of handling vast datasets efficiently while uncovering complex behavioral patterns.
- Integration Into Blockchain Analytics Platforms: Major analytics providers now incorporate advanced clustering features into their tools—enabling users ranging from law enforcement agencies to financial firms—to gain deeper insights.
- Privacy-Centric Cryptocurrencies: Some projects have integrated cluster-aware features directly into their protocols—for example, enhancing user privacy while still allowing legitimate analysis under certain conditions—which reflects ongoing innovation balancing transparency with confidentiality.
Challenges & Ethical Considerations
Despite its benefits, wallet address clustering raises important concerns:
Regulatory Dilemmas: As authorities seek greater oversight over illicit activities like money laundering or terrorist financing via blockchain analysis tools—including those employing clustering—they face challenges balancing user privacy rights against compliance needs.
Potential for Misuse: If improperly implemented—or used without proper safeguards—clustering could inadvertently obscure legitimate transactions involving businesses or individuals who rely on enhanced privacy measures.
Ethical Debates: The debate continues around whether such analytical techniques should be solely used for security purposes—or if they risk infringing upon personal freedoms by enabling pervasive surveillance without adequate oversight.
Timeline of Key Developments
Understanding how wallet address clustering has evolved provides context about its current state:
- 2020: Academic research focused on evaluating different algorithms' effectiveness at preserving user privacy while enabling meaningful analysis.
- 2021: Major blockchain analytics platforms began integrating advanced cluster detection features amid rising demand from compliance-focused clients.
- 2022: The rise of privacy-centric cryptocurrencies prompted developers to embed cluster-aware mechanisms directly within protocols themselves.
- 2023: Regulatory discussions intensified regarding how best practices can balance effective AML/KYC processes with respecting individual rights—a debate ongoing today.
By grasping what wallet address clustering entails—and recognizing both its capabilities and limitations—you can better appreciate its role within broader efforts toward secure yet private cryptocurrency usage. Whether you're an investor seeking insight into transaction behaviors—or a regulator aiming at compliance—the evolving landscape underscores the importance of understanding this powerful analytical tool in today's digital economy.
Keywords: cryptocurrency wallets | blockchain analysis | transaction pattern recognition | crypto privacy | AML compliance | crypto security | decentralized finance
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
What Is Blockchain Interoperability? A Complete Overview
Understanding Blockchain Interoperability
Blockchain interoperability refers to the ability of different blockchain networks to communicate, share data, and transfer assets seamlessly. Unlike traditional financial systems where institutions can easily exchange information through standardized protocols, blockchain ecosystems are often isolated due to differing architectures and protocols. Interoperability aims to bridge these gaps, creating a more interconnected decentralized environment. This capability is essential for enabling cross-chain transactions, expanding the utility of digital assets, and fostering innovation across various blockchain platforms.
Why Is Interoperability Important in Blockchain Technology?
As blockchain technology matures, its applications have diversified into areas like decentralized finance (DeFi), non-fungible tokens (NFTs), supply chain management, and more. These use cases often require interaction between multiple blockchains—for example, transferring an NFT from one platform to another or executing a DeFi trade across different networks. Without interoperability, users face fragmentation; they must navigate multiple interfaces or convert assets manually through exchanges.
Interoperability enhances user experience by allowing smooth asset transfers and data sharing without intermediaries or complex procedures. It also promotes scalability by enabling specialized blockchains optimized for specific tasks while still maintaining connectivity with broader ecosystems.
Types of Blockchain Interoperability
There are primarily two types of interoperability based on how blockchains connect:
Homogeneous Interoperability: This involves different chains that share similar consensus mechanisms and protocols—think of it as connecting similar "languages." For example, two Ethereum-compatible chains can communicate more straightforwardly because they follow compatible standards.
Heterogeneous Interoperability: This connects fundamentally different blockchains with distinct architectures—such as Bitcoin and Ethereum—requiring more complex solutions like cross-chain bridges or protocol adapters.
Technologies Enabling Cross-Chain Communication
Several innovative technologies facilitate interoperability:
Cross-Chain Atomic Swaps: These enable the direct exchange of assets between two separate blockchains without intermediaries. They rely on smart contracts that ensure both parties fulfill their obligations simultaneously.
Sidechains: Smaller chains linked to a main chain via pegging mechanisms allow assets to move back and forth securely while leveraging the main chain’s security features.
Layer 2 Solutions: Technologies like Lightning Network (Bitcoin) or Optimism (Ethereum) improve scalability and enable faster cross-chain interactions by processing transactions off the main chain before settling them on-chain.
Interoperability Protocols:
- Cosmos IBC: The Inter-Blockchain Communication protocol allows independent zones within Cosmos’ ecosystem—and beyond—to transfer data securely.
- Polkadot Relay Chain: Acts as a central hub connecting various parachains (independent but connected chains), facilitating asset transfers across diverse networks.
Challenges Facing Blockchain Interoperability
Despite promising advancements, several hurdles remain:
Scalability Concerns: Ensuring rapid transaction speeds without compromising security is challenging when connecting multiple networks with varying capacities.
Security Risks: Cross-chain bridges are vulnerable points; exploits could lead to significant losses if not properly secured against attacks such as double-spending or 51% attacks.
Regulatory Uncertainty: Different jurisdictions impose varying rules on cryptocurrencies which complicate compliance efforts during cross-border transactions involving multiple legal frameworks.
Recent Developments in Cross-Chain Compatibility
The landscape has seen notable progress recently:
Cosmos launched its IBC protocol in 2020, enabling seamless communication among Cosmos-based chains—a significant step toward an interconnected ecosystem.
Polkadot’s Relay Chain has been operational since 2020; it facilitates asset transfers between parachains within its network while exploring connections outside its ecosystem.
Binance Smart Chain has integrated several interoperability solutions including atomic swaps and sidechain integrations with Ethereum-compatible projects.
Solana is actively exploring partnerships aimed at bridging its high-performance network with Ethereum through technological collaborations designed for cross-platform compatibility.
Potential Risks & Future Outlook
While these developments mark substantial progress toward interconnectedness in blockchain space, potential risks could impact adoption:
Security vulnerabilities remain a concern if bridges aren’t implemented correctly—they could be exploited leading to loss of funds or data breaches.
Regulatory challenges may arise as authorities develop frameworks around cross-border digital asset movements; inconsistent policies might hinder seamless integration globally.
Market sentiment can also be affected by technological failures or delays in deploying robust interoperability solutions—affecting investor confidence and asset prices alike.
Looking ahead,
the push towards universal compatibility continues driven by demand from users seeking streamlined experiences across platforms. As technical standards mature alongside regulatory clarity,
blockchain interoperability promises not only enhanced functionality but also increased mainstream adoption of decentralized technologies.
Understanding how diverse networks connect will be vital for developers aiming at building scalable dApps,
investors seeking diversified portfolios,
and regulators working towards balanced oversight that fosters innovation without compromising security.
By addressing current challenges head-on through collaborative efforts among industry stakeholders,
the vision of an fully interoperable blockchain universe becomes increasingly attainable—one where digital assets flow freely regardless of underlying architecture.
This comprehensive overview underscores why blockchain interoperability is fundamental for advancing decentralized technology's potential—and why ongoing innovations will shape the future landscape significantly


JCUSER-IC8sJL1q
2025-05-15 03:34
What is interoperability between blockchains?
What Is Blockchain Interoperability? A Complete Overview
Understanding Blockchain Interoperability
Blockchain interoperability refers to the ability of different blockchain networks to communicate, share data, and transfer assets seamlessly. Unlike traditional financial systems where institutions can easily exchange information through standardized protocols, blockchain ecosystems are often isolated due to differing architectures and protocols. Interoperability aims to bridge these gaps, creating a more interconnected decentralized environment. This capability is essential for enabling cross-chain transactions, expanding the utility of digital assets, and fostering innovation across various blockchain platforms.
Why Is Interoperability Important in Blockchain Technology?
As blockchain technology matures, its applications have diversified into areas like decentralized finance (DeFi), non-fungible tokens (NFTs), supply chain management, and more. These use cases often require interaction between multiple blockchains—for example, transferring an NFT from one platform to another or executing a DeFi trade across different networks. Without interoperability, users face fragmentation; they must navigate multiple interfaces or convert assets manually through exchanges.
Interoperability enhances user experience by allowing smooth asset transfers and data sharing without intermediaries or complex procedures. It also promotes scalability by enabling specialized blockchains optimized for specific tasks while still maintaining connectivity with broader ecosystems.
Types of Blockchain Interoperability
There are primarily two types of interoperability based on how blockchains connect:
Homogeneous Interoperability: This involves different chains that share similar consensus mechanisms and protocols—think of it as connecting similar "languages." For example, two Ethereum-compatible chains can communicate more straightforwardly because they follow compatible standards.
Heterogeneous Interoperability: This connects fundamentally different blockchains with distinct architectures—such as Bitcoin and Ethereum—requiring more complex solutions like cross-chain bridges or protocol adapters.
Technologies Enabling Cross-Chain Communication
Several innovative technologies facilitate interoperability:
Cross-Chain Atomic Swaps: These enable the direct exchange of assets between two separate blockchains without intermediaries. They rely on smart contracts that ensure both parties fulfill their obligations simultaneously.
Sidechains: Smaller chains linked to a main chain via pegging mechanisms allow assets to move back and forth securely while leveraging the main chain’s security features.
Layer 2 Solutions: Technologies like Lightning Network (Bitcoin) or Optimism (Ethereum) improve scalability and enable faster cross-chain interactions by processing transactions off the main chain before settling them on-chain.
Interoperability Protocols:
- Cosmos IBC: The Inter-Blockchain Communication protocol allows independent zones within Cosmos’ ecosystem—and beyond—to transfer data securely.
- Polkadot Relay Chain: Acts as a central hub connecting various parachains (independent but connected chains), facilitating asset transfers across diverse networks.
Challenges Facing Blockchain Interoperability
Despite promising advancements, several hurdles remain:
Scalability Concerns: Ensuring rapid transaction speeds without compromising security is challenging when connecting multiple networks with varying capacities.
Security Risks: Cross-chain bridges are vulnerable points; exploits could lead to significant losses if not properly secured against attacks such as double-spending or 51% attacks.
Regulatory Uncertainty: Different jurisdictions impose varying rules on cryptocurrencies which complicate compliance efforts during cross-border transactions involving multiple legal frameworks.
Recent Developments in Cross-Chain Compatibility
The landscape has seen notable progress recently:
Cosmos launched its IBC protocol in 2020, enabling seamless communication among Cosmos-based chains—a significant step toward an interconnected ecosystem.
Polkadot’s Relay Chain has been operational since 2020; it facilitates asset transfers between parachains within its network while exploring connections outside its ecosystem.
Binance Smart Chain has integrated several interoperability solutions including atomic swaps and sidechain integrations with Ethereum-compatible projects.
Solana is actively exploring partnerships aimed at bridging its high-performance network with Ethereum through technological collaborations designed for cross-platform compatibility.
Potential Risks & Future Outlook
While these developments mark substantial progress toward interconnectedness in blockchain space, potential risks could impact adoption:
Security vulnerabilities remain a concern if bridges aren’t implemented correctly—they could be exploited leading to loss of funds or data breaches.
Regulatory challenges may arise as authorities develop frameworks around cross-border digital asset movements; inconsistent policies might hinder seamless integration globally.
Market sentiment can also be affected by technological failures or delays in deploying robust interoperability solutions—affecting investor confidence and asset prices alike.
Looking ahead,
the push towards universal compatibility continues driven by demand from users seeking streamlined experiences across platforms. As technical standards mature alongside regulatory clarity,
blockchain interoperability promises not only enhanced functionality but also increased mainstream adoption of decentralized technologies.
Understanding how diverse networks connect will be vital for developers aiming at building scalable dApps,
investors seeking diversified portfolios,
and regulators working towards balanced oversight that fosters innovation without compromising security.
By addressing current challenges head-on through collaborative efforts among industry stakeholders,
the vision of an fully interoperable blockchain universe becomes increasingly attainable—one where digital assets flow freely regardless of underlying architecture.
This comprehensive overview underscores why blockchain interoperability is fundamental for advancing decentralized technology's potential—and why ongoing innovations will shape the future landscape significantly
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
What Is a Private Key in Cryptocurrency?
A private key is a fundamental element in the world of blockchain and digital currencies. Think of it as a secret password or digital signature that grants access to your cryptocurrency holdings. Unlike your public address, which you can share openly to receive funds, your private key must remain confidential because it provides control over your assets. If someone gains access to your private key, they can potentially transfer or spend all associated funds without your permission.
In essence, the private key is what authorizes transactions on blockchain networks like Bitcoin and Ethereum. It’s generated through cryptographic algorithms that ensure its uniqueness and security. The strength of this system relies heavily on keeping this key secret; otherwise, the security of your digital assets could be compromised.
How Does a Private Key Work in Blockchain Transactions?
Understanding how private keys function within blockchain transactions involves several steps:
1. Generating a Key Pair
When you create a cryptocurrency wallet, it automatically generates two cryptographic keys: a public key and a private key. The public key acts as an address where others can send you funds—think of it as an email address for receiving money—while the private key remains secret with you.
2. Signing Transactions
To send cryptocurrencies from your wallet, you need to sign the transaction using your private key. This process creates a unique digital signature that proves ownership without revealing the actual private key itself.
3. Verification by Network Nodes
Once signed, the transaction is broadcasted across the network (like Bitcoin or Ethereum). Network nodes verify that the signature matches with the sender’s public key—confirming authenticity—and then add it to the blockchain ledger if valid.
This cryptographic process ensures both security and integrity: only someone with access to the correct private key can authorize spending from an account, preventing unauthorized transactions.
Why Are Private Keys Critical for Digital Asset Security?
Private keys are at the core of securing digital assets because they provide proof of ownership and authorization rights within decentralized systems:
- Confidentiality: Since anyone with access to this secret code can control associated funds, safeguarding it is paramount.
- Irreversibility: Unlike traditional banking systems where errors might be rectified easily, losing access to your private keys typically means losing all control over those assets permanently.
- Security Risks: If exposed through hacking attempts like phishing or malware attacks, malicious actors could drain accounts instantly.
Because these risks are so significant, users often employ various methods such as hardware wallets or encrypted backups to protect their keys effectively.
Types of Private Keys Used in Cryptocurrency Wallets
There are different formats for storing and managing private keys depending on user needs:
- Hexadecimal Strings: Long strings composed solely of numbers 0–9 and letters A–F.
- Wallet Files (e.g., .json files): Encrypted files containing encrypted versions of keys used by software wallets.
- Hardware Wallets: Physical devices like Ledger Nano S/X or Trezor store private keys offline for enhanced security.
Each method offers varying levels of convenience versus security; hardware wallets are generally considered most secure against online threats because they keep keys isolated from internet-connected devices.
Recent Developments in Private Key Management
The landscape around managing crypto-private keys continues evolving rapidly due to technological advancements:
Hardware Wallets Advancements
Devices such as Ledger Nano X have improved user experience while maintaining high-security standards by storing sensitive data offline—a practice known as cold storage—which significantly reduces hacking risks.
Multi-Signature Wallets
Multi-signature (multi-sig) setups require multiple independent signatures before executing transactions—adding layers of approval that prevent single points-of-failure or theft if one device gets compromised.
Quantum Computing Concerns
Emerging quantum computing technology poses potential threats since current cryptography may become vulnerable under powerful quantum algorithms. Researchers are actively developing post-quantum cryptography solutions designed specifically for resisting such attacks without compromising performance today’s systems rely upon.
Regulatory Focus & Industry Standards
As governments worldwide implement regulations around cryptocurrencies’ custody practices—including how users should securely manage their private keys—the industry sees increased adoption of standardized protocols emphasizing secure storage solutions like hardware wallets combined with best practices for backup procedures.
Risks Associated With Private Keys
Despite their importance in securing digital assets, mishandling or exposure poses serious dangers:
Loss Due To Forgetfulness or Damage: Losing physical copies (like paper backups) means permanent loss unless properly stored elsewhere.
Theft Through Phishing & Malware Attacks: Attackers often trick users into revealing their secrets via fake websites (“phishing”) or infecting devices with malware designed specifically for stealing keystrokes or clipboard data containing sensitive information.
Regulatory Non-compliance Risks: Failing to follow proper management procedures may lead not only to financial loss but also legal consequences depending on jurisdictional requirements.
Best Practices For Managing Your Private Keys Safely
To minimize risks associated with handling crypto-private keys:
- Use hardware wallets whenever possible—they store secrets offline away from internet vulnerabilities.
- Create multiple encrypted backups stored securely in geographically separated locations.
- Never share/private reveal your seed phrases — avoid storing them digitally unless encrypted properly.
- Be cautious about phishing attempts; always verify URLs before entering sensitive information online.
- Keep software wallets updated regularly along with device firmware patches.
Staying informed about developments related to privacy-enhancing tools like multi-sig arrangements and advances against emerging threats such as quantum computing will help safeguard investments long-term while complying with evolving regulatory landscapes.
By understanding what exactly constitutes a private key—and adopting robust management strategies—you ensure better protection against thefts while maintaining full control over digital assets within decentralized ecosystems.
Keywords: cryptocurrency privacy tips | secure crypto storage | blockchain security best practices | managing crypto-privatekeys | multi-signature wallets | hardware wallet advantages


Lo
2025-05-06 08:02
What is a private key and how does it work?
What Is a Private Key in Cryptocurrency?
A private key is a fundamental element in the world of blockchain and digital currencies. Think of it as a secret password or digital signature that grants access to your cryptocurrency holdings. Unlike your public address, which you can share openly to receive funds, your private key must remain confidential because it provides control over your assets. If someone gains access to your private key, they can potentially transfer or spend all associated funds without your permission.
In essence, the private key is what authorizes transactions on blockchain networks like Bitcoin and Ethereum. It’s generated through cryptographic algorithms that ensure its uniqueness and security. The strength of this system relies heavily on keeping this key secret; otherwise, the security of your digital assets could be compromised.
How Does a Private Key Work in Blockchain Transactions?
Understanding how private keys function within blockchain transactions involves several steps:
1. Generating a Key Pair
When you create a cryptocurrency wallet, it automatically generates two cryptographic keys: a public key and a private key. The public key acts as an address where others can send you funds—think of it as an email address for receiving money—while the private key remains secret with you.
2. Signing Transactions
To send cryptocurrencies from your wallet, you need to sign the transaction using your private key. This process creates a unique digital signature that proves ownership without revealing the actual private key itself.
3. Verification by Network Nodes
Once signed, the transaction is broadcasted across the network (like Bitcoin or Ethereum). Network nodes verify that the signature matches with the sender’s public key—confirming authenticity—and then add it to the blockchain ledger if valid.
This cryptographic process ensures both security and integrity: only someone with access to the correct private key can authorize spending from an account, preventing unauthorized transactions.
Why Are Private Keys Critical for Digital Asset Security?
Private keys are at the core of securing digital assets because they provide proof of ownership and authorization rights within decentralized systems:
- Confidentiality: Since anyone with access to this secret code can control associated funds, safeguarding it is paramount.
- Irreversibility: Unlike traditional banking systems where errors might be rectified easily, losing access to your private keys typically means losing all control over those assets permanently.
- Security Risks: If exposed through hacking attempts like phishing or malware attacks, malicious actors could drain accounts instantly.
Because these risks are so significant, users often employ various methods such as hardware wallets or encrypted backups to protect their keys effectively.
Types of Private Keys Used in Cryptocurrency Wallets
There are different formats for storing and managing private keys depending on user needs:
- Hexadecimal Strings: Long strings composed solely of numbers 0–9 and letters A–F.
- Wallet Files (e.g., .json files): Encrypted files containing encrypted versions of keys used by software wallets.
- Hardware Wallets: Physical devices like Ledger Nano S/X or Trezor store private keys offline for enhanced security.
Each method offers varying levels of convenience versus security; hardware wallets are generally considered most secure against online threats because they keep keys isolated from internet-connected devices.
Recent Developments in Private Key Management
The landscape around managing crypto-private keys continues evolving rapidly due to technological advancements:
Hardware Wallets Advancements
Devices such as Ledger Nano X have improved user experience while maintaining high-security standards by storing sensitive data offline—a practice known as cold storage—which significantly reduces hacking risks.
Multi-Signature Wallets
Multi-signature (multi-sig) setups require multiple independent signatures before executing transactions—adding layers of approval that prevent single points-of-failure or theft if one device gets compromised.
Quantum Computing Concerns
Emerging quantum computing technology poses potential threats since current cryptography may become vulnerable under powerful quantum algorithms. Researchers are actively developing post-quantum cryptography solutions designed specifically for resisting such attacks without compromising performance today’s systems rely upon.
Regulatory Focus & Industry Standards
As governments worldwide implement regulations around cryptocurrencies’ custody practices—including how users should securely manage their private keys—the industry sees increased adoption of standardized protocols emphasizing secure storage solutions like hardware wallets combined with best practices for backup procedures.
Risks Associated With Private Keys
Despite their importance in securing digital assets, mishandling or exposure poses serious dangers:
Loss Due To Forgetfulness or Damage: Losing physical copies (like paper backups) means permanent loss unless properly stored elsewhere.
Theft Through Phishing & Malware Attacks: Attackers often trick users into revealing their secrets via fake websites (“phishing”) or infecting devices with malware designed specifically for stealing keystrokes or clipboard data containing sensitive information.
Regulatory Non-compliance Risks: Failing to follow proper management procedures may lead not only to financial loss but also legal consequences depending on jurisdictional requirements.
Best Practices For Managing Your Private Keys Safely
To minimize risks associated with handling crypto-private keys:
- Use hardware wallets whenever possible—they store secrets offline away from internet vulnerabilities.
- Create multiple encrypted backups stored securely in geographically separated locations.
- Never share/private reveal your seed phrases — avoid storing them digitally unless encrypted properly.
- Be cautious about phishing attempts; always verify URLs before entering sensitive information online.
- Keep software wallets updated regularly along with device firmware patches.
Staying informed about developments related to privacy-enhancing tools like multi-sig arrangements and advances against emerging threats such as quantum computing will help safeguard investments long-term while complying with evolving regulatory landscapes.
By understanding what exactly constitutes a private key—and adopting robust management strategies—you ensure better protection against thefts while maintaining full control over digital assets within decentralized ecosystems.
Keywords: cryptocurrency privacy tips | secure crypto storage | blockchain security best practices | managing crypto-privatekeys | multi-signature wallets | hardware wallet advantages
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
$JU/USDT just hit new ATH: $22
Road to $50
#cryptocurrency #blockchain #JU

Mrconfamm
2025-08-30 17:54
$JU Touch new ATH
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
Understanding Proof-of-Stake (PoS) as a Blockchain Consensus Mechanism
Blockchain technology relies on consensus mechanisms to validate transactions and maintain the integrity of the network. Among these, Proof-of-Stake (PoS) has gained significant attention as an energy-efficient alternative to traditional methods like Proof-of-Work (PoW). This article explores what PoS is, how it functions, its historical development, advantages, challenges, and recent trends shaping its future.
What Is Proof-of-Stake?
Proof-of-Stake is a consensus protocol that enables blockchain networks to agree on transaction validity without requiring extensive computational work. Unlike PoW systems—such as Bitcoin—that depend on miners solving complex mathematical puzzles using powerful hardware, PoS selects validators based on the amount of cryptocurrency they "stake" or lock up in the network. This stake acts as collateral; if validators act maliciously or fail to perform their duties properly, they risk losing their staked tokens.
The core idea behind PoS is that those who have a vested interest in maintaining the network's security are more likely to act honestly. By tying validator incentives directly to their holdings, PoS aims to promote trustworthiness while significantly reducing energy consumption.
How Does Proof-of-Stake Work?
The process of validating transactions and creating new blocks in a PoS system involves several key steps:
Validator Selection
Validators are chosen based on their stake—the amount of cryptocurrency they have committed to the network. Generally speaking, larger stakes increase the probability of being selected for block creation because they represent a higher economic commitment. This proportional selection incentivizes validators to behave honestly since malicious actions could jeopardize their own assets.
Randomized Block Creation
Once selected through probabilistic algorithms—often involving random number generators—the validator proceeds with creating a new block containing recent transactions. To ensure fairness and prevent predictability or manipulation in validator selection, many systems incorporate additional randomness factors into this process.
Rewards and Penalties
Successful validation results in rewards such as newly minted coins and transaction fees added to the blockchain's ledger. Conversely, if validators attempt double-spending attacks or fail to produce blocks when selected—known as "missed" validations—they face penalties called "slashing." Slashing involves reducing or forfeiting part of their staked tokens as punishment for misconduct.
Security Measures: Slashing Penalties
Slashing serves both as an incentive for honest participation and a deterrent against malicious behavior like double-spending or equivocation (creating conflicting blocks). These penalties help uphold network security by aligning validator interests with overall system health.
The Evolution of Proof-of-Stake: A Brief History
While conceptually proposed back in 2012 by cryptographer Daniel Bernstein—a pioneer known for his contributions across cryptography—the first notable implementation appeared with Tezos in 2017. Tezos introduced innovative governance features allowing token holders themselves to vote on protocol upgrades—a model that enhanced community participation within proof-based consensus mechanisms.
Ethereum’s transition from proof-of-work toward hybrid proof-of-stake via Ethereum 2.0 has been pivotal for mainstream adoption. Launched initially through its Beacon Chain in December 2020—and ongoing since then—Ethereum aims at improving scalability while drastically reducing energy consumption associated with mining activities.
Other projects like Cardano utilize Ouroboros—a rigorous academic-designed PoS algorithm—to achieve secure decentralization from inception. Meanwhile, Solana combines elements from both PoS and other protocols such as Proof-of-History (PoH), enabling high throughput suitable for decentralized applications demanding fast transaction speeds.
Advantages of Using Proof-of-Stake
One primary benefit of PoS over traditional proof-based methods is its superior energy efficiency; validators do not need massive computational power but only hold tokens relevant enough relative stakes for participation rights. As such:
- Lower Energy Consumption: Since no intensive calculations are required.
- Enhanced Scalability: Faster validation times facilitate higher transaction throughput.
- Decentralization Potential: When designed inclusively—with low barriers for entry—it can foster broader participation among users globally.
Additionally, staking often encourages long-term engagement by rewarding token holders who commit assets over time rather than short-term miners seeking quick profits.
Challenges Facing Proof-of-Stake Networks
Despite its advantages, PoS faces certain risks:
Centralization Risks
Large stakeholders may accumulate disproportionate influence over decision-making processes within networks—potentially leading toward centralization where few entities control significant portions of staking power unless measures are implemented carefully during design phases.
Security Concerns
While generally considered secure when properly implemented—including slashing safeguards—PoS networks remain vulnerable under specific attack vectors such as “51% attacks,” where an entity controlling more than half the total stake could manipulate outcomes temporarily.
Furthermore, issues like “Nothing at Stake”—where validators might support multiple competing chains without penalty—have prompted developers worldwide to develop additional security patches and protocols addressing these vulnerabilities effectively over time.
Recent Trends & Future Outlook
The shift towards proof-based consensus models continues shaping blockchain ecosystems globally:
Ethereum’s Transition: The move towards Ethereum 2.0’s hybrid model aims at achieving greater scalability while maintaining decentralization standards—a complex but promising evolution expected over upcoming years.
Regulatory Scrutiny: As institutional interest grows around cryptocurrencies employing staking mechanisms—for example via DeFi platforms—regulators worldwide are examining legal frameworks surrounding staking activities which could impact future adoption strategies.
Security Improvements: Ongoing research into mitigating vulnerabilities like Nothing at Stake has led developers toward implementing multi-layered security measures ensuring robustness against potential exploits.
Community Engagement & Governance: Many projects leverage token-holder voting rights embedded within protocols encouraging active community involvement—which fosters transparency but also raises questions about influence concentration among large stakeholders.
Why Understanding Proof-of-Stake Matters
For investors considering cryptocurrencies utilizing PoS algorithms—or developers designing next-generation blockchain solutions—it’s crucial understanding both benefits and limitations inherent within this mechanism:
- Recognizing how validator incentives align with network health helps assess long-term sustainability prospects;
- Being aware of centralization risks guides better governance structures;
- Monitoring ongoing developments ensures preparedness amidst evolving regulatory landscapes;4.. Appreciating technical nuances supports informed decision-making regarding project viability or investment potential.
By grasping these core aspects rooted deeply in cryptographic principles—and supported by real-world implementations—you can better navigate today’s rapidly changing blockchain environment grounded increasingly upon proof-based consensus models like Proof-of-Stake.
This overview provides clarity around what makes proof-of-stake an influential component within modern blockchain architecture—from foundational concepts through current trends—all essential knowledge whether you're an investor aiming for informed decisions or developer seeking innovative solutions rooted in proven technology principles


JCUSER-WVMdslBw
2025-05-22 04:42
Could you explain "Proof-of-Stake" (PoS) as a consensus mechanism?
Understanding Proof-of-Stake (PoS) as a Blockchain Consensus Mechanism
Blockchain technology relies on consensus mechanisms to validate transactions and maintain the integrity of the network. Among these, Proof-of-Stake (PoS) has gained significant attention as an energy-efficient alternative to traditional methods like Proof-of-Work (PoW). This article explores what PoS is, how it functions, its historical development, advantages, challenges, and recent trends shaping its future.
What Is Proof-of-Stake?
Proof-of-Stake is a consensus protocol that enables blockchain networks to agree on transaction validity without requiring extensive computational work. Unlike PoW systems—such as Bitcoin—that depend on miners solving complex mathematical puzzles using powerful hardware, PoS selects validators based on the amount of cryptocurrency they "stake" or lock up in the network. This stake acts as collateral; if validators act maliciously or fail to perform their duties properly, they risk losing their staked tokens.
The core idea behind PoS is that those who have a vested interest in maintaining the network's security are more likely to act honestly. By tying validator incentives directly to their holdings, PoS aims to promote trustworthiness while significantly reducing energy consumption.
How Does Proof-of-Stake Work?
The process of validating transactions and creating new blocks in a PoS system involves several key steps:
Validator Selection
Validators are chosen based on their stake—the amount of cryptocurrency they have committed to the network. Generally speaking, larger stakes increase the probability of being selected for block creation because they represent a higher economic commitment. This proportional selection incentivizes validators to behave honestly since malicious actions could jeopardize their own assets.
Randomized Block Creation
Once selected through probabilistic algorithms—often involving random number generators—the validator proceeds with creating a new block containing recent transactions. To ensure fairness and prevent predictability or manipulation in validator selection, many systems incorporate additional randomness factors into this process.
Rewards and Penalties
Successful validation results in rewards such as newly minted coins and transaction fees added to the blockchain's ledger. Conversely, if validators attempt double-spending attacks or fail to produce blocks when selected—known as "missed" validations—they face penalties called "slashing." Slashing involves reducing or forfeiting part of their staked tokens as punishment for misconduct.
Security Measures: Slashing Penalties
Slashing serves both as an incentive for honest participation and a deterrent against malicious behavior like double-spending or equivocation (creating conflicting blocks). These penalties help uphold network security by aligning validator interests with overall system health.
The Evolution of Proof-of-Stake: A Brief History
While conceptually proposed back in 2012 by cryptographer Daniel Bernstein—a pioneer known for his contributions across cryptography—the first notable implementation appeared with Tezos in 2017. Tezos introduced innovative governance features allowing token holders themselves to vote on protocol upgrades—a model that enhanced community participation within proof-based consensus mechanisms.
Ethereum’s transition from proof-of-work toward hybrid proof-of-stake via Ethereum 2.0 has been pivotal for mainstream adoption. Launched initially through its Beacon Chain in December 2020—and ongoing since then—Ethereum aims at improving scalability while drastically reducing energy consumption associated with mining activities.
Other projects like Cardano utilize Ouroboros—a rigorous academic-designed PoS algorithm—to achieve secure decentralization from inception. Meanwhile, Solana combines elements from both PoS and other protocols such as Proof-of-History (PoH), enabling high throughput suitable for decentralized applications demanding fast transaction speeds.
Advantages of Using Proof-of-Stake
One primary benefit of PoS over traditional proof-based methods is its superior energy efficiency; validators do not need massive computational power but only hold tokens relevant enough relative stakes for participation rights. As such:
- Lower Energy Consumption: Since no intensive calculations are required.
- Enhanced Scalability: Faster validation times facilitate higher transaction throughput.
- Decentralization Potential: When designed inclusively—with low barriers for entry—it can foster broader participation among users globally.
Additionally, staking often encourages long-term engagement by rewarding token holders who commit assets over time rather than short-term miners seeking quick profits.
Challenges Facing Proof-of-Stake Networks
Despite its advantages, PoS faces certain risks:
Centralization Risks
Large stakeholders may accumulate disproportionate influence over decision-making processes within networks—potentially leading toward centralization where few entities control significant portions of staking power unless measures are implemented carefully during design phases.
Security Concerns
While generally considered secure when properly implemented—including slashing safeguards—PoS networks remain vulnerable under specific attack vectors such as “51% attacks,” where an entity controlling more than half the total stake could manipulate outcomes temporarily.
Furthermore, issues like “Nothing at Stake”—where validators might support multiple competing chains without penalty—have prompted developers worldwide to develop additional security patches and protocols addressing these vulnerabilities effectively over time.
Recent Trends & Future Outlook
The shift towards proof-based consensus models continues shaping blockchain ecosystems globally:
Ethereum’s Transition: The move towards Ethereum 2.0’s hybrid model aims at achieving greater scalability while maintaining decentralization standards—a complex but promising evolution expected over upcoming years.
Regulatory Scrutiny: As institutional interest grows around cryptocurrencies employing staking mechanisms—for example via DeFi platforms—regulators worldwide are examining legal frameworks surrounding staking activities which could impact future adoption strategies.
Security Improvements: Ongoing research into mitigating vulnerabilities like Nothing at Stake has led developers toward implementing multi-layered security measures ensuring robustness against potential exploits.
Community Engagement & Governance: Many projects leverage token-holder voting rights embedded within protocols encouraging active community involvement—which fosters transparency but also raises questions about influence concentration among large stakeholders.
Why Understanding Proof-of-Stake Matters
For investors considering cryptocurrencies utilizing PoS algorithms—or developers designing next-generation blockchain solutions—it’s crucial understanding both benefits and limitations inherent within this mechanism:
- Recognizing how validator incentives align with network health helps assess long-term sustainability prospects;
- Being aware of centralization risks guides better governance structures;
- Monitoring ongoing developments ensures preparedness amidst evolving regulatory landscapes;4.. Appreciating technical nuances supports informed decision-making regarding project viability or investment potential.
By grasping these core aspects rooted deeply in cryptographic principles—and supported by real-world implementations—you can better navigate today’s rapidly changing blockchain environment grounded increasingly upon proof-based consensus models like Proof-of-Stake.
This overview provides clarity around what makes proof-of-stake an influential component within modern blockchain architecture—from foundational concepts through current trends—all essential knowledge whether you're an investor aiming for informed decisions or developer seeking innovative solutions rooted in proven technology principles
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
Understanding Blob-Carrying Transactions in Blockchain Sharding
Blockchain technology has revolutionized the way digital assets and data are transferred, stored, and verified. As the popularity of blockchain networks grows, so does the need for scalable solutions that can handle increasing transaction volumes without compromising security or decentralization. One promising approach to achieving this scalability is through sharding, a technique that divides a blockchain network into smaller, manageable segments called shards. Within this framework, blob-carrying transactions have emerged as an innovative method to optimize data processing and improve overall network efficiency.
What Are Blob-Carrying Transactions?
Blob-carrying transactions are specialized data structures designed to facilitate efficient transaction processing within sharded blockchain networks. Unlike traditional transactions that are verified individually by each node across the entire network, blob-carrying transactions package multiple small transactions into a single large "blob." This blob acts as a container holding numerous individual operations or data points.
The primary purpose of these blobs is to reduce verification overhead on individual nodes. Instead of verifying each small transaction separately—which can be time-consuming and resource-intensive—nodes verify larger blobs containing many transactions at once. This process significantly decreases latency and increases throughput, enabling the network to handle more users and higher transaction volumes without sacrificing security.
How Do Blob-Carrying Transactions Enhance Blockchain Scalability?
In traditional blockchain systems like Bitcoin or early versions of Ethereum, every node must validate every transaction directly. While this ensures high security levels through full validation, it also limits scalability because nodes become bottlenecks under heavy loads.
Sharding addresses this issue by dividing the network into smaller segments—each shard processes its own subset of transactions independently. However, managing communication between shards introduces complexity; verifying cross-shard interactions efficiently becomes challenging.
Blob-carrying transactions help mitigate these challenges by:
- Reducing Verification Load: By bundling multiple small transactions into one blob per shard, nodes only need to verify fewer large data structures instead of numerous tiny ones.
- Streamlining Data Transfer: Blobs simplify cross-shard communication since they encapsulate multiple operations in a single package.
- Improving Network Throughput: With less verification overhead per node and optimized data handling within shards, overall transaction processing speeds increase dramatically.
This approach aligns with modern demands for high-performance blockchains capable of supporting decentralized applications (dApps), DeFi platforms, NFTs marketplaces—and other use cases requiring rapid confirmation times at scale.
Recent Advances in Sharding Using Blob-Carrying Transactions
Blockchain projects worldwide have been actively exploring sharding techniques incorporating blob-based methods:
Ethereum 2.0's Sharding Implementation: Ethereum's transition from proof-of-work (PoW) to proof-of-stake (PoS) includes extensive sharding plans aimed at scaling its ecosystem sustainably. The Beacon Chain launched in December 2020 laid groundwork for future shard chains.
In September 2022, Ethereum activated its first phase of full sharding with the Shanghai hard fork—introducing parallel processing capabilities via shard chains that utilize blob-like structures for efficient validation.
Polkadot’s Interoperability Focus: Polkadot employs parachains—independent blockchains connected via relay chains—to facilitate seamless asset transfer across different networks.
Its architecture leverages sharded design principles where blobs enable quick cross-chain messaging while maintaining security guarantees.
Solana’s High Throughput Model: Solana adopts unique consensus mechanisms combining Proof-of-History (PoH) with Proof-of-Stake (PoS). It processes thousands of transactions per second using parallel execution similar to sharding concepts but optimized through innovative data structuring akin to blobs for batch validation purposes.
These developments demonstrate how integrating blob-like transactional models within sharded architectures can significantly enhance performance metrics such as throughput and latency while maintaining robust security standards essential for mainstream adoption.
Challenges Associated With Blob-Based Sharded Networks
Despite their advantages, implementing blob-carrying transactions within sharded systems presents several hurdles:
Security Concerns:
- Ensuring each shard remains secure against malicious actors is critical; if one shard becomes compromised due to inadequate validation protocols on blobs or faulty aggregation methods — it could threaten overall network integrity.
Interoperability Complexities:
- Facilitating smooth communication between different shards—or even disparate blockchains—is complex when relying on bundled transactional data like blobs because synchronization issues may arise if not managed properly.
User Experience Variability:
- As different shards may process batches differently or experience varying load levels during peak times—a user might notice inconsistent confirmation times depending on which part of the network their transaction interacts with.
Regulatory Considerations:
- As blockchain adoption expands into regulated sectors such as finance or healthcare—with strict compliance requirements—the design choices around batching mechanisms like blobs must align with legal standards concerning transparency and auditability.
Addressing these challenges requires ongoing research focused on enhancing cryptographic proofs associated with batch validations while developing standardized protocols ensuring interoperability without sacrificing decentralization principles.
The Future Role Of Blob-Carrying Transactions in Blockchain Ecosystems
As blockchain technology continues evolving towards greater scalability solutions—including Layer 2 rollups and other off-chain methods—blob-based approaches will likely remain integral components within broader architectural frameworks aimed at optimizing performance without compromising trustlessness or censorship resistance.
Furthermore:
- They will play vital roles in enabling real-time applications such as decentralized exchanges (DEXs), gaming platforms requiring rapid state updates,
- Supporting enterprise-grade solutions where high throughput combined with privacy-preserving features is necessary,
- And facilitating interoperability initiatives among diverse ecosystems aiming toward unified multi-chain environments.
By improving how large datasets are packaged and validated efficiently across distributed ledgers—a core function served by blob-carrying transactions—they contribute substantially toward realizing scalable decentralized infrastructures suitable for mainstream adoption.
Key Takeaways About Blob-Carrying Transactions
To summarize:
- They bundle multiple small operations into larger "blobs" reducing verification overhead,
- Play an essential role in scaling efforts like Ethereum's upcoming upgrades,
- Enable faster cross-shard communication crucial for complex dApps,
- Present ongoing challenges related to security assurance & interoperability,
- Will continue shaping future multi-chain ecosystems aiming for high performance alongside robust decentralization standards.
Understanding how these advanced transactional techniques fit within broader scaling strategies provides valuable insights into building resilient yet efficient blockchain networks capable of supporting tomorrow’s digital economy needs.
Keywords & Semantic Terms Used:
Blockchain scalability | Sharded blockchain | Transaction batching | Cross-shard communication | Ethereum 2.0 | Polkadot parachains | Solana throughput | Distributed ledger technology | Decentralized applications (dApps) | Blockchain interoperability


kai
2025-05-14 12:35
What role do blob-carrying transactions play in sharding?
Understanding Blob-Carrying Transactions in Blockchain Sharding
Blockchain technology has revolutionized the way digital assets and data are transferred, stored, and verified. As the popularity of blockchain networks grows, so does the need for scalable solutions that can handle increasing transaction volumes without compromising security or decentralization. One promising approach to achieving this scalability is through sharding, a technique that divides a blockchain network into smaller, manageable segments called shards. Within this framework, blob-carrying transactions have emerged as an innovative method to optimize data processing and improve overall network efficiency.
What Are Blob-Carrying Transactions?
Blob-carrying transactions are specialized data structures designed to facilitate efficient transaction processing within sharded blockchain networks. Unlike traditional transactions that are verified individually by each node across the entire network, blob-carrying transactions package multiple small transactions into a single large "blob." This blob acts as a container holding numerous individual operations or data points.
The primary purpose of these blobs is to reduce verification overhead on individual nodes. Instead of verifying each small transaction separately—which can be time-consuming and resource-intensive—nodes verify larger blobs containing many transactions at once. This process significantly decreases latency and increases throughput, enabling the network to handle more users and higher transaction volumes without sacrificing security.
How Do Blob-Carrying Transactions Enhance Blockchain Scalability?
In traditional blockchain systems like Bitcoin or early versions of Ethereum, every node must validate every transaction directly. While this ensures high security levels through full validation, it also limits scalability because nodes become bottlenecks under heavy loads.
Sharding addresses this issue by dividing the network into smaller segments—each shard processes its own subset of transactions independently. However, managing communication between shards introduces complexity; verifying cross-shard interactions efficiently becomes challenging.
Blob-carrying transactions help mitigate these challenges by:
- Reducing Verification Load: By bundling multiple small transactions into one blob per shard, nodes only need to verify fewer large data structures instead of numerous tiny ones.
- Streamlining Data Transfer: Blobs simplify cross-shard communication since they encapsulate multiple operations in a single package.
- Improving Network Throughput: With less verification overhead per node and optimized data handling within shards, overall transaction processing speeds increase dramatically.
This approach aligns with modern demands for high-performance blockchains capable of supporting decentralized applications (dApps), DeFi platforms, NFTs marketplaces—and other use cases requiring rapid confirmation times at scale.
Recent Advances in Sharding Using Blob-Carrying Transactions
Blockchain projects worldwide have been actively exploring sharding techniques incorporating blob-based methods:
Ethereum 2.0's Sharding Implementation: Ethereum's transition from proof-of-work (PoW) to proof-of-stake (PoS) includes extensive sharding plans aimed at scaling its ecosystem sustainably. The Beacon Chain launched in December 2020 laid groundwork for future shard chains.
In September 2022, Ethereum activated its first phase of full sharding with the Shanghai hard fork—introducing parallel processing capabilities via shard chains that utilize blob-like structures for efficient validation.
Polkadot’s Interoperability Focus: Polkadot employs parachains—independent blockchains connected via relay chains—to facilitate seamless asset transfer across different networks.
Its architecture leverages sharded design principles where blobs enable quick cross-chain messaging while maintaining security guarantees.
Solana’s High Throughput Model: Solana adopts unique consensus mechanisms combining Proof-of-History (PoH) with Proof-of-Stake (PoS). It processes thousands of transactions per second using parallel execution similar to sharding concepts but optimized through innovative data structuring akin to blobs for batch validation purposes.
These developments demonstrate how integrating blob-like transactional models within sharded architectures can significantly enhance performance metrics such as throughput and latency while maintaining robust security standards essential for mainstream adoption.
Challenges Associated With Blob-Based Sharded Networks
Despite their advantages, implementing blob-carrying transactions within sharded systems presents several hurdles:
Security Concerns:
- Ensuring each shard remains secure against malicious actors is critical; if one shard becomes compromised due to inadequate validation protocols on blobs or faulty aggregation methods — it could threaten overall network integrity.
Interoperability Complexities:
- Facilitating smooth communication between different shards—or even disparate blockchains—is complex when relying on bundled transactional data like blobs because synchronization issues may arise if not managed properly.
User Experience Variability:
- As different shards may process batches differently or experience varying load levels during peak times—a user might notice inconsistent confirmation times depending on which part of the network their transaction interacts with.
Regulatory Considerations:
- As blockchain adoption expands into regulated sectors such as finance or healthcare—with strict compliance requirements—the design choices around batching mechanisms like blobs must align with legal standards concerning transparency and auditability.
Addressing these challenges requires ongoing research focused on enhancing cryptographic proofs associated with batch validations while developing standardized protocols ensuring interoperability without sacrificing decentralization principles.
The Future Role Of Blob-Carrying Transactions in Blockchain Ecosystems
As blockchain technology continues evolving towards greater scalability solutions—including Layer 2 rollups and other off-chain methods—blob-based approaches will likely remain integral components within broader architectural frameworks aimed at optimizing performance without compromising trustlessness or censorship resistance.
Furthermore:
- They will play vital roles in enabling real-time applications such as decentralized exchanges (DEXs), gaming platforms requiring rapid state updates,
- Supporting enterprise-grade solutions where high throughput combined with privacy-preserving features is necessary,
- And facilitating interoperability initiatives among diverse ecosystems aiming toward unified multi-chain environments.
By improving how large datasets are packaged and validated efficiently across distributed ledgers—a core function served by blob-carrying transactions—they contribute substantially toward realizing scalable decentralized infrastructures suitable for mainstream adoption.
Key Takeaways About Blob-Carrying Transactions
To summarize:
- They bundle multiple small operations into larger "blobs" reducing verification overhead,
- Play an essential role in scaling efforts like Ethereum's upcoming upgrades,
- Enable faster cross-shard communication crucial for complex dApps,
- Present ongoing challenges related to security assurance & interoperability,
- Will continue shaping future multi-chain ecosystems aiming for high performance alongside robust decentralization standards.
Understanding how these advanced transactional techniques fit within broader scaling strategies provides valuable insights into building resilient yet efficient blockchain networks capable of supporting tomorrow’s digital economy needs.
Keywords & Semantic Terms Used:
Blockchain scalability | Sharded blockchain | Transaction batching | Cross-shard communication | Ethereum 2.0 | Polkadot parachains | Solana throughput | Distributed ledger technology | Decentralized applications (dApps) | Blockchain interoperability
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
Today’s Top Gainers:
$AITP/USDT: 129%
$VEL/USDT: 124%$PYTH/USDT : 80%
$JU Token is close to reach $22 a new ATH
#cryptocurrency #blockchain #finance


Mrconfamm
2025-08-29 07:37
Market Daily Report
免責聲明:含第三方內容,非財務建議。
詳見《條款和條件》
